-
Massive 2014 West Virginia chemical spill was preventable: CSB
The Chemical Safety Board’s (CSB) final report into the massive 2014 release by Freedom Industries of chemicals into the primary source of drinking water of Charleston, West Virginia, concludes that Freedom Industries failed to inspect or repair corroding tanks, and that as hazardous chemicals flowed into the Elk River, the water company and local authorities were unable effectively to communicate the looming risks to hundreds of thousands of affected residents, who were left without clean water for drinking, cooking, and bathing.
-
-
California's almond boom ramped up water use, consumed wetlands
Converting land in California to grow water-hungry almonds between 2007 and 2014 has led to a 27 percent annual increase in irrigation demands — despite the state’s historic drought. The expansion of almonds has also consumed 16,000 acres of wetlands and will likely put additional pressure on already stressed honeybee populations.
-
-
Judge questions whether Facebook is doing enough to deter terrorists from using its platform
A federal judge harshly criticized Facebook, admonishing the social media giant for not be doing enough to deter terrorists from using its platform. U.S. District Judge Nicholas Garaufis in Brooklyn, New York, also accused Kirkland & Ellis LLP, Facebook’s lawyers — who had sent a first-year associate to a hearing — of not taking seriously lawsuits which touch on important issues such as international terrorism and the murder of innocents. “I think it is outrageous, irresponsible, and insulting,” Garaufis told the attorney. The judge ordered the law firm to send a more senior lawyer to the next hearing on 28 September because he wanted to “talk to someone who talks to senior management at Facebook.”
-
-
Abnormalities found in drinking water in Texas’s Eagle Ford Shale region
Chemists studying well water quality in the Texas’s Eagle Ford Shale region found some abnormal chloride/bromide ratios, alongside evidence of dissolved gases and sporadic episodes of volatile organic compounds, all indicative of some contamination from industrial or agricultural activities in the area.
-
-
Radioactive wastewater enters Florida major aquifer after huge sinkhole opens up below fertilizer plant
At least 980 million liters of highly contaminated water — including radioactive substances – has leaked into one of Florida’s largest sources of drinking water. The leak was caused by a huge sinkhole which opened up beneath a fertilizer plant near Tampa. The sinkhole caused highly contaminated waste water to pass into an aquifer which supplies much of the state. The waste water contained phosphogypsum, a by-product of fertilizer production, which contains naturally occurring uranium and radium. the Floridan aquifer aquifer underlies all of Florida and extends into southern Alabama, Georgia, and South Carolina, supplying groundwater to the cities of Tallahassee, Jacksonville, Gainesville, Orlando, Daytona Beach, Tampa, and St Petersburg.
-
-
Muslim woman in Sweden quits job after being instructed to shake hands with male colleagues
A 20-year old Muslim woman in Helsingborg, Sweden has quit her job after being told she must shake hands with her male colleagues. She had told her fellow employees that she preferred not to shake hands with her male colleagues, and instead would rather put her hand on her heart and bow as a greeting. One of her male colleagues, however, took offense at her suggestion, complained to the school principal where she was working at the time, and the principal informed her that she must conform to the institution’s “core values” if she wanted to remain working there.
-
-
Cyber incidents’ cost not large compared with other business losses
The cost of a typical cyber breach to an American company is much less than generally estimated, providing one possible explanation for why companies do not invest more to improve computer security, according to a new study. Researchers found that the typical cost of a breach was about $200,000 and that most cyber events cost companies less than 0.4 percent of their annual revenues. The $200,000 cost was roughly equivalent to a typical company’s annual information security budget. Given that finding, the study’s author says that businesses “lack a strong incentive to increase their investment in data security and privacy protection.”
-
-
Climate change means land use will need to change to keep up with global food demand
Researchers warn that without significant improvements in technology, global crop yields are likely to fall in the areas currently used for production of the world’s three major cereal crops — wheat, maize, and rice — forcing production to move to new areas. This could lead to a major drop in productivity of these areas by 2050, along with a corresponding increase in potential productivity of many previously unused areas, pointing to a major shift in the map of global food production.
-
-
CBP MVSS border surveillance system: Another border program mired in delays
Political parties debate crucial immigration issues, including a call for a new border wall, but an essential component — frequently neglected in the run up to the November elections — is the efficacy of the Customs and Border Protection (CBP) contract acquisition and management process. What is frequently overlooked is the “business side” of CBP – but the business side of CBP is crucial to any immigration policy. CBP agents and officers finally are benefiting from the much-delayed delivery of the Integrated Fixed Tower (IFT) surveillance technology program, but the status of the Remote Video Surveillance Systems (RVSS) and Ultra-Light Aircraft Detection (ULAD) surveillance technology programs has not been ascertained. After many needless Office of Technology Innovation and Acquisition (OTIA) delays and problematic contract management decisions, both the MVSS program, along with the Mobile Surveillance Capabilities (MSC) program, now appear to be dead in the water.
-
-
“Great British Firewall”: U.K. plans firewall to protect industries, consumers
The GCHQ, U.K.’s surveillance agency, said it was planning to build a British firewall to offer protection against malicious hackers. GCHQ has developed cybersecurity systems the aim of which is to protect government sites and critical infrastructure, but the agency is now ready to offer its expertise to major private companies. “It’s possible to filter unwanted content or spam. It’s possible to filter offensive content. It’s technically possible to block malicious content,” GCHQ director said. “So, the question is: why aren’t we, the cybersecurity community, using this more widely? Well, we — in the U.K.— now are.”
-
-
Why Terrorism (Re)insurance Pools need to collaborate
Julian Enoizi, CEO of Pool Re, the U.K. government-backed terrorism pool, on Tuesday, 13 September, posted a note on the Pool Re’s Web site ahead of the 6 October Global Terrorism Risk Insurance Conference, which will take place in Canberra, Australia. “The terrorist threat is unprecedented and persistent, and our national interests are now threatened at home and overseas,” he wrote. “Terrorism is a global phenomenon and we need to face up to it with an internationally joined-up response involving innovation, creativity, and collaboration.”
-
-
AIR Worldwide expands its terrorism model globally
Catastrophe risk modeling firm AIR Worldwide (AIR) announced that it has expanded the capabilities of its terrorism risk model to support scenario testing for the United States and twenty-seven other select countries to help companies assess the impact of different attack scenarios on their portfolios and better manage their global terrorism risk. AIR Worldwide is a Verisk Analytics business.
-
-
Freight airships may soon help Asian companies reach world markets
The rise of freight airships could go down like a lead balloon with traditional aircraft companies, but could also represent a new high for Asian companies seeking to exploit new ways to reach world markets. Researchers explain how the reinvented technology of airships has come apace in recent years and is a far cry from the trial and error methods and primitive materials used to build the giant Zeppelins of yesteryear.
-
-
Oklahoma shuts down 37 wells after Saturday’s 5.6 magnitude earthquake
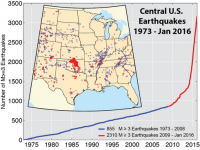
Oklahoma ordered the shutting down of 37 wells after Saturday’s 5.6 magnitude earthquake. Experts note that the significant increase in the number earthquakes measuring 3.0 or higher in Oklahoma has been linked to the practice of underground disposal of wastewater from oil and natural gas production. Only three earthquakes 3.0 magnitude or higher were recorded in 2009. Last year, the state had 907 such quakes. So far this year, there have been more than 400.
-
-
Solar-powered Ring Garden combines desalination, agriculture for drought-stricken California
With roughly 80 percent of California’s already-scarce water supply going to agriculture, it is crucial for the state to embrace new technologies that shrink the amount of water required to grow food. Alexandru Predonu has designed an elegant solution which uses solar energy to power a rotating desalination plant and farm that not only produces clean drinking water for the city of Santa Monica, but also food crops — including algae.
-
More headlines
The long view
Factories First: Winning the Drone War Before It Starts
Wars are won by factories before they are won on the battlefield,Martin C. Feldmann writes, noting that the United States lacks the manufacturing depth for the coming drone age. Rectifying this situation “will take far more than procurement tweaks,” Feldmann writes. “It demands a national-level, wartime-scale industrial mobilization.”
Trump Is Fast-Tracking New Coal Mines — Even When They Don’t Make Economic Sense
In Appalachian Tennessee, mines shut down and couldn’t pay their debts. Now a new one is opening under the guise of an “energy emergency.”
Smaller Nuclear Reactors Spark Renewed Interest in a Once-Shunned Energy Source
In the past two years, half the states have taken action to promote nuclear power, from creating nuclear task forces to integrating nuclear into long-term energy plans.
