-
U.S. Pharmaceutical Giant Says COVID Vaccine Could Be Ready for Emergency Use by Early 2021
U.S. pharmaceutical giant Johnson & Johnson says human testing of its experimental coronavirus vaccine will begin by September and says the vaccine could be available for emergency use by early next year.
The company said Monday that it has jointly committed more than $1 billion to develop and test a vaccine along with the U.S. Department of Health and Human Services. It said if human trials of the vaccine are successful, it is prepared to produce more than 1 billion doses of the vaccine.
-
-
Pandemic Bonds: The Financial Cure We Need for COVID-19?
Like other financial players that have embraced innovation in recent years, insurers too have developed novel tools and products. One such innovation is catastrophe bonds. A catastrophe bond provides the issuer (usually either an insurer or a reinsurer) with financial protection in case of a major catastrophe. Most catastrophe bonds cover extreme natural events such as hurricanes or earthquakes, but some bonds cover pandemics like the one the world is facing now.
-
-
Cryptocurrency Laundering Is a National Security Risk
As U.S. adversaries get more acquainted with blockchain technology, their hostile cyber operations are likely to rely increasingly on cryptocurrency activity. And rogue states are likely to become more innovative in using cryptocurrencies as they try to dampen the impact of U.S. economic sanctions.
-
-
Understanding the Economic Shock of Coronavirus
As the coronavirus continues its march around the world, governments have turned to proven public health measures, such as social distancing, to physically disrupt the contagion. Yet, doing so has severed the flow of goods and people, stalled economies, and is in the process of delivering a global recession. Economic contagion is now spreading as fast as the disease itself.
Philipp Carlsson-Szlezak , Martin Reeves, and Paul Swartz write in the Harvard Business Review that this didn’t look plausible even a few weeks ago. As the virus began to spread, politicians, policy makers, and markets, informed by the pattern of historical outbreaks, looked on while the early (and thus more effective and less costly) window for social distancing closed. Now, much further along the disease trajectory, the economic costs are much higher, and predicting the path ahead has become nearly impossible, as multiple dimensions of the crisis are unprecedented and unknowable.
“In this uncharted territory, naming a global recession adds little clarity beyond setting the expectation of negative growth. Pressing questions include the path of the shock and recovery, whether economies will be able to return to their pre-shock output levels and growth rates, and whether there will be any structural legacy from the coronavirus crisis,” they write. -
-
Sweden under Fire for “Relaxed” Coronavirus Approach – Here’s the Science Behind It
A growing number of Swedish doctors and scientists are raising alarm over the Swedish government’s approach to COVID-19. Unlike its Nordic neighbors, Sweden has adopted a relatively relaxed strategy, seemingly assuming that overreaction is more harmful than under-reaction. Some support the government’s policy as rational and reasonable, while critics say that Sweden is hurtling toward a disaster of biblical proportions and that the direction of travel must change. The truth is that of all these opinions, none is derived from direct experience of a global pandemic. No one knows for sure what lies ahead.
-
-
Deal with Ransomware the Way Police Deal with Hostage Situations
When faced with a ransomware attack, a person or company or government agency finds its digital data encrypted by an unknown person, and then gets a demand for a ransom. The two major ways people have so far responded – pay the ransom of hire a specialist to recover the data — are missing another option that we have identified in our cybersecurity policy studies. Police have a long history of successful crisis and hostage negotiation – experience that offers lessons that could be useful for people and organizations facing ransomware attacks.
-
-
MyPillow, Other U.S. Companies Making Face Masks to Meet Coronavirus Shortages
As coronavirus cases start to overwhelm U.S. hospitals, American companies say they’re starting to make face masks and other personal protective equipment critically needed by medical staff.
Brie Stimson writes in Fox News that in Minnesota, the MyPillow company is refocusing 75 percent of its production to face masks for health care workers.
“We have capacity to make a lot of things at big rates and we’re going to be going hopefully from 10,000 units a day to 50,000 units a day in a very short period of time,” CEO Mike Lindell told FOX 9 of Minneapolis-St. Paul.
In New Jersey, Stuart Carlitz, president and CEO of mattress company Eclipse International, said he made the decision to switch production to masks last week after hearing New York Gov. Andrew Cuomo say that state had a shortage and was paying high prices for masks.
“I’m not trying to sell masks,” Carlitz said. “Whether it’s a dollar apiece or four dollars apiece, that’s not going to change my business. I’m going to donate the masks.”
Other companies, too, have converted their production lines to producing masks, among them: The Tablecloth Company in Paterson, N.J., decided to start making masks after requests from customers, including nursing homes where the virus can easily spread, according to NJ.com.
Los Angeles-based apron company Hedley &Bennett will also be putting its 30 factory employees to work on face masks, Owner Ellen Bennett told Fast Company magazine.
Other American fashion brands like Hanes, Los Angeles Apparel and Michael Costello and Karla Colletto Swimwear are also asking their workers to start making masks.
Michigan-based Ford is assisting General Electric Healthcare with ventilator production, according to Yahoo Finance. -
-
Economic Crash Could Cost More Life Than Coronavirus, Says Expert
If the coronavirus lockdown leads to a fall in GDP of more than 6.4 per cent more years of life will be lost due to recession than will be gained through beating the virus, a study suggests.
Philip Thomas, professor of risk management at Bristol University, said that keeping the economy going in the next year was crucial, otherwise the measures would “do more harm than good.”
“I’m worried that in order to solve one problem we’d create a bigger problem,” he said a day after economists predicted we were on course for the worst recession in modern history.
Tom Whipple writes in The Times that there is a clear link between GDP and life expectancy, in part due to richer countries being able to spend more on healthcare, safety and environmental regulations. This means it is possible to calculate roughly the effect of increased, or decreased, wealth on the health of a population. -
-
Fast COVID-19 Test to Be Limited to Hospitals
Sunnyvale, California-based Cepheid has a new diagnostic test for the coronavirus – a test which returns results in just 45 minutes, four times faster than existing systems. Techcrunch reports, however, that the test, which was cleared by the Food and Drug Administration last week, will not materially affect the number of tests experts say are needed because it will likely be used only in the most urgent situations: triaging patients who are already in the hospital or the emergency room, and testing health care workers who might be infected to see whether they can return to work.
-
-
Facebook, Twitter Remove Russia-Linked Fake Accounts Targeting Americans
Social-media giants Facebook and Twitter say they have removed a number of Russia-linked fake accounts that targeted U.S. users from their operations in Ghana and Nigeria. Facebook on 12 March said the accounts it removed were in the “early stages” of building an audience on behalf of individuals in Russia, posting on topics such as black history, celebrity gossip, and fashion.
-
-
U.K.: Tory MPs Rebel against Government’s Huawei’s Plan
The U.K. government has launched an all-hands-on-deck effort to contain a growing rebellion by Tory MPs who want to ban the use of Huawei’s equipment in the U.K. 5G telecoms network, arguing that allowing the Chinese company, with its close ties to China’s intelligence and military establishments, any access to the country’s communication infrastructure would be like inviting a fox to guard the hen house.
-
-
American Observers Threatened over Guyana Election Results
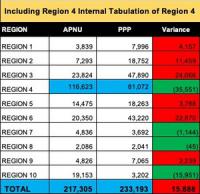
Tensions are rising in newly oil-rich Guyana with nearly 100 percent of the votes now reported from Monday’s national election. The governing APNU party appears to have lost to the opposition Peoples Progressive Party (PPP). International elections observers – mostly Americans – are now being menaced and threatened by APNU to leave or face arrest. Guyana’s election is being watched closely because the winner will be in control of a coming oil boom which will transform Guyana. In December Exxon began commercial exploitation of a huge 2016 oil discovery off the coast, and production is expected to grow from 52,000 barrels per day to over 750,000 by 2025.
-
-
Lawmaker Presses Clearview AI on Foreign Sales of Facial Recognition
Senator Edward J. Markey (D-Massachusetts earlier this week raised new concerns about Clearview AI’s facial recognition app. Markey initially wrote to Clearview in January 2020 with concerns about how the company’s app might violate Americans’ civil liberties and privacy. Clearview is marketing its product to users in foreign countries with authoritarian regimes such as Saudi Arabia. The company might also be collecting and processing images of children from social media sites.
-
-
Extreme Weather Events Could Bring Next Recession
Physical climate risk from extreme weather events remains unaccounted for in financial markets. Without better knowledge of the risk, the average energy investor can only hope that the next extreme event won’t trigger a sudden correction, according to new research. Experts say that the market needs to plan for weather risk, or face extreme correction.
-
-
Bipartisan Bill Would Reimburse Telcoms for Replacing Huawei’s, ZTE’s Equipment
New bipartisan legislation aims to protect American communications networks from threats presented by foreign suppliers like Huawei and ZTE. The “rip and replace” part of the legislation would offer relief to reimburse smaller telecommunications providers – largely in rural areas – by reimbursing them for the costs of removing and replacing untrusted foreign equipment.
-
More headlines
The long view
Factories First: Winning the Drone War Before It Starts
Wars are won by factories before they are won on the battlefield,Martin C. Feldmann writes, noting that the United States lacks the manufacturing depth for the coming drone age. Rectifying this situation “will take far more than procurement tweaks,” Feldmann writes. “It demands a national-level, wartime-scale industrial mobilization.”
Trump Is Fast-Tracking New Coal Mines — Even When They Don’t Make Economic Sense
In Appalachian Tennessee, mines shut down and couldn’t pay their debts. Now a new one is opening under the guise of an “energy emergency.”
Smaller Nuclear Reactors Spark Renewed Interest in a Once-Shunned Energy Source
In the past two years, half the states have taken action to promote nuclear power, from creating nuclear task forces to integrating nuclear into long-term energy plans.
