-
Georgia Tech releases 2015 Emerging Cyber Threats Report
In its latest Emerging Cyber Threats Report, Georgia Tech warns about loss of privacy; abuse of trust between users and machines; attacks against the mobile ecosystem; rogue insiders; and the increasing involvement of cyberspace in nation-state conflicts.
-
-
Surge in cyberattacks drives growth in cybersecurity insurance
More than 3,000 American businesses were hacked in 2013, many of them small and mid-size firms without cybersecurity insurance. That surge in cyberattacks has led to a growing cybersecurity industry, with firms offering products and solutions to secure network systems. Insurance companies are also claiming their stake in the booming industry. Today, roughly fifty U.S. companies offer cybersecurity insurance. American businesses will spend up to $2 billion on cyber-insurance premiums this year, a 67 percent increase from the $1.2 billion spent in 2013.
-
-
State, local governments aim to strengthen cybersecurity staff despite shrinking budgets
Due to increased cyberattacks on state and local government servers, many leaders are looking to strengthen the cybersecurity staff on their payrolls. Lower levels of government are also worried about cybercrime due to the large amounts of personal and confidential data that they store. Demand for cybersecurity experts is more than double the workplace demand for IT specialists.
-
-
Virginia welcomes cybersecurity start-ups to a state-backed business accelerator
Earlier this week, MACH37, a business accelerator for cybersecurity start-ups in Virginia, welcomed a new group of companies one year after it was launched to help establish the state as a hub for cybersecurity firms. The three-month program, funded with state money, offers a $50,000 investment and access to a network of mentors to companies that can turn their ideas into viable businesses.
-
-
Demand for cyberattack insurance grows, but challenges remain
The surge in cyberattacks against the private sector and critical infrastructure has led to a growth in demand for cyber insurance; yet most insurers are unable properly to assess their clients’ cyber risk, let alone issue the appropriate pricing for their cyber coverage.Insurers which traditionally handle risks like weather disasters and fires, are now rushing to gain expertise in cyber technology.On average, a $1 million cyber coverage could cost $20,000 to $25,000.
-
-
Pennsylvania cybersecurity group takes down international criminal network
Over the past month, a coalition of cybersecurity forces in Pittsburgh, Pennsylvania made of regional FBI officers and members of Carnegie Mellon University’s CERT cyberteam, took down the Gameover Zeus cyber theft network, which had employed data ransom and theft schemes. The criminal group was able to snatch funds up to seven figures from owners’ bank accounts.
-
-
Squiggly lines may be the future of password security
As more people use smart phones or tablets to pay bills, make purchases, store personal information, and even control access to their houses, the need for robust password security has become more critical than ever. A new study shows that free-form gestures — sweeping fingers in shapes across the screen of a smart phone or tablet — can be used to unlock phones and grant access to apps. These gestures are less likely than traditional typed passwords or newer “connect-the-dots” grid exercises to be observed and reproduced by “shoulder surfers” who spy on users to gain unauthorized access.
-
-
Develop tool to make the Internet of Things safer
There is a big push to create the so-called Internet of Things, where all devices are connected and communicate with one another. As a result, embedded systems — small computer systems built around microcontrollers — are becoming more common. They remain vulnerable, however, to security breaches. Some examples of devices that may be hackable: medical devices, cars, cell phones and smart grid technology. Computer scientists have developed a tool that allows hardware designers and system builders to test security- a first for the field.
-
-
Future cyberattacks to cause more trouble than Heartbleed
Many of the future cyberattacks could take advantage of vulnerabilities similar to Heartbleed, a major Internet security flaw which allows attackers to gain access to encrypted passwords, credit card details, and other data on trusted Web sites including Facebook, Gmail, Instagram, and Pinterest. A new report said that hackers could soon use similar holes in computer security to shut down energy grids, disrupt public services, and steal vast amounts of private data worth billions of dollars, unless institutions take measures today to ready themselves against future Heartbleed-like threats.
-
-
Snowden revelations spur a surge in encrypted e-mail services
The Edward Snowden revelations about National Security Agency(N.S.A) surveillance programs have fueled a surge of new e-mail encryption services. “A lot of people were upset with those revelations, and that coalesced into this effort,” said the co-developer of a new encrypted e-mail service which launched last Friday. The company notes that its servers are based in Switzerland, making it more difficult for U.S. law enforcement to reach them.
-
-
Cryptolocker has you between a back-up and a hard place
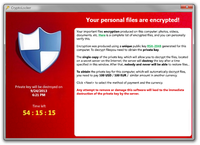
Cryptolocker, a particularly vicious form of malware that first appeared in September 2013, is a game-changer. After getting into your computer, it will encrypt all your data files, from your word documents to your photos, videos, and PDFs. It will then ask for a ransom of around $300 or 0.5 bitcoins to get them back. It has been one of the most commented developments in computer security circles in recent times, and copycats are appearing. The criminals are netting tens or hundreds of millions in ransoms, and at least some of the ill-gotten gains secured from Cryptolocker are likely to be reinvested. The criminals behind it will likely pay for access to bigger botnets to reach a wider base of victims. Future versions of the virus will in all likelihood be more prevalent and will extend across other platforms, like smartphones and tablets.
-
-
Black markets for hackers increasingly sophisticated, specialized, and maturing
Black and gray markets for computer hacking tools, services and byproducts such as stolen credit card numbers continue to expand, creating an increasing threat to businesses, governments and individuals, according to a new study. One dramatic example is the December 2013 breach of retail giant Target, in which data from approximately forty million credit cards and 70 million user accounts was hijacked. Within days, that data appeared — available for purchase — on black market Web sites.
-
-
New tool makes scanning the Internet for illegal images possible
Researchers have developed a system that makes it possible to scan traffic on the Internet for illegal photographs. The system can, for example, help trace child pornography on the Internet without infringing on the privacy of Internet users. Internet service providers could use the tool to keep their network “clean.”
-
-
Software spots malicious behavior by apps
Last year at the end of July the Russian software company Doctor Web detected several malicious apps in the app store Google Play. Downloaded on a smartphone, the malware installed — without the permission of the user — additional programs which sent expensive text messages to premium services. German computer scientists have now developed software which can discover such malicious apps already in the app store. The software detects pieces of code where the app accesses sensitive data and where data is sent from the mobile device.
-
-
Biometric security for mobile devices becoming mainstream
Biometric security such as fingerprint, face, and voice recognition is set to hit the mainstream as global technology companies market the systems as convenient and easy to use. The latest biometric technologies are not without their security issues, but they are marketed as more convenient than traditional methods rather than more secure, and encourage adoption by people who currently do not have any security on their phone at all.
-
- All
- Regional
- Water
- Biometrics
- Borders/Immig
- Business
- Cybersecurity
- Detection
- Disasters
- Government
- Infrastructure
- International
- Public health
- Public Safety
- Communication interoperabillity
- Emergency services
- Emergency medical services
- Fire
- First response
- IEDs
- Law Enforcement
- Law Enforcement Technology
- Military technology
- Nonlethal weapons
- Nuclear weapons
- Personal protection equipment
- Police
- Notification /alert systems
- Situational awareness
- Weapons systems
- Sci-Tech
- Sector Reports
- Surveillance
- Transportation
Advertising & Marketing: advertise@newswirepubs.com
Editorial: editor@newswirepubs.com
General: info@newswirepubs.com
2010-2011 © News Wire Publications, LLC News Wire Publications, LLC
220 Old Country Road | Suite 200 | Mineola | New York | 11501
Permissions and Policies
Editorial: editor@newswirepubs.com
General: info@newswirepubs.com
2010-2011 © News Wire Publications, LLC News Wire Publications, LLC
220 Old Country Road | Suite 200 | Mineola | New York | 11501
Permissions and Policies
