-
U.K. launching broad anti-extremism strategy
Amid growing concerns about the growth of home-grown terrorism, British prime minister David Camron has announce that the government will spend millions on funding anti-extremism projects in communities and tackling online attempts to radicalize vulnerable Britons. The new funding would be used to providing direct support to groups to expand the reach and scale of their work to confront extremism. Projects will include social media training and technical assistance to enable small charities to set up Web sites. “We need to systematically confront and challenge extremism and the ideologies that underpin it, exposing the lies and the destructive consequences it leaves in its wake. We have to stop it at the start — stop this seed of hatred even being planted in people’s minds and cut off the oxygen it needs to grow,” Cameron said.
-
-
If you think your emails are private, think again
When you type up a racy e-mail to a loved one, do you consider the details private? It appears that at least some Internet users expect a different, and higher, level of privacy simply because the information is cloaked in an e-mail. That’s the issue at stake in a pending lawsuit against Yahoo! Inc. Plaintiffs filed an e-mail privacy lawsuit against Yahoo in the U.S. District Court for the Northern District of California under several privacy laws, including the Stored Communications Act (SCA) — a federal law that prohibits an e-mail service provider from knowingly divulging to any person or entity the contents of a communication while in electronic storage. The plaintiffs won a short-term victory in achieving class action certification, but the bigger issue over whether they can object to the scanning of their e-mails by Yahoo — based on a right to privacy — given Yahoo’s disclosure of its scanning and possible sharing practices and given that they chose to send and/or receive an e-mail to a Yahoo user, is far from being decided in their favor.
-
-
Justice Department created new office to focus on domestic terrorists
The Justice Department said this week that it has created a new office which would on homegrown extremists. Assistant Attorney General John P. Carlin announced the move on Wednesday. He said the new office, the Domestic Terrorism Counsel, will be the main point of contact for federal prosecutors working on domestic terrorism cases. Carlin said the new office was created “in recognition of a growing number of potential domestic terrorism matters around the United States.” Following the 9/11 attacks, U.S. law enforcement had shifted its attention, and the allocation of law enforcement and intelligence resources, from domestic to foreign terrorism. The result, security experts say, was that federal authorities had lost sight of domestic extremists. “Looking back over the past few years, it is clear that domestic terrorists and homegrown violent extremists remain a real and present danger to the United States. We recognize that, over the past few years, more people have died in this country in attacks by domestic extremists than in attacks associated with international terrorist groups,” Carlin said.
-
-
U.S. deploys 300 U.S. troops to Cameroon to bolster campaign against Boko Haram

President Barack Obama on Wednesday notified the Congress of his plan to deploy 300 troops to Cameroon to provide intelligence, surveillance, and reconnaissance operations to the militaries of Nigeria, Cameroon, Chad, and Niger as they battle the Islamist Boko Haram insurgents. In a letter released by the White House, the president said ninety personnel had already been deployed, and that they would be armed for self-defense. A senior administration official said the deployment was “part of the counter Boko Haram effort.”
-
-
U.S. tries to persuade Pakistan not to deploy small tactical nuclear weapons

Pakistani Prime Minister Nawaz Sharif is coming to the United States next week on an official visit, and ahead of the visit the Obama administration is holding talks with Pakistani officials about Pakistan’s plan to deploy a small tactical nuclear weapon which would be more difficult to monitor and secure than Pakistan’s arsenal of larger weapons. U.S. officials fear that the smaller weapons are easier to steal, or would be easier to use should they fall into the hands of a rogue commander. “All it takes is one commander with secret radical sympathies, and you have a big problem,” said one former official.
-
-
Will the Supreme Court kill the smart grid?
On 30 April, Tesla’s Elon Musk took the stage in California to introduce the company’s Powerwall battery energy storage system, which he hopes will revolutionize the dormant market for household and utility-scale batteries. A few days later, the Supreme Court announced that it would hear a case during its fall term that could very well determine whether Tesla’s technology gamble succeeds or fails. At issue is an obscure federal policy known in the dry language of the electricity business as “Order 745,” which a lower court vacated last year. Order 745 allowed electricity customers to be paid for reducing electricity usage from the grid — a practice known as “demand response.” It also stipulated that demand response customers would be paid the market price for not using the grid — like the power industry’s version of paying farmers not to grow corn. This case, ultimately, is far more significant than getting paid for not using electricity. It’s about who gets to set the rules of the road for emerging technology in the electricity sector — the states or the federal government — and whether the United States will be able to modernize its energy policy the same way that it would like to modernize its power grid.
-
-
Experts are often fallible, so expert advice should be examined carefully
Evidence shows that experts are frequently fallible, say leading risk researchers, and policy makers should not act on expert advice without using rigorous methods that balance subjective distortions inherent in expert estimates. Many governments aspire to evidence-based policy, but the researchers say the evidence on experts themselves actually shows that they are highly susceptible to “subjective influences” — from individual values and mood, to whether they stand to gain or lose from a decision — and, while highly credible, experts often vastly overestimate their objectivity and the reliability of peers.
-
-
U.S. to keep 5,500 troops in Afghanistan beyond January 2017

The United States will keep U.S. troops in Afghanistan beyond next year in response to Taliban advances. President Barack Obama was elected in 2008 promising to end U.S. ground involvement in Afghanistan before leaving office in January 2017, but he now admits that that promise cannot be kept. Obama will later today announce that 5,500 troops will remain in Afghanistan beyond January 2017. The present contingent of 9,800 U.S. troops would remain throughout most of next year, being reduced to 5,500 in 2017.
-
-
Pentagon inspects two Colorado prisons for Guantánamo detainees

A U.S. Defense Department team is spending three days this week in Colorado to determine whether two prisons in the state would be suitable for holding dozens of Guantánamo detainees indefinitely. The latest effort by President Barack Obama to close Guantánamo Bay involves inspecting a federal Supermax in Florence and a state penitentiary at Canon City to determine the feasibility of using them to continue the detention of men, currently at Guantánamo, who would not be charged or released by the United States. Colorado lawmakers oppose the move, and critics of the administration say the problem with Guantánamo is not its location, but the practice of indefinite detention without charge far from any active battlefield and the use of military tribunals – and these will not change in a U.S. domestic facility.
-
-
Turkey warns U.S., Russia against supporting Syrian Kurds
Turkish prime minister Ahmet Davutoğlu, referring the Syrian Kurdish forces, earlier today said that Turkey cannot accept “cooperation with terrorist organizations,” as Turkey summoned the U.S. and Russian ambassadors to Turkey to express Turkish displeasure with the United States and Russia supporting Kurdish groups fighting ISIS. Davutoğlu, has warned the United States and Russia against “unacceptable” military and political support for Syrian Kurdish forces fighting Islamic State in Syria. Turkey’s military actions in Syria are a mirror image of Russia’s military actions there. Russia says it is “fighting terrorism” in Syria, but more than 90 percent of its bombing attacks have targeted moderate, non-ISIS Syrian rebels, some of them backed by the United States. Turkey is also waging a “war on terror” in Syria, but the overwhelming majority of its airstrikes have targeted targets in the Kurdish region of Syria, not ISIS targets.
-
-
Christianity looks set to disappear from parts of the Middle East: Report
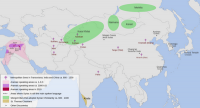
Christianity looks set to disappear from key parts of the Middle East, according to a report issued Tuesday, 13 October, which highlights a worsening cycle of persecution. Persecuted and Forgotten? A Report on Christians oppressed for their Faith 2013-15, compiled by Catholic charity Aid to the Church in Need, concludes that if the exodus of Christians from Iraq continues at existing levels, the Christians could all but disappear within five years, and that a faster rate of attrition is noted in Syria whose Christians have reportedly plummeted from 1.25 million in 2011 to as few as 500,000 today.
-
-
New strategy: U.S. airdrops arms, ammunition to Syrian rebel groups
In a demonstration of the U.S. strategy shift in Syria, the U.S. military on Sunday it carried out an arms and ammunition airdrop for Syrian rebel groups fighting Islamic State. Last week Washington announced the end of a $500 million program to train and equip vetted rebel groups. The U.S. military refused to provide any details about the groups that received the supplies, their location, or the type of equipment in the airdrop.
-
-
On symptoms and underlying conditions
In the last few days, Israelis in Jerusalem, Tel Aviv, and other cities have been facing a spontaneous, from-the-bottom-up campaign of violence by (mostly) Palestinian youth wielding, in most cases, no more than kitchen knives. This wave of attacks may soon recede, but another eruption of violence will surely come soon unless the underlying conditions are dealt with. The lone-wolf attacks are an immediate security problem with which Israel’s security services must deal. This security problem, however, is only the symptom of a deeper, more pernicious condition. As is the case with a medical condition, dealing with the symptoms would just not be sufficient.
-
-
How Syria is becoming a test bed for high-tech weapons of electronic warfare

Russia’s military presence in Syria has been steadily increasing over the past few months. The latest reports are that Russia has also deployed its most modern electronic warfare system to Syria — the Krasukha-4 (or Belladonna) mobile electronic warfare (EW) unit. The Krasukha-4 is a broad-band multifunctional jamming system designed to neutralize Low-Earth Orbit (LEO) spy satellites such as the U.S. Lacrosse/Onyx series, airborne surveillance radars and radar-guided ordinance at ranges between 150km to 300km. U.S. and NATO intelligence gatherers will have “electronic counter countermeasures” (ECCM) to combat Russian EW interference — and so the cat and mouse game of the cold war is repeated. Intelligence gathering and radar-guided munitions will suffer some disruption and mistakes may be made but operations will continue. Russia will now be able to test its new EW systems in live combat but avoiding direct conflict with NATO — it will enhance overseas sales prospects of the Krasukha-4 system. NATO will be able test its ECCM against another EW system, presumably with similar ends in mind.
-
-
Russia will soon begin to pay a steep price for Syrian campaign: Ash Carter
Moscow will soon begin to pay a steep price – in the form of reprisal attacks and casualties — for its escalating military intervention on behalf of the Assad regime in Syria, U.S. Defense Secretary Ashton Carter has warned. Earlier this week, fifty-five leading Muslim clerics, including prominent Islamists, urged “true Muslims” to “give all moral, material, political and military” support to the fight against Assad’s army as well as Iranian and Russian forces. “Russia has created a Frankenstein in the region which it will not be able to control,” warned a senior Qatari diplomat. “With the call to jihad things will change. Everyone will go to fight. Even Muslims who sit in bars. There are 1.5 billion Muslims. Imagine what will happen if 1 percent of them join.”
-
More headlines
The long view
Factories First: Winning the Drone War Before It Starts
Wars are won by factories before they are won on the battlefield,Martin C. Feldmann writes, noting that the United States lacks the manufacturing depth for the coming drone age. Rectifying this situation “will take far more than procurement tweaks,” Feldmann writes. “It demands a national-level, wartime-scale industrial mobilization.”
No Nation Is an Island: The Dangers of Modern U.S. Isolationism
The resurgence of isolationist sentiment in American politics is understandable but misguided. While the desire to refocus on domestic renewal is justified, retreating from the world will not bring the security, prosperity, or sovereignty that its proponents promise. On the contrary, it invites instability, diminishes U.S. influence, and erodes the democratic order the U.S. helped forge.
Fragmented by Design: USAID’s Dismantling and the Future of American Foreign Aid
The Trump administration launched an aggressive restructuring of U.S. foreign aid, effectively dismantling the United States Agency for International Development (USAID). The humanitarian and geopolitical fallout of the demise of USAID includes shuttered clinics, destroyed food aid, and China’s growing influence in the global south. This new era of American soft power will determine how, and whether, the U.S. continues to lead in global development.
Water Wars: A Historic Agreement Between Mexico and US Is Ramping Up Border Tension
As climate change drives rising temperatures and changes in rainfall, Mexico and the US are in the middle of a conflict over water, putting an additional strain on their relationship. Partly due to constant droughts, Mexico has struggled to maintain its water deliveries for much of the last 25 years, deliveries to which it is obligated by a 1944 water-sharing agreement between the two countries.
How Disastrous Was the Trump-Putin Meeting?
In Alaska, Trump got played by Putin. Therefore, Steven Pifer writes, the European leaders and Zelensky have to “diplomatically offer suggestions to walk Trump back from a position that he does not appear to understand would be bad for Ukraine, bad for Europe, and bad for American interests. And they have to do so without setting off an explosion that could disrupt U.S.-Ukrainian and U.S.-European relations—all to the delight of Putin and the Kremlin.”
How Male Grievance Fuels Radicalization and Extremist Violence
Social extremism is evolving in reach and form. While traditional racial supremacy ideologies remain, contemporary movements are now often fueled by something more personal and emotionally resonant: male grievance.
