-
U.K.’s first research institute to investigate the science of cyber security
A new U.K. academic research institute, aiming to improve understanding of the science behind the growing cybersecurity threat, was announced last week; GCHQ, the U.K. intelligence agency, says that the institute, which is funded by a £3.8 million grant, is part of a cross-government commitment to increasing the U.K. academic capability in all fields of cybersecurity
-
-
Thorium to play limited role in U.K. future power supply
Worldwide, there has for a long time been a sustained interest in the thorium fuel cycle and presently there are several major research initiatives which are either focused specifically on the thorium fuel cycle or on systems which use thorium as the fertile seed instead of U-238; the U.K. National Nuclear Laboratory examined the topic and concluded that thorium has theoretical advantages but that these benefits are often overstated; as a result, thorium fuel cycle at best has only limited relevance to the United Kingdom as a possible alternative plutonium disposition strategy and as a possible strategic option
-
-
China’s nuclear strategy too risky: experts
Beijing’s nuclear missiles exist to deter a nuclear first strike on China, and are only to be used in extremis; at the same time, conventional weapons — including missiles with conventional warheads – located on formerly all-nuclear bases must be ready to strike first and hard; targeted enemies and their allies will not immediately be able to distinguish whether any missiles launched from these bases are conventional or nuclear
-
-
U.S. sends two guided missile destroyers, more drones, to Libya

The United States is increasing its military and intelligence presence in and around Libya – on the ground, in the air, and at sea; in addition to helping the Libyan authorities hunt down the members of the cell which attacked the consulate, the United States is increasing its surveillance of Islamic militants in eastern Libya, with the al Qaeda-linked Imprisoned Omar Abdul Rahman Brigades considered to be the main culprit behind the consulate attack, and behind Islamic terrorism in Libya more generally; drone strikes against militants in Libya, similar to the drone strikes in Pakistan, Yemen, and Somalia, should be initiated sooner rather than later
-
-
DHS, FBI warn of the “risk of violence” in wake of movie controversy; movie producer’s identity revealed

The FBI and DHS yesterday issued a Joint Intelligence Bulletin which warned faith-based organizations in the United States and U.S. embassies abroad that “the risk of violence could increase both at home and abroad as the film continues to gain attention”
-
-
Details, timeline of attack on Benghazi compound emerge
The details and time line of the assault on the U.S. diplomatic compound in Benghazi raises questions about whether internal and external security arrangements were sufficient; the relative ease with which the assailants managed to enter the compound, and then shoot their way from building to building, suggests that there were not enough security guards to protect the compound; but there are also questions about the security arrangements between the United States and Libya. It is not clear why it took the Libyan government – or the local police – nearly four hours to respond: the assault began at 10:00 p.m., but Libyan units did not arrive in force until 2:00 a.m.
-
-
U.S. Middle East embassies under attack
Three U.S. embassies in the Middle East and North Africa came under attack on Tuesday and Wednesday; the attacks, in Cairo, Benghazi, and Sanaa, have raised different questions; the attack in Cairo, which saw a score of ultraislamist demonstrators scale the walls of the embassy and pull down the U.S. flag, raised questions about a press release issued by the embassy, a release which, some charged, appeared to be more concerned with the hurt feelings of Muslims than with the security of U.S. personnel and the rule of law; the Benghazi attack raised questions of a more operational nature, concerning intelligence and protection
-
-
Are Americans safer today than they were four years ago?

The presidential campaign is dominated by economic issues, so the question the two candidates invite their audience to ponder is: “Are you better off now than four years ago?”; the question “Are you safer today than you were four years ago” is hardly, if ever, posed; security experts agree that while security challenges posed by China, Iran, and Islamists in Africa have grown, Americans are safer today than they were four years ago because the Obama administration, relative to its predecessor and, has pursued the campaign against terrorism and terrorists more aggressively and more single-mindedly; sustained drone strikes and secretive special operations have weakened al Qaeda considerably over the last four years
-
-
Forensic science in the dock
Two members of O. J. Simpson’s defense team founded the Innocence Project in 1992; since then, the project has helped exonerate almost 300 innocent people by challenging improper use of DNA testing and other elements of forensic science
-
-
Himalayan glaciers retreating at an uneven rate, making South Asia water supply future unclear

MI6, the U.K. intelligence service, four years ago predicted that the world’s first water war – that is, war between countries over access to water resources — will take place between India and Bangladesh sometime between 2015 and 2020; the reason for the war: intensifying conflicts over dwindling Himalayas water sources; glaciers in the eastern and central regions of the Himalayas appear to be retreating at accelerating rates, similar to those in other areas of the world, while glaciers in the western Himalayas are more stable and could be growing, a new report says
-
-
Serious limitations make boost-phase missile interception impractical
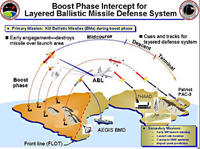
One of the central elements of President Reagan’s 1983 “Star Wars” ballistic missile defense initiative was boost-phase defense: boost-phase defense systems are intended to shoot down enemy missiles immediately following launch while the rocket engine is still firing; a new congressionally mandated study by the National Research Council study says that to defend against ballistic missile attacks more effectively, the United States should concentrate on defense systems that intercept enemy missiles in midcourse and stop spending money on boost-phase defense systems of any kind
-
-
In Pakistan, stronger support for militant groups among the middle class than the poor

Expectations that poorer people are more susceptible to the appeals of violent groups have contributed to U.S. policies that focus on using aid to reduce poverty as a way to combat militant violence; a new survey found, however, that the poor in Pakistan were substantially more negative toward militant groups than their middle class countrymen
-
-
More traffic deaths following 9/11
In the wake of the terrorist attacks of 11 September 2001, many Americans started driving more due to a fear of flying — and lost their lives in traffic accidents; why did this happen more frequently in some states than in others? Why did Spanish driving habits not change in the same way following the 2004 train bombings in Madrid? Psychologists offer an answer
-
-
Lawmakers threaten Pakistan aid unless jailed Pakistani doctor is released

Senator Rand Paul (R-Kentucky) is threatening to hold up Senate business unless a discussion is scheduled on the fate of the jailed Pakistani doctor Shakil Afridi, who helped the United States locate Ossama bin Laden; Paul has been working for a month to bring the issue of U.S. aid to Pakistan to a vote – and he is gathering support for a vote on freezing all aid to Pakistan until Afridi is freed
-
-
The historical and future probabilities of 9/11-size terrorist events
On the eleventh anniversary of the 9/11 attacks, two statisticians apply statistical methods to try and accurately estimate the probability of a 9/11-size terrorist attack occurring during the next decade; examining the historical data from 1968 to 2007, they show that the likelihood of a 9/11-size attack occurring within this time frame was between 11 and 35 percent; looking forward, the likelihood increase to between 25 and 50 percent – and, under certain circumstances, to 95 percent
-
More headlines
The long view
Factories First: Winning the Drone War Before It Starts
Wars are won by factories before they are won on the battlefield,Martin C. Feldmann writes, noting that the United States lacks the manufacturing depth for the coming drone age. Rectifying this situation “will take far more than procurement tweaks,” Feldmann writes. “It demands a national-level, wartime-scale industrial mobilization.”
No Nation Is an Island: The Dangers of Modern U.S. Isolationism
The resurgence of isolationist sentiment in American politics is understandable but misguided. While the desire to refocus on domestic renewal is justified, retreating from the world will not bring the security, prosperity, or sovereignty that its proponents promise. On the contrary, it invites instability, diminishes U.S. influence, and erodes the democratic order the U.S. helped forge.
Fragmented by Design: USAID’s Dismantling and the Future of American Foreign Aid
The Trump administration launched an aggressive restructuring of U.S. foreign aid, effectively dismantling the United States Agency for International Development (USAID). The humanitarian and geopolitical fallout of the demise of USAID includes shuttered clinics, destroyed food aid, and China’s growing influence in the global south. This new era of American soft power will determine how, and whether, the U.S. continues to lead in global development.
Water Wars: A Historic Agreement Between Mexico and US Is Ramping Up Border Tension
As climate change drives rising temperatures and changes in rainfall, Mexico and the US are in the middle of a conflict over water, putting an additional strain on their relationship. Partly due to constant droughts, Mexico has struggled to maintain its water deliveries for much of the last 25 years, deliveries to which it is obligated by a 1944 water-sharing agreement between the two countries.
How Disastrous Was the Trump-Putin Meeting?
In Alaska, Trump got played by Putin. Therefore, Steven Pifer writes, the European leaders and Zelensky have to “diplomatically offer suggestions to walk Trump back from a position that he does not appear to understand would be bad for Ukraine, bad for Europe, and bad for American interests. And they have to do so without setting off an explosion that could disrupt U.S.-Ukrainian and U.S.-European relations—all to the delight of Putin and the Kremlin.”
How Male Grievance Fuels Radicalization and Extremist Violence
Social extremism is evolving in reach and form. While traditional racial supremacy ideologies remain, contemporary movements are now often fueled by something more personal and emotionally resonant: male grievance.
