-
Signcryption technology tightens cybersecurity
Signcryption is a data security technology by which confidentiality is protected and authenticity is achieved seamlessly at the same time; it has now been formally recognized as an international standard by the International Organization of Standardization (ISO)
-
-
UMD, Lunarline partner on cybersecurity
The University of Maryland Cybersecurity Center will partner with Lunarline Inc. on cybersecurity education, research, and technology development
-
-
Wireless passwords vulnerable to hackers, US-CERT warns
The U.S. government is warning wireless users that their home and business networks are highly vulnerable to hackers
-
-
Smartphone users hold false sense of security
A recent study reveals that smartphone users maintain a false sense of cybersecurity
-
-
New Apple facial recognition tech could make passwords obsolete
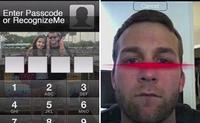
Passwords could become a thing of the past for Apple iPhone and iPad users; the tech company recently revealed a patent application for what it is calling “Low Threshold Face Recognition,” a tool that would allow users to unlock their phones by simply picking up the device and pointing it at their face
-
-
McAfee releases 2012 cyber threat predictions

The cyberthreats organizations and individuals are likely to face in 2012 will resemble those they faces in 2011, only more so; among the increased threats: attacks on critical infrastructure, mobile devices and consumer electronics, and politically motivated attacks
-
-
DHS social media monitoring policy under fire
DHS’ tactics of gathering intelligence via social media has drawn sharp criticism from privacy advocates with one group filing a lawsuit against the department
-
-
Lieberman asks Twitter to shut down Taliban accounts

Senator Joe Lieberman (I-Connecticut), the chair of the Homeland Security Committee, has requested that the popular social media site Twitter shut down the accounts of the Taliban
-
-
DHS, Idaho lab win cybersecurity innovation award
The Controls Systems Security Program (CSSP) at DHS and Idaho National Laboratory have created a series of training programs for managerial and technical people in the critical infrastructure sector that are packed with up-to-date information on cyber threats and mitigations for vulnerabilities
-
-
Anonymous threatens Internet blackout over controversial legislation

The hacker group Anonymous has vowed to blackout the Internet if U.S. lawmakers pass the controversial Stop Online Piracy Act; under the bill, government powers would be greatly expanded, enabling the Justice Department working at the behest of individual copyright holders to shut down Web sites for potential copyright violations
-
-
Lawmaker targets fake ID smartphone app

With the “License” app for Apple iPhones and iPads, making a realistic fake ID has never been easier; to prevent this app from falling into the wrong hands that would use it for nefarious purposes, Senator Bob Casey (D — Pennsylvania) recently requested that Apple remove the app from its online store
-
-
National Guardsmen, the new front line in cybersecurity

In an aggressive push to expand the military’s cyber warfare and defense capabilities, the National Guard has formed an increasing number of special cybersecurity units; National Guard cybertroops have proven to be particularly appealing solution, especially with defense cuts looming, as they cost less to train, maintain, and retain than active duty forces
-
-
Twelve Chinese hacker groups responsible for attacks on U.S.

U.S. cybersecurity experts say as few as twelve different Chinese hacker collectives, working at the behest of the government, are responsible for the majority of cyberattacks on U.S. businesses and government agencies; the bulk of the attacks are stealthy in nature and have resulted in the loss of billions of dollars’ worth of intellectual property and state secrets from the private and public sector
-
-
Electrical grid needs cybersecurity oversight: study

In a recently released report, researchers from the Massachusetts Institute of Technology say that a single federal agency should be tasked with protecting the United States’ electrical grid from cyberattacks; the Obama administration has proposed that DHS assume responsibility for the grid, while Congress has submitted proposals for both the Department of Energy and the Federal Energy Regulatory Commission (FERC)
-
-
MIT report warns U.S. electrical grid vulnerable
A new report from the Massachusetts Institute of Technology warns that the U.S. electrical grid is vulnerable to cyberatacks; according to the report, the U.S. electrical grid’s cybersecurity vulnerabilities stem from weaknesses in processes, technology, as well as the actual physical environment
-
More headlines
The long view
Researchers Develop AI Agent That Solves Cybersecurity Challenges Autonomously
New framework called EnIGMA demonstrates improved performance in automated vulnerability detection using interactive tools.
