-
Smartphones turned into secure and versatile keys
It is already possible to open doors using an app — but we are a long way from seeing widespread acceptance of this in the market; now, researchers have developed a piece of software that will make the technology even more secure and versatile
-
-
Secure communication technology overcomes lack of trust between communicating parties
Many scenarios in business and communication require that two parties share information without either being sure whether they can trust the other; examples include secure auctions and identification at ATM machines; researchers say that exploiting the strange properties of the quantum world could be the answer to dealing with such distrust
-
-
Louisiana parishes to encrypt police radio communication
First-responder agencies in Orleans, Jefferson, St. Bernard, and Plaquemines parishes in Louisiana will soon be encrypting all emergency radios, keeping emergency response chatter out of the ears of the public; the police says the encrypted communication is needed in order to keep criminals from gaining information on police by listening to scanners, but a police union and crime-prevention groups are worried that the encrypted system would prevent the media from monitoring police activity, and hobble neighborhood watch organizations from keeping their neighborhoods safe
-
-
Social networks helping during disasters
In 2005, when Katrina hit New Orleans, social networking Web sites were not as popular or as informative as they are today. Facebook was only up for a year at that point and was still restricted to college students only; Twitter was not started until 2006, and most local governments did not use the Internet for daily updates and information; advancements in social networking Web sites and in technology made a big difference for victims of Sandy
-
-
Cybersecurity company using hackers own devices against them
A California cybersecurity start-up, marketing itself as a private cyber intelligence agency, works to identify foreign attackers who are attempting to steal corporate secrets; it does so by using the attackers’ own techniques and vulnerabilities against them; the company also collects data on hackers and tricks intruders into stealing false information
-
-
Expert show how to crack every common password in under six hours
GPU computing has improved considerably in recent years, and Jeremi Gosney, founder and CEO of Stricture Consulting Group, used a 25-GPU cluster that can run through 350 billion guesses per second to show how easy it would be to crack practically any password out there (easy, that is, if you can use a 25-GPU cluster )
-
-
New NIST report offers guidance in cryptographic key generation
Protecting sensitive electronic information in different situations requires different types of cryptographic algorithms, but ultimately they all depend on keys, the cryptographic equivalent of a password; a new publication from the National Institute of Standards and Technology (NIST) aims to help people secure their data with good keys no matter which algorithm they choose
-
-
Israel cyber security incubator program established by Ben-Gurion University of the Negev
Israel has been named one of the top three world leaders in the field of cyber security; approximately twenty-five Israeli information security firms have been acquired by multinational organizations, and Israeli companies are counted among the world’s leading IT security providers; Ben-Gurion University of the Negev (BGU) and its technology transfer company, BGN Technologies, will create Israel’s first cyber security incubator in Beer-Sheva
-
-
Huawei rejects U.S. “threat to national security” claims
In October the United States House Intelligence Committee issued a report warning U.S. companies against using two Chinese companies, Huawei and ZTE, for their telecommunication technology needs; the report said that the firms may be too close to China’s Communist Party and its military’ the report also suggested their products and services could pose a threat to the security of the United .States; Huawei vigorously disputes both claims
-
-
Quantum cryptography may soon go main stream
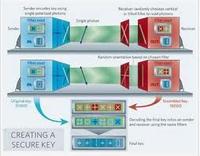
Researchers have perfected a technique that offers a less expensive way to ensure the security of high-speed fiber-optic cables, protecting communication networks from unauthorized snooping; this means that existing telecom networks can now be secured with this ultimate form of encryption
-
-
DARPA’s program to reveal backdoors, hidden malicious functionality in commercial IT devices

The scenario is one that information security experts dread: widespread dissemination of commercial technology which is secretly wired to function in unintended ways or even spy on its users; from this vantage point, mobile phones, network routers, computer work stations, and any other device hooked up to a network can provide a point of entry for an adversary; for the Department of Defense this issue is of great concern, and DARPA pland to do something about it
-
-
Pacemakers, other implanted devices, vulnerable to lethal attacks

IT experts reported that security flaws in pacemakers and defibrillators could be putting lives at risk; the experts say that many of these devices are not properly secured and therefore are vulnerable to hackers who may want to commit an act that could lead to multiple deaths
-
-
Social media as preventative method for infectious diseases
When it comes to stopping illness, social media posts and tweets may be just what the doctor ordered; researchers are studying whether a well-timed post from a public authority or trustworthy person could be as beneficial as flu shots, hand-washing, or sneezing into an elbow
-
-
DHS awards $23.6 million to fund development of new software analysis technology
DHS awarded a $23.6 million grant to the Morgridge Institute for Research at the University of Wisconsin-Madison to create the Software Assurance Marketplace, which, over the next five years, will work closely with developers of new software analysis technology and the open source community to advance the security of software; initial operating capabilities for the Software Assurance Marketplace will include the ability continuously to test up to 100 open-source software packages against five software assurance tools on eight platforms, including Macintosh, Linux, and Windows
-
-
New method to rid inboxes of unsolicited e-mail
Spam used to be text-based, but has recently turned high-tech, using layers of images to fool automatic filters; thanks to some sophisticated new cyber-sleuthing, researchers at are working toward a cure
-
More headlines
The long view
States Rush to Combat AI Threat to Elections
This year’s presidential election will be the first since generative AI became widely available. That’s raising fears that millions of voters could be deceived by a barrage of political deepfakes. Congress has done little to address the issue, but states are moving aggressively to respond — though questions remain about how effective any new measures to combat AI-created disinformation will be.
Ransomware Attacks: Death Threats, Endangered Patients and Millions of Dollars in Damages
A ransomware attack on Change Healthcare, a company that processes 15 billion health care transactions annually and deals with 1 in 3 patient records in the United States, is continuing to cause massive disruptions nearly three weeks later. The incident, which started on February 21, has been called the “most significant cyberattack on the U.S. health care system” by the American Hospital Association. It is just the latest example of an increasing trend.
Chinese Government Hackers Targeted Critics of China, U.S. Businesses and Politicians
An indictment was unsealed Monday charging seven nationals of the People’s Republic of China (PRC) with conspiracy to commit computer intrusions and conspiracy to commit wire fraud for their involvement in a PRC-based hacking group that spent approximately 14 years targeting U.S. and foreign critics, businesses, and political officials in furtherance of the PRC’s economic espionage and foreign intelligence objectives.
Autonomous Vehicle Technology Vulnerable to Road Object Spoofing and Vanishing Attacks
Researchers have demonstrated the potentially hazardous vulnerabilities associated with the technology called LiDAR, or Light Detection and Ranging, many autonomous vehicles use to navigate streets, roads and highways. The researchers have shown how to use lasers to fool LiDAR into “seeing” objects that are not present and missing those that are – deficiencies that can cause unwarranted and unsafe braking or collisions.
Tantalizing Method to Study Cyberdeterrence
Tantalus is unlike most war games because it is experimental instead of experiential — the immersive game differs by overlapping scientific rigor and quantitative assessment methods with the experimental sciences, and experimental war gaming provides insightful data for real-world cyberattacks.
