CybersecurityCryptolocker has you between a back-up and a hard place
Cryptolocker, a particularly vicious form of malware that first appeared in September 2013, is a game-changer. After getting into your computer, it will encrypt all your data files, from your word documents to your photos, videos, and PDFs. It will then ask for a ransom of around $300 or 0.5 bitcoins to get them back. It has been one of the most commented developments in computer security circles in recent times, and copycats are appearing. The criminals are netting tens or hundreds of millions in ransoms, and at least some of the ill-gotten gains secured from Cryptolocker are likely to be reinvested. The criminals behind it will likely pay for access to bigger botnets to reach a wider base of victims. Future versions of the virus will in all likelihood be more prevalent and will extend across other platforms, like smartphones and tablets.
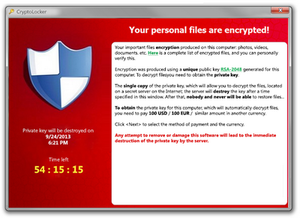
Cryptolocker encrypts your files, the demands ransom // Source: northeastern.edu
Cryptolocker, a particularly vicious form of malware that first appeared in September 2013, is a game-changer. After getting into your computer, it will encrypt all your data files, from your word documents to your photos, videos, and PDFs. It will then ask for a ransom of around $300 or 0.5 bitcoins to get them back. It has been one of the most commented developments in computer security circles in recent times, and copycats are appearing.
Criminals have been trying to make cryptoviruses of this kind work effectively for decades, but only now have they got it right. You can take some simple steps to protect yourself, but this threat is going to grow globally for some time.
Far from being a surprise, the arrival of Cryptolocker was easy to predict. I’ve taught cryptoviruses for more than ten years in my lectures, and others have been aware of the threat for nearly twenty years. But Cryptolocker is the first example of the technique working on a large scale and for a sustained period of time.
From the brightest brains to your desktop
Credit where credit is due: Cryptolocker is the work of one or more criminals, who are probably netting tens or hundreds of millions in ransoms, but the original concept was fully developed in the mid-1990s by Moti Yung, a cryptography researcher at Columbia University who now works for Google, and his Ph.D. student at the time, Adam Young.
Fortunately, criminals aren’t known for their love of academic papers so the cryptovirus proposed by Yung and Young went largely unnoticed outside the academic community for nearly twenty years.
In some ways that’s a good thing. We were spared from falling victim to this scam for a while. But on the other hand, if we’d paid more attention to these two brilliant researchers in the first place, we might have been better placed to have stopped or at least limited the damage Cryptolocker and similar ransomware has done and will undoubtedly inflict in the near future.
Until Cryptolocker, other criminals had tried in vain to produce a virus that could hold your files hostage until money exchanged hands. They were largely isolated attempts by individuals and most fell apart at the seams because the people behind them only had a passing knowledge of cryptography.
