-
Young women’s warning to other women: Don’t be fooled by ISIS
A young woman who converted to Islam after being drawn to ISIS on social media has publicly warned other girls about how the jihadist group uses social media to reach vulnerable individuals such as herself. Her mother called the national hotline and the French police was able to intervene before the two women left for Syria. The young woman has since joined other youngest girls in France’s deradicalization program.
-
-
Mining social media improves disaster response efforts
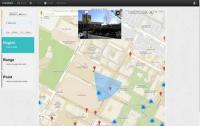
Leveraging publicly available social media posts could help disaster response agencies quickly identify impacted areas in need of assistance, according to a team of researchers. By analyzing the September 2013 Colorado floods, researchers showed that a combination of remote sensing, Twitter and Flickr data could be used to identify flooded areas.
-
-
SplashData releases annual “Worst Passwords” list -- “123456” maintains top spot

SplashData has announced its annual list of the twenty-five most common passwords found on the Internet — thus making them the “Worst Passwords” that will expose anybody to being hacked or having their identities stolen. The 2014 list of worst passwords demonstrates the importance of keeping names, simple numeric patterns, sports, and swear words out of your passwords. In this year’s report – the company’s fourth annual report — compiled from more than 3.3 million leaked passwords during the year, “123456”and “password” continue to hold the top two spots that they have held each year since the first list in 2011. Other passwords in the top 10 include “qwerty,” “dragon,” and “football.”
-
-
Cyberattack on Ukraine grid: here’s how it worked and perhaps why it was done
On 23 December 2015, two days before Christmas, the power grid in the Ivano-Frankivsk region of Ukraine went down for a reported six hours, leaving about half the homes in the region with a population of 1.4 million without power. Because of its success, the incident has sent shock waves through cybersecurity circles. Could this happen in the West? In short, yes. This incident underscores the need for diligence and the increased effort in cybersecurity that we are seeing in the government and private sectors. The continuously increasing dependence on the power grid is driving the need for cybersecurity to be part of the design of all new systems.
-
-
Cloud security reaches silicon
In the last ten years, computer security researchers have shown that malicious hackers don’t need to see your data in order to steal your data. From the pattern in which your computer accesses its memory banks, adversaries can infer a shocking amount about what’s stored there. The risk of such attacks is particularly acute in the cloud, where you have no control over whose applications are sharing server space with yours. An antagonist could load up multiple cloud servers with small programs that do nothing but spy on other people’s data. System for defending against memory-access attacks is being implemented in chips.
-
-
Optical illusions which fool computer vision raise security concerns

Computers are learning to recognize objects with near-human ability. But researchers have found that computers, like humans, can be fooled by optical illusions, which raises security concerns and opens new avenues for research in computer vision
-
-
Family of ISIS victim sues Twitter for enabling terrorism
The family of Lloyd “Carl” Fields Jr., who was killed last year in an attack in Amman, the capital of Jordan in an ISIS shooting, is suing Twitter, claiming the network has not done enough about the spread of the group’s deadly reach. The complaint claims that the shooting might never have happened had Twitter not existed.
-
-
Teenage hacker breaks into personal e-mail of James Clapper, director of national intelligence

A teenage hacker who, in October, broke into the personal e-mail account of John Brennan, the director of the Central Intelligence Agency, has now broken into the personal accounts of James Clapper, director of national intelligence. The high school student he managed to fool Verizon into giving him access to Brennan’s account.
-
-
U.S. assisting Ukraine investigate 23 December cyberattack on power grid

The United States is helping Ukraine investigate last month’s cyberattack last month which disrupted the country’s power grid and left some 80,000 customers without power. Experts say that the 23 December attack against western Ukraine’s Prykarpattyaoblenergo utility was the first known power outage caused by a cyberattack.
-
-
World leaders urged to oppose encryption back doors
In an open letter made public on Monday, nearly 200 Internet and digital rights leaders and experts, companies, and organizations are calling on the Obama administration and other world leaders to reject efforts to create “back doors” to encryption. “Encryption tools, technologies, and services are essential to protect against harm and to shield our digital infrastructure and personal communications from unauthorized access,” the letter states.
-
-
Administration tries to harness Silicon Valley’s talent for fight against ISIS
Senior administration intelligence officials are meeting today (Friday) with Silicon Valley’s major technology firms — companies including Facebook, Twitter, Apple, Microsoft, YouTube , LinkedIn, Dropbox, and others — in an effort to recruit them and their technological know-how in the fight against radicalization and terrorism.
-
-
Kaplan launches cybersecurity education company
Education provider Kaplan announced Wednesday that it has created a 12-person spin-off, split from a separate sister company called Cybervista, to offer Web-based cybersecurity courses. The creation of this new cybersecurity unit is an indication that the private sector is aware of, and trying to benefit from, the shortage of qualified security employees.
-
-
Tool improves government computer network security

Government agencies, along with state and local governments, could receive a helping hand from a computer network security tool developed by computer scientists and engineers at DOE’s Lawrence Livermore National Laboratory. The LLNL software-based technology, known as the Network Mapping System (NeMS), does not allow a rogue computer which has gained access to a computer network to use a company’s virus protection systemd. The goal is to uncover any unauthorized devices to ensure a company is not at risk.
-
-
Jihadi cyberattacks; ISIS’s sex slaves; Iran’s missile test

Hackers affiliated with the Jihadist group have been developing the capabilities to attack U.S. government and civilian targets, and such targets in other countries; Theologians working with ISIS have issued detailed and specific ruling on women slaves – explaining when “owners” of these women can have sex with them and who else among ISIS members may be entitled for sex services from enslaved women; On 26 December, the Iranian navy fired several rockets near three Western warships in the Gulf of Hormuz.
-
-
Making mobile health more secure

With Internet-connected medical technology and digitized health records on the rise, cybersecurity is a growing concern for patients and hospitals alike. For example, a patient’s insulin pump may accept dosage instructions from unauthorized smartphones that have been infected with malicious software, or a patient’s fertility-tracking app could expose itself to nearby strangers by probing for a Bluetooth device to connect with. One research team is taking a holistic approach to strengthening the medical system’s security — from the computer networks that support hospitals, to the cloud, to the smart phone in your pocket.
-
More headlines
The long view
States Rush to Combat AI Threat to Elections
This year’s presidential election will be the first since generative AI became widely available. That’s raising fears that millions of voters could be deceived by a barrage of political deepfakes. Congress has done little to address the issue, but states are moving aggressively to respond — though questions remain about how effective any new measures to combat AI-created disinformation will be.
Ransomware Attacks: Death Threats, Endangered Patients and Millions of Dollars in Damages
A ransomware attack on Change Healthcare, a company that processes 15 billion health care transactions annually and deals with 1 in 3 patient records in the United States, is continuing to cause massive disruptions nearly three weeks later. The incident, which started on February 21, has been called the “most significant cyberattack on the U.S. health care system” by the American Hospital Association. It is just the latest example of an increasing trend.
Chinese Government Hackers Targeted Critics of China, U.S. Businesses and Politicians
An indictment was unsealed Monday charging seven nationals of the People’s Republic of China (PRC) with conspiracy to commit computer intrusions and conspiracy to commit wire fraud for their involvement in a PRC-based hacking group that spent approximately 14 years targeting U.S. and foreign critics, businesses, and political officials in furtherance of the PRC’s economic espionage and foreign intelligence objectives.
Autonomous Vehicle Technology Vulnerable to Road Object Spoofing and Vanishing Attacks
Researchers have demonstrated the potentially hazardous vulnerabilities associated with the technology called LiDAR, or Light Detection and Ranging, many autonomous vehicles use to navigate streets, roads and highways. The researchers have shown how to use lasers to fool LiDAR into “seeing” objects that are not present and missing those that are – deficiencies that can cause unwarranted and unsafe braking or collisions.
Tantalizing Method to Study Cyberdeterrence
Tantalus is unlike most war games because it is experimental instead of experiential — the immersive game differs by overlapping scientific rigor and quantitative assessment methods with the experimental sciences, and experimental war gaming provides insightful data for real-world cyberattacks.
