-
Democrats brace for more e-mail leaks
The FBI on Monday said the agency is investigating the hacks of the DNC computer networks. Democrats are worried that the Russian government hackers behind the DNC hacks may have gotten their hands on other politically embarrassing e-mails and documents, and the hackers would release these e-mails and documents between now and November in an effort to increase Trump’s chances of winning in November. Julian Assange, the founder of WikiLeaks and its current top editor, who said that the release [of the DNC e-mails] on Friday was the first in a series.
-
-
U.S. to issue new policy directive for coordinated government response to cyberattacks
The administration is set to release a new directive on how the government should respond to significant cyberattacks. The release of the directives aims to clarify the responsibilities of agencies involved in security breaches. The presidential directive comes against the backdrop of an increasing number of cyberattacks by criminals and foreign governments.
-
-
Russian government hackers leaked DNC e-mails: Cybersecurity experts

Robby Mook, Hillary Clinton’s campaign manager, said on Sunday that Friday’s release by WikiLeaks of Democratic National Committee (DNC) internal e-mails was the work of Russian government hackers. The leak, Mook said, was part of an effort by President Vladimir Putin and people in his circle to weaken Clinton and increase the chances of a Donald Trump victory in November. Cybersecurity experts support Mook’s claims.
-
-
DHS S&T awards $3.66 million for privacy-enhancing technology R&D
DHS S&T has announced the award of three contracts totaling $3.66 million to fund the research and development of privacy-enhancing technologies that better defend personally identifying information and protect privacy in cyber space.
-
-
Protecting against “browser fingerprint”
Imagine that every time a person goes out in public, they leave behind a track for all to see, so that their behavior can be easily analyzed, revealing their identity. This is the case with people’s online browser “fingerprints,” which are left behind at each location they visit on their internet browser. Almost like a regular fingerprint, a person’s browser fingerprint — or “browserprint” — is often unique to the individual. Such a fingerprint can be monitored, tracked, and identified by companies and hackers.
-
-
Automated cybersecurity systems get set for final face-off at DARPA’s Cyber Grand Challenge
The Heartbleed security bug existed in many of the world’s computer systems for nearly two-and-a-half years before it was discovered and a fix circulated in the spring of 2014. The reason for this time lag? In contrast to the sophistication and automation that characterize so much of today’s computer systems, the process of finding and countering bugs, hacks, and other cyber infection vectors is still effectively artisanal. But what if that system of finding and fixing flaws were just as fast and automated as the computer systems they are trying to protect? What if cyber defense were as seamless, sophisticated, and scalable as the Internet itself? These are questions at the heart of DARPA’s Cyber Grand Challenge.
-
-
DHS seeking input to study safeguards to mobile devices
DHS is seeking input from the mobile and cellular industry to study defense capability gaps and additional safeguards for government devices. The DHS S&T will additionally hold two Industry Day events – 20 July in Washington, D.C. and 2 August in Menlo Park, California — to provide additional insight about the request for information (RFI) to the mobile and cellular industry and researchers.
-
-
Cybersecurity risks in 3D printing
Additive manufacturing (AM), commonly called 3D printing, is a $4 billion business set to quadruple by 2020. One day, manufacturers may print everything from cars to medicines, disrupting centuries-old production practices. But the new technology poses some of the same dangers unearthed in the electronics industry, where trusted, partially trusted, and untrusted parties are part of a global supply chain. Researchers report of their examination of two aspects of 3D printing that have cybersecurity implications: printing orientation and insertion of fine defects.
-
-
Better computer bug finder

Individuals and corporations spend millions of dollars every year on software that sniffs out potentially dangerous bugs in computer programs. And whether the software finds ten bugs or 100, there is no way determine how many go unnoticed, nor to measure the efficacy of bug-finding tools. Researchers are taking an unorthodox approach to tackling this problem: Instead of finding and remediating bugs, they are adding them by the hundreds of thousands.
-
-
How to stay anonymous online
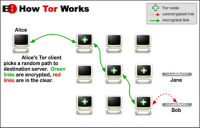
Anonymity networks protect people living under repressive regimes from surveillance of their Internet use. But the recent discovery of vulnerabilities in the most popular of these networks — Tor — has prompted computer scientists to try to come up with more secure anonymity schemes. These scientists have developed a new anonymity scheme that provides strong security guarantees but uses bandwidth much more efficiently than its predecessors, making it possible for network to protect users’ anonymity if all but one of its servers are compromised.
-
-
Increasing power grid cybersecurity

Cybersecurity experts are leading a new program to develop new data analysis methods better to protect the nation’s power grid. The goal of this project is to develop technologies and methodologies to protect the grid from advanced cyber and threats by developing the means to distinguish between power grid failures caused by cyber attacks and failures caused by other means, including natural disasters, “normal” equipment failures, and even physical attacks.
-
-
Ending extortion: Researchers develop a way to stop ransomware

Ransomware — what hackers use to encrypt your computer files and demand money in exchange for freeing those contents — is an exploding global problem with few solutions. The FBI issued a warning in May saying the number of attacks has doubled in the past year and is expected to grow even more rapidly this year. It said it received more than 2,400 complaints last year and estimated losses from such attacks at $24 million last year for individuals and businesses. Researchers have developed a way to stop ransomware dead in its tracks.
-
-
Your smart watch and fitness tracker may give away your PIN
Wearable devices — Fitbits, Jawbones, Nike+, Apple Watches, and the like — are white-hot. The tech segment is already producing an estimated $14 billion in sales worldwide, and expected to more than double within four years, climbing to north of $30 billion. But a new research report reveals those cool wearables just may leak information as you use them.
-
-
DHS S&T funds efforts to make Internet of Things safer
DHS S&T the other day awarded $119,000 to Ionic Security, Inc. based in Atlanta, Georgia, to advance detection and monitoring for Internet of Things (IoT) systems security. The Ionic Security team proposes to apply a novel distributed data protection model to solve the authentication, detection, and confidentiality challenges that impact distributed IoT devices.
-
-
Effective defense against Internet attacks
The brute force and sheer scale of current Internet attacks put a heavy strain on classic methods of intrusion detection. Moreover, these methods are not prepared for the rapidly growing number of connected devices. Researchers have developed a “flow based” approach, which looks at the data flow from a higher level and detects suspicious patterns.
-
- All
- Regional
- Water
- Biometrics
- Borders/Immig
- Business
- Cybersecurity
- Detection
- Disasters
- Government
- Infrastructure
- International
- Public health
- Public Safety
- Communication interoperabillity
- Emergency services
- Emergency medical services
- Fire
- First response
- IEDs
- Law Enforcement
- Law Enforcement Technology
- Military technology
- Nonlethal weapons
- Nuclear weapons
- Personal protection equipment
- Police
- Notification /alert systems
- Situational awareness
- Weapons systems
- Sci-Tech
- Sector Reports
- Surveillance
- Transportation
Advertising & Marketing: advertise@newswirepubs.com
Editorial: editor@newswirepubs.com
General: info@newswirepubs.com
2010-2011 © News Wire Publications, LLC News Wire Publications, LLC
220 Old Country Road | Suite 200 | Mineola | New York | 11501
Permissions and Policies
Editorial: editor@newswirepubs.com
General: info@newswirepubs.com
2010-2011 © News Wire Publications, LLC News Wire Publications, LLC
220 Old Country Road | Suite 200 | Mineola | New York | 11501
Permissions and Policies
