-
Mexico to use drones, satellites in a renewed effort to find dead students
Mexico said it would launch a new search, joined by international experts, for the remains of dozens of students training to be teachers who were abducted and apparently massacred in 2014. Forty-three students were abducted by corrupt municipal police, and then turned over to a local drug gang to be killed. Apparently, the gang leaders believed the students were linked to a rival drug gang in the area.
-
-
Internal fingerprint sensor enables more accurate ID
In the 1971 film “Diamonds are Forever,” British secret agent James Bond uses fake fingerprints as part of a ploy to assume the identity of a diamond smuggler. At the time, sham prints were purely a futuristic bit of Bond gadgetry, but technology has since caught up. Quickly detecting “internal fingerprints” and sweat pores could make fingerprint sensors more reliable and less likely to be tricked by fake fingerprints.
-
-
FEMA assessing over-the-air broadcast alerting technology
FEMA’s National Continuity Programs’ Integrated Public Alert and Warning System Division (IPAWS) has begun to assess the feasibility of a public alert and warning capability which is being developed in the private sector. FEMA says that new technologies could deliver detailed emergency information to the public with pictures and videos of evacuation routes, storm tracks, and shelter information — increasing community preparedness before, during, and after a disaster.
-
-
Technology confronts disasters
In 2010, soon after Haiti was devastated by an earthquake, a team from MIT Lincoln Laboratory collected and analyzed information to help the U.S. Southern Command (USSOUTHCOM), the lead military agency responding to the crisis, effectively dispatch vital resources, including food, water, tents, and medical supplies, to the victims of this disaster. This Haiti experience demonstrated to Lincoln Laboratory researchers that advanced technology and technical expertise developed for the Department of Defense (DoD) can significantly benefit future humanitarian assistance and disaster relief efforts. In February, the Laboratory established the Humanitarian Assistance and Disaster Relief (HADR) Systems Group to explore ways to leverage or advance existing capabilities for improving disaster responses.
-
-
ACLU lawsuit seeks disclosure of details of CIA drone program
The American Civil Liberties Union (ACLU) is continuing its campaign over CIA drone use with a lawsuit filed on Monday to force the CIA to turn over details about the U.S. clandestine drone war program. The ACLU lawsuit, coming a week after some of details of the program were leaked, asks for summary data from the CIA on drone strikes, including the locations and dates of strikes, the number of people killed and their identities or status.
-
-
U.S. to clean up site of a 1966 nuclear weapons accident in Spain
On 17 January 1966, a B-52 bomber carrying four hydrogen bombs collided with a KC-135 tanker plane during mid-air refueling off the coast of Almería, Spain, killing seven of the eleven crew members. Two of the bombs were recovered intact from the sea, but the other two leaked radiation into the surrounding countryside when their plutonium-filled detonators went off, strewing 3kg of radioactive plutonium 239 around the town of Palomares. Following the accident, the U.S. military shipped 1,700 tons of contaminated soil to South Carolina, and the whole thing was forgotten. On Monday in Madrid, Secretary of State John Kerry and the Spanish foreign minister José Manuel García-Margallo, signed an agreement to clean up the site after tests showed that 50,000 cubic meters of soil were still contaminated.
-
-
Airborne networking capabilities for hostile environments
Modern airborne warfare is becoming increasingly complex, with manned and unmanned systems having rapidly to share information in a volatile environment where adversaries use advanced, commercially available electronic systems to disrupt U.S. and allied communications. DARPA’s Dynamic Network Adaptation for Mission Optimization (DyNAMO) program. DyNAMO seeks novel technologies which would enable independently designed networks to share information and adapt to sporadic jamming and mission-critical dynamic network bursts in contested RF environments.
-
-
Justice Department created new office to focus on domestic terrorists
The Justice Department said this week that it has created a new office which would on homegrown extremists. Assistant Attorney General John P. Carlin announced the move on Wednesday. He said the new office, the Domestic Terrorism Counsel, will be the main point of contact for federal prosecutors working on domestic terrorism cases. Carlin said the new office was created “in recognition of a growing number of potential domestic terrorism matters around the United States.” Following the 9/11 attacks, U.S. law enforcement had shifted its attention, and the allocation of law enforcement and intelligence resources, from domestic to foreign terrorism. The result, security experts say, was that federal authorities had lost sight of domestic extremists. “Looking back over the past few years, it is clear that domestic terrorists and homegrown violent extremists remain a real and present danger to the United States. We recognize that, over the past few years, more people have died in this country in attacks by domestic extremists than in attacks associated with international terrorist groups,” Carlin said.
-
-
U.S. tries to persuade Pakistan not to deploy small tactical nuclear weapons

Pakistani Prime Minister Nawaz Sharif is coming to the United States next week on an official visit, and ahead of the visit the Obama administration is holding talks with Pakistani officials about Pakistan’s plan to deploy a small tactical nuclear weapon which would be more difficult to monitor and secure than Pakistan’s arsenal of larger weapons. U.S. officials fear that the smaller weapons are easier to steal, or would be easier to use should they fall into the hands of a rogue commander. “All it takes is one commander with secret radical sympathies, and you have a big problem,” said one former official.
-
-
Anti-drone defense system now features quad band RF inhibitor, optical disruptor
The world’s first fully integrated detect-track-disrupt Anti-UAV Defense System (AUDS) — launched by a trio of British companies in May this year — now features a quad band radio frequency (RF) inhibitor/jammer, an optical disruptor, and rapid deployment features in the final production version of the counter-drone system. The companies say that these enhancements follow extensive customer trials of the pre-production system across Europe and North America over the spring and summer.
-
-
Lockheed Martin begins production of modular high-power laser

Lockheed Martin has begun production of a new generation of modular high power lasers this month. The first laser built using the modular technique will be a 60-kilowatt system for a U.S. Army vehicle. The Army has the option to add more modules and increase power from 60kW to 120kW. Laser weapons provide a complement to traditional kinetic weapons in the battlefield. In the future, they will offer reliable protection against threats such as swarms of drones or large numbers of rockets and mortars.
-
-
White House will not seek law allowing law enforcement access to encrypted messages
The Obama administration has decided not to seek legislation which would require tech companies to design their devices in a way which would give law enforcement agencies access to individuals’ encrypted messages, the White House said on Saturday. The tech industry, led by giants Apple, Google, Facebook, IBM, and Microsoft, has mounted a vigorous campaign opposing any administration moves to weaken ever-more-sophisticated encryption systems which are designed to protect consumers’ privacy.
-
-
How Syria is becoming a test bed for high-tech weapons of electronic warfare

Russia’s military presence in Syria has been steadily increasing over the past few months. The latest reports are that Russia has also deployed its most modern electronic warfare system to Syria — the Krasukha-4 (or Belladonna) mobile electronic warfare (EW) unit. The Krasukha-4 is a broad-band multifunctional jamming system designed to neutralize Low-Earth Orbit (LEO) spy satellites such as the U.S. Lacrosse/Onyx series, airborne surveillance radars and radar-guided ordinance at ranges between 150km to 300km. U.S. and NATO intelligence gatherers will have “electronic counter countermeasures” (ECCM) to combat Russian EW interference — and so the cat and mouse game of the cold war is repeated. Intelligence gathering and radar-guided munitions will suffer some disruption and mistakes may be made but operations will continue. Russia will now be able to test its new EW systems in live combat but avoiding direct conflict with NATO — it will enhance overseas sales prospects of the Krasukha-4 system. NATO will be able test its ECCM against another EW system, presumably with similar ends in mind.
-
-
Predictive policing substantially reduces crime in Los Angeles during 21-month period
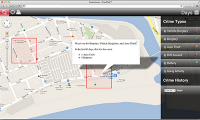
Can math help keep our streets safer? A new study by a UCLA-led team of scholars and law enforcement officials suggests the answer is yes. A mathematical model they devised to guide where the Los Angeles Police Department should deploy officers, led to substantially lower crime rates during a recent 21-month period. The model was so successful that the LAPD has adopted it for use in 14 of its 21 divisions, up from three in 2013.
-
-
An app alerts people, law enforcement about potential crime risk
You are walking home after a night out on a dark autumn evening. Suddenly, you get the feeling that someone is following you. You look over your shoulder, and see a shadow between the trees in the park. You quicken your steps. When you glance behind you again, you see the shadow disappear in between two houses. This is when you could press the “help” button on the app that you have downloaded. It sends a message to everyone in the area who also has the app, with information about your phone number and where you are. This way they are able to call you, alert emergency services, or get to your location if need be. The app has been developed by a group of student entrepreneurs.
-
More headlines
The long view
Factories First: Winning the Drone War Before It Starts
Wars are won by factories before they are won on the battlefield,Martin C. Feldmann writes, noting that the United States lacks the manufacturing depth for the coming drone age. Rectifying this situation “will take far more than procurement tweaks,” Feldmann writes. “It demands a national-level, wartime-scale industrial mobilization.”
How Male Grievance Fuels Radicalization and Extremist Violence
Social extremism is evolving in reach and form. While traditional racial supremacy ideologies remain, contemporary movements are now often fueled by something more personal and emotionally resonant: male grievance.
The Surprising Reasons Floods and Other Disasters Are Deadlier at Night
It’s not just that it’s dark and people are asleep. Urban sprawl, confirmation bias, and other factors can play a role.
Why Flash Flood Warnings Will Continue to Go Unheeded
Experts say local education and community support are key to conveying risk.
