-
DHS forced to release list terms it monitors on social media
Following a Freedom of Information Act (FOIA) request by the Electronic Privacy Information center (EPIC), DHS was forced to release its 2011 Analyst’s Desktop Binder; the binder, among other things, contains a list of words DHS uses as triggers of suspicious communication when the department’s analysts monitor social media
-
-
Malware intelligence system allow organizations to share threat information
As malware threats expand into new domains and increasingly focus on industrial espionage, researchers are launching a new tool to help battle the threats: a malware intelligence system which will help corporate and government security officials share information about the attacks they are fighting
-
-
How govt. can achieve IT savings, innovation
Innovative shifts in technology can springboard government into a new era of efficiency, effectiveness, and transparency; lawmakers urged to focus not only on technology infrastructure to achieve savings and efficiencies, but also consider how the government procures and delivers
-
-
SAIC Launches Inaugural Utah Cyber Defense Challenge and Symposium 2012

SAIC will lead a Utah statewide cyber competition and symposium designed to raise cyber awareness across government, academia, and industry; the Utah Cyber Defense Challenge and Symposium (UCDC) 2012, to be held 1 June
-
-
Execs offered cyber security degree track at NYU-Poly
Polytechnic Institute of New York University says that because defending institutional data against attack depends equally on cyber security experts as well as executives who command management and technical skills, it is introducing a management track to its master’s degree in cyber security; first classes begin this summer
-
-
Using Twitter to share information after a disaster
A new study shows how people used Twitter following the 2011 nuclear disaster in Japan, highlighting challenges for using the social media tool to share information; the study also indicates that social media have not changed what we communicate so much as how quickly we can disseminate it
-
-
Texas fights identity theft
Everything is bigger in Texas, including the number of instances of identity manipulation; according to an April report from ID Analytics, the cities of Beaumont and El Paso lead the nation in per-capita identity manipulation attempts
-
-
McAfee, Intel collaborate on protecting energy infrastructure

McAfee and Intel will collaborate on improving the protection of the world’s energy utilities, including generation, transmission, and distribution, from increased cyber attacks; the two companies have provided a blueprint for a comprehensive solution of multiple products which create layers of security and operate together without great complexity or without impacting availability
-
-
Self-adapting computer network that actively defends itself against hackers
Researchers are looking into the feasibility of building a computer network that could protect itself against online attackers by automatically changing its setup and configuration; the researchers will examine whether this type of adaptive cybersecurity, called moving-target defense, can be effective – and cost-effective
-
-
Travelers’ laptops infected through fake software updates in foreign hotel rooms
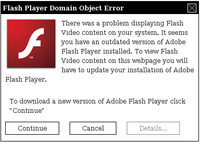
Recent analysis from the FBI and other government agencies demonstrates that malicious actors are targeting travelers abroad through pop-up windows while establishing an Internet connection in their hotel rooms
-
-
Yucca Mountain as a data depository

For nearly three decades, Yucca Mountain was the place designated as the country’s nuclear waste repository; after many years of study and exploration, the Obama administration, two years ago, decided not to ask for additional funds for the project; now there is another idea for the site: turning it into a giant, secure data center
-
-
Free mobile security to U.S. government agencies
A company offers its mobile security solutions, free of charge, to U.S. defense agencies; the offer is part of the NSA/CSS Co-operative Research and Development Agreement
-
-
FBI seeking wiretap-ready Web
As communications have changed in recent years from the traditional telephone system to the Internet, the FBI has found itself facing greater difficulty in carrying out surveillance operations; the agency is asking Internet companies not to oppose a coming proposal which would require them to provide a surveillance backdoor
-
-
Number, diversity of targeted cyberattacks increased in 2011
The number of vulnerabilities decreased by 20 percent in 2011, but the number of malicious attacks leaped by 81 percent in the same period; targeted attacks have spread to organizations of all sizes and types
-
-
Slowing time as a way to counter cyberattacks
Researchers offer a new way to deal with cyberattacks on critical infrastructure like power and water utilities and banking networks: slow down Internet traffic, including the malicious code, when an attack is suspected; this would allow networks time to deal with the attacks
-
More headlines
The long view
Researchers Develop AI Agent That Solves Cybersecurity Challenges Autonomously
New framework called EnIGMA demonstrates improved performance in automated vulnerability detection using interactive tools.
