-
New program to educate next generation of U.S. cybersecurity specialists

University of Maryland and Northrop Grumman create a cybersecurity honors program for undergraduates; the program, Advanced Cybersecurity Experience for Students (ACES), will immerse undergraduate students in all aspects of the field to meet growing manpower needs in the nation and the State of Maryland
-
-
Veterans of Israel’s secretive Unit 8200 head many successful high-tech start-ups

Unit 8200 is Israel’s equivalent of the U.S. National Security Agency (NSA) or GCHQ in Britain; what sets the unit apart from its SIGINT counterparts in the United States and Europe is that it does almost all its research and development in-house; this means that, aside from interpreters and analysts, the unit is home to a huge cadre of engineers, technicians, and programmers; one result is that veterans of Unit 8200 have founded many of Israel’s successful high-tech start-ups
-
-
Experts: Flame represents a new level of state-sponsored cyber attacks
The latest cyber espionage malware, Flame, represents a new level of sophistication in state-sponsored cyberattacks; experts note that Flame circumvented anti-virus programs, and remained undetected between two and five years; one expert says: “[Flame] uses multiple exploit combinations so it is pretty significant that it hid itself, but maybe the best ones have not been discovered yet”; another expert says: “The failure to detect Flame means simplistic signature-based detection is obsolete”
-
-
QinetiQ North America to provide cybersecurity services to DOT
QinetiQ North America (QNA) was awarded a new task order by the Volpe National Transportation Systems Center to provide cybersecurity services to protect the U.S. transportation and control systems and critical infrastructure
-
-
NSA launches cyber operations academic program
The NSA has launched National Centers of Academic Excellence (CAE) in Cyber Operations Program; the program is intended to be a deeply technical, inter-disciplinary, higher education program grounded in the computer science (CS), computer engineering (CE), or electrical engineering (EE) disciplines, with extensive opportunities for hands-on applications via labs and exercises
-
-
DHS forced to release list terms it monitors on social media
Following a Freedom of Information Act (FOIA) request by the Electronic Privacy Information center (EPIC), DHS was forced to release its 2011 Analyst’s Desktop Binder; the binder, among other things, contains a list of words DHS uses as triggers of suspicious communication when the department’s analysts monitor social media
-
-
Malware intelligence system allow organizations to share threat information
As malware threats expand into new domains and increasingly focus on industrial espionage, researchers are launching a new tool to help battle the threats: a malware intelligence system which will help corporate and government security officials share information about the attacks they are fighting
-
-
How govt. can achieve IT savings, innovation
Innovative shifts in technology can springboard government into a new era of efficiency, effectiveness, and transparency; lawmakers urged to focus not only on technology infrastructure to achieve savings and efficiencies, but also consider how the government procures and delivers
-
-
SAIC Launches Inaugural Utah Cyber Defense Challenge and Symposium 2012

SAIC will lead a Utah statewide cyber competition and symposium designed to raise cyber awareness across government, academia, and industry; the Utah Cyber Defense Challenge and Symposium (UCDC) 2012, to be held 1 June
-
-
Execs offered cyber security degree track at NYU-Poly
Polytechnic Institute of New York University says that because defending institutional data against attack depends equally on cyber security experts as well as executives who command management and technical skills, it is introducing a management track to its master’s degree in cyber security; first classes begin this summer
-
-
Using Twitter to share information after a disaster
A new study shows how people used Twitter following the 2011 nuclear disaster in Japan, highlighting challenges for using the social media tool to share information; the study also indicates that social media have not changed what we communicate so much as how quickly we can disseminate it
-
-
Texas fights identity theft
Everything is bigger in Texas, including the number of instances of identity manipulation; according to an April report from ID Analytics, the cities of Beaumont and El Paso lead the nation in per-capita identity manipulation attempts
-
-
McAfee, Intel collaborate on protecting energy infrastructure

McAfee and Intel will collaborate on improving the protection of the world’s energy utilities, including generation, transmission, and distribution, from increased cyber attacks; the two companies have provided a blueprint for a comprehensive solution of multiple products which create layers of security and operate together without great complexity or without impacting availability
-
-
Self-adapting computer network that actively defends itself against hackers
Researchers are looking into the feasibility of building a computer network that could protect itself against online attackers by automatically changing its setup and configuration; the researchers will examine whether this type of adaptive cybersecurity, called moving-target defense, can be effective – and cost-effective
-
-
Travelers’ laptops infected through fake software updates in foreign hotel rooms
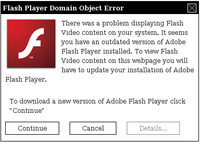
Recent analysis from the FBI and other government agencies demonstrates that malicious actors are targeting travelers abroad through pop-up windows while establishing an Internet connection in their hotel rooms
-
More headlines
The long view
States Rush to Combat AI Threat to Elections
This year’s presidential election will be the first since generative AI became widely available. That’s raising fears that millions of voters could be deceived by a barrage of political deepfakes. Congress has done little to address the issue, but states are moving aggressively to respond — though questions remain about how effective any new measures to combat AI-created disinformation will be.
Ransomware Attacks: Death Threats, Endangered Patients and Millions of Dollars in Damages
A ransomware attack on Change Healthcare, a company that processes 15 billion health care transactions annually and deals with 1 in 3 patient records in the United States, is continuing to cause massive disruptions nearly three weeks later. The incident, which started on February 21, has been called the “most significant cyberattack on the U.S. health care system” by the American Hospital Association. It is just the latest example of an increasing trend.
Chinese Government Hackers Targeted Critics of China, U.S. Businesses and Politicians
An indictment was unsealed Monday charging seven nationals of the People’s Republic of China (PRC) with conspiracy to commit computer intrusions and conspiracy to commit wire fraud for their involvement in a PRC-based hacking group that spent approximately 14 years targeting U.S. and foreign critics, businesses, and political officials in furtherance of the PRC’s economic espionage and foreign intelligence objectives.
Autonomous Vehicle Technology Vulnerable to Road Object Spoofing and Vanishing Attacks
Researchers have demonstrated the potentially hazardous vulnerabilities associated with the technology called LiDAR, or Light Detection and Ranging, many autonomous vehicles use to navigate streets, roads and highways. The researchers have shown how to use lasers to fool LiDAR into “seeing” objects that are not present and missing those that are – deficiencies that can cause unwarranted and unsafe braking or collisions.
Tantalizing Method to Study Cyberdeterrence
Tantalus is unlike most war games because it is experimental instead of experiential — the immersive game differs by overlapping scientific rigor and quantitative assessment methods with the experimental sciences, and experimental war gaming provides insightful data for real-world cyberattacks.
