-
Are your phones really secure?
Breakthroughs in technology have enabled malicious actors to listen in on any conversation using your phone even when not in use; eavesdroppers have circumvented encrypted audio channels by relying on a relatively simple principle in physics — resonance; by tapping into an object’s natural resonance, spies have turned phones and phone cables into listening devices even when they are not in use; researchers at Teo, a manufacturer of secure telecommunications equipment, were able to capture human voices using standard phones, unplugged Ethernet cables, or even a rock; to address this security gap, Teo has designed its IP TSG-6 phones with special vibration dampening circuitry and materials that render them impervious to these types of listening devices
-
-
Android apps send private data in the clear

Cell phones running the Android operating system fail to encrypt data sent to and from Facebook and Google Calendar, shortcomings that could jeopardize hundreds of millions of users’ privacy; Facebook’s recently unveiled always-on SSL encryption setting to prevent snooping over insecure networks — but the encryption is no good, meaning that all private messages, photo uploads, and other transactions are visible to eavesdroppers
-
-
CyberCom commander calls for government protection of critical infrastructure

General Keith Alexander, the head of the U.S. Cyber Command, is calling for the creation and implementation of a government strategy to protect critical infrastructure in the United States from cyber attacks; in a speech yesterday, General Alexander emphasized the importance of securing critical infrastructure like the stock market, the electrical grid, and power plants against cyber attacks; he sought to ease fears by assuring the audience that the government could protect critical infrastructure and preserve civil liberties; Alexander’s remarks come as civil rights advocates and internet freedom groups have grown more vociferous in their criticism of a recent Senate bill that would help secure the nation’s critical infrastructure from cyber attacks; supporters of the bill say that it is impossible to create an internet “kill switch” and that is not their goal
-
-
U.K. rethinking cyber security
U.K. cyber crime could cost more than 27 billion Pounds a year; the estimate of 21 billion Pounds to businesses, 2.2 billion Pounds to government, and 3.1 billion Pounds to citizens may be an under-estimation due to a possible lack of reporting for fear of reputational damage; the hardest-hit sectors being pharmaceuticals, biotech, electronics, IT, and chemicals
-
-
Defining cyber warfare
Several high-profile cyberattack incidents lead commentators to worry that we may be using the wrong metaphor to describe the phenomena; Bruce Schneier, for example, says that “What we are seeing is not cyber war but an increasing use of war-like tactics and that is what is confusing us. We don’t have good definitions of what cyber war is, what it looks like and how to fight it”
-
-
FBI says it does not demand encryption back doors
The FBI says that it is not calling for restrictions on encryption without back doors for law enforcement; only last fall the agency said discussions should focus on requiring that communication providers and Web sites have legally mandated procedures to divulge unencrypted data in their possession; the FBI says that because of the rise of Web-based e-mail and social networks, it’s “increasingly unable” to conduct certain types of surveillance that would be possible on cellular and traditional telephones
-
-
Police using text messages to fight crime
In an increasing trend police departments across the United States are using text messages to help fight crime; various police departments have set up a text message service that allows citizens to report any crimes that they see; informants can stay anonymous while department officials can exchange texts with them to learn more; police departments have long had anonymous hotlines in place, and text messages are the technological upgrade to these hotlines; text message systems were first introduced in 2007 in Boston and Cincinnati; this year several smaller police departments will implement a text based tip system including those in Apex, North Carolina and Colorado Springs, Colorado
-
-
DHS requesting boost in cybersecurity funds
Government, industry, and academia have labeled the shortage of cyber specialists in the government as a national security problem; the United States is looking to hire 30,000 security experts to safeguard cyberspace as opposed to the 1,000 personnel currently staffed government wide; DHS has requested $936 million in funding for FY 2012 to grow the federal cybersecurity workforce and enhance network protections
-
-
IT organization surveys potential insider-threats
Employees are being overloaded with passwords; 10 percent of IT professionals are still able to access accounts from a prior job; 52 percent of employees admit that they have shared their work log-ins and passwords with other co-workers, and vice versa
-
-
Hackers steal data from oil giants worth millions
McAfee Inc. recently announced that hackers have stolen data worth millions from five major multinational oil and gas companies; in the attacks, dubbed “Night Dragon,” hackers stole company secrets like bidding contracts, oil exploration data, proprietary industrial processes, and sensitive financial documents; analysts determined that hackers initially began infiltrating company networks in November 2009 using relatively simple methods; the information that the cyber thieves took was “tremendously sensitive and would be worth a huge amount of money to competitors”; the methods of execution and circumstantial evidence implicate China
-
-
Hackers release Stuxnet's decompiled code online
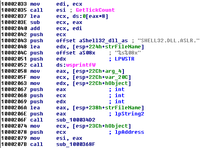
The Stuxnet worm was a cybermissile designed to penetrate advanced security systems; it was equipped with a warhead that targeted and took over the controls of the centrifuge systems at Iran’s uranium processing center in Natanz, and it had a second warhead that targeted the massive turbine at the nuclear reactor in Bushehr; security experts say it is the most sophisticated cyberweapon ever designed; now, a group of anonymous “hacktivists” hacked the computers of a U.S. security company and stole a decrypted version — the decompiled code — of the malware, and put it on the Web; security experts are anxious: “There is the real potential that others will build on what is being released,” says one; this will not lead to an immediate threat, but it could lead to something soon, he added; “Weeks wouldn’t surprise me”
-
-
Cyberweapon could cause Internet doomsday
Researchers show that an attack by a large botnet — a network of computers infected with software that allows them to be externally controlled — could take down the Internet; the researchers reckon that 250,000 such machines would be enough to do the job; a sustained 20-minute attack by the 250,000-strong army — they will be sending waves of border gateway protocol (BGP) updates to every router in the world — would overwhelm the net, bringing Web servers down by overloading them with traffic
-
-
Hoover Dam is safe from hackers
In response to the debate over the controversial Senate Internet “kill switch” bill, the U.S. Bureau of Reclamation refuted a central argument that the law’s proponents have been using; proponents of the bill have often stated the need for the bill because terrorists could hack into the system and open the Hoover Dam’s floodgates; the dam is not connected to the Internet and has several physical and technological safeguards that prevent the floodgates from opening; the proposed bill would authorize the president to sever critical infrastructure from the Internet in the event of a cyber attack; critics say the bill could violate First Amendment rights
-
-
Cell phones are hackers' target of choice
In its fourth quarter threat report, McAfee announced that hackers have increasingly turned their attention to smart phones; in 2010 there was a 56 percent increase in malware targeting cell phones; hackers most frequently used Adobe products like PDFs and Flash to embed pernicious code; Google’s Android smart phone operating system was also a target of choice; the report noted that spam levels were down 62 percent, while politically motivated hacking was on the rise
-
-
Cybersecurity named one of top five global threats
World leaders at the World Economic Forum in Davos named cyber security as one of the top five global risks in its 2011 report; the report identifies four key areas that pose global risks: cyber theft, cyber espionage, cyber war, and cyber terrorism; observers worry that the Stuxnet virus, which damaged Iran’s nuclear centrifuges, may have sparked a cyber arms race and are particularly concerned about the lack of established international norms surrounding these weapons; the report fears that cyber attacks on nations could lead to conventional attacks
-
More headlines
The long view
Researchers Develop AI Agent That Solves Cybersecurity Challenges Autonomously
New framework called EnIGMA demonstrates improved performance in automated vulnerability detection using interactive tools.
