-
Spotting and extracting relevant information from mountains of data
The term “Big Data” refers to a technology phenomenon that has arisen over the past thirty years. As computers have improved, growing storage and processing capacities have provided new and powerful ways to gain insight into the world by sifting through the infinite quantities of data available. This insight, discoverable in previously unseen patterns and trends within these phenomenally large data sets, can be hard to detect without new analytic tools that can comb through the information and highlight points of interest. Experts convene to address growing need for Big Data analysis tools.
-
-
DHS grant to fund technology for tracking mobile devices
The University Of Alabama at Birmingham(UAB) has been given a $583,000 grant from the Department of Homeland Securityto build a system for verifying the location history and chorological track of cell phones and smart phones, tablets, and other mobile devices. The system being built could also be used to eliminate contest fraud, verify the origin of sea food, and protect national security.
-
-
DNA sequencing a serious risk to privacy
The growing ease of DNA sequencing has led to enormous advancements in the scientific field. Through extensive networked databases, researchers can access genetic information to gain valuable knowledge about causative and preventative factors for disease, and identify new targets for future treatments. The wider availability of such information, however, also has a significant downside — the risk of revealing personal information. New study finds that new policies are needed to safeguard participants’ identity in genetic studies.
-
-
Google wants to limit law enforcement’s access to e-mails, users’ information
In 2012 Google received 16,407 requests for user data, which affected 31,072 users or accounts. More than half of the requests were accompanied with a subpoena, the others were not. Google is planning on lobbying Washington this year to persuade lawmakers that they should make it harder for law enforcement to gain access to e-mails and other digital messages.
-
-
New Hampshire bill would limit searches, expand expectation of privacy

New Hampshire State Representative Neal Kurk ® says state residents do not expect,when they throw something out in their trash or leave a drinking glass with their saliva on it at a public place, that law enforcement, insurance companies, or data miners would use the trash left behind to glean personally identifiable information.
-
-
Police depts. reviews policy on retaining data from license plate readers
License plate readers (LPRs) have been used more and more by law enforcement agencies across the United States, but as they gain popularity in law enforcement, they have become the subject of debate, and concern, in many local governments.
-
-
Unmanned vessel for continuous tracking of enemy submarines

DARPA looking for an unmanned naval vessel that can seek out and track quiet diesel submarines, forcing them to return to base and thus protecting friendly ships from attack
-
-
Kansas history says DHS opened his mail -- again
Grant Goodman, a retired professor at the University of Kansas, was shocked when he found out that DHS opened his mail in 2005, but now that it has happened again, he just wants to know why; CBP does not need a warrant or probable cause to check international mail or cargo
-
-
DARPA seeking surveillance technology to predict future behavior
DARPA has teamed up with scientists from Carnegie Mellon University to create an artificial intelligence system that can watch and predict what a person will “likely” do in the future, using specially programmed software designed to analyze various real-time video surveillance feeds; the system can automatically identify and notify officials if it recognized that an action is not permitted, detecting what is described as anomalous behaviors
-
-
Searching social media sources by geography
Geofeedia, has created a group of algorithms that can search multiple social media sources by geography in real time; the postings, pictures, and tweets that show up in the results of a search are geolocation-enabled, are free, and results can be streamed on a mobile device, computer, or tablet. Businesses may have to pay a fee for more intensive searches
-
-
CIA-commissioned climate change report outlines perils for U.S. national security
U.S. national security leaders believe that the accelerating pace of climate change will place severe strains on U.S. military and intelligence agencies in coming years; the reason, according the National Research Council, the U.S. top scientific research body: climate changes will trigger increasingly disruptive developments around the world; a 206-page National Research Council study, commissioned by the CIA and other U.S. intelligence services, concludes that states will fail, large populations subjected to famine, flood, or disease will migrate across international borders, and national and international agencies will not have the capacity or resources to cope with the resulting conflicts and crises
-
-
New cell phone surveillance method raises privacy concerns
The FBI is using a new method to access cell phone customer data,butthe American Civil Liberties Union (ACLU) contends that the method is overly invasive
-
-
Smart camera to describe what it sees -- and reason about what it cannot see
Army scouts are commonly tasked with covertly entering uncontrolled areas, setting up a temporary observation post, and then performing persistent surveillance for twenty-four hours or longer; what if instead of sending scouts on high-risk missions the military could deploy taskable smart cameras? A truly “smart” camera would be able to describe with words everything it sees and reason about what it cannot see
-
-
New app uses scattered public information to put together a digital footprint of individuals, organizations
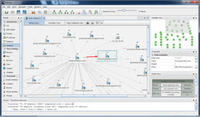
A new app application can collect scattered online clues to provide a picture of individuals or organizations; the application draws on public data sources in order to put together a graphical digital footprint
-
-
Scenario-based gaming exercise to improve intelligence analysis
Raytheon has created a scenario-based gaming exercise to study in depth the intelligence analyst’s tradecraft; the company says the goal is ultimately to help analysts produce the best intelligence products and streamline workflows
-
- All
- Regional
- Water
- Biometrics
- Borders/Immig
- Business
- Cybersecurity
- Detection
- Disasters
- Government
- Infrastructure
- International
- Public health
- Public Safety
- Communication interoperabillity
- Emergency services
- Emergency medical services
- Fire
- First response
- IEDs
- Law Enforcement
- Law Enforcement Technology
- Military technology
- Nonlethal weapons
- Nuclear weapons
- Personal protection equipment
- Police
- Notification /alert systems
- Situational awareness
- Weapons systems
- Sci-Tech
- Sector Reports
- Surveillance
- Transportation
Advertising & Marketing: advertise@newswirepubs.com
Editorial: editor@newswirepubs.com
General: info@newswirepubs.com
2010-2011 © News Wire Publications, LLC News Wire Publications, LLC
220 Old Country Road | Suite 200 | Mineola | New York | 11501
Permissions and Policies
Editorial: editor@newswirepubs.com
General: info@newswirepubs.com
2010-2011 © News Wire Publications, LLC News Wire Publications, LLC
220 Old Country Road | Suite 200 | Mineola | New York | 11501
Permissions and Policies
