-
Improving cybersecurity, reducing online theft
NIST the other day announced it will award nearly $3.7 million for three pilot projects designed to make online transactions more secure and privacy-enhancing for healthcare, government services, transportation, and the Internet of Things. The three recipients of the National Strategy for Trusted Identities in Cyberspace (NSTIC) grants will pilot solutions aimed at reducing tax refund theft, improving the security of medical information and providing secure online data storage.
-
-
Clearance of employees who repeatedly fall for phishing scams should be revoked: Experts
People are one vital component in the 3P security system (the others being process and product). Some of the people who handle sensitive government information also continue to fall for human engineering techniques like phishing. The question is: should the individuals who repeatedly fall for these scams have their security clearance revoked? Absolutely they should, maintains DHS chief security officer (CIS) Paul Beckman.
-
-
Beyond data theft: Next phase of cyber intrusions will include destruction, manipulation of data
James Clapper, director of U.S. intelligence, and other senior intelligence officers, have warned Congress that the next phase of escalating online data theft will likely involve the manipulation of digital information. Clapper on Wednesday told lawmakers on the House Intelligence Committee that a “cyber Armageddon,” in which a digitally triggered damage to physical infrastructure results in a series of catastrophic events, is less likely than “cyber operations that will change or manipulate data.” Leaders of the U.S. intelligence community told lawmakers that the manipulation or destruction of data would undermine confidence in data stored on or accessible through U.S. networks, engendering an uncertainty which could jeopardize U.S. military situational awareness and undermine business activity.
-
-
Smart watches allow hackers to harvest users’ data

They are the latest rage in jewelry and gadgetry, but like all computer devices, smart watches are vulnerable to hackers. Using a homegrown app on a Samsung Gear Live smart watch, researchers were able to guess what a user was typing through data “leaks” produced by the motion sensors on smart watches. The project, called Motion Leaks through Smartwatch Sensors, or MoLe, has privacy implications, as an app that is camouflaged as a pedometer, for example, could gather data from emails, search queries and other confidential documents.
-
-
Securing and protecting the emerging Internet of Things

The digital world once existed largely in non-material form. But with the rise of connected homes, smart grids and autonomous vehicles, the cyber and the physical are merging in new and exciting ways. These hybrid forms are often called cyber-physical systems (CPS), and are giving rise to a new Internet of Things. National Science Foundation and Intel Corporation team to improve the security and privacy of computing systems that interact with the physical world using a new cooperative research model.
-
-
Strategic alliance to deliver behavioral analysis cybersecurity to market
Ernst & Young LLP and Los Alamos National Laboratory have formed a strategic alliance to deliver what they describe as some of the most advanced behavioral cybersecurity tools available to the commercial market. The alliance comes at a watershed moment when increasingly sophisticated cyberattacks are inflicting significant economic, social, and even political damage to U.S. organizations. The tools developed by Los Alamos and delivered to the private sector by Ernst & Young LLP can help counter these threats by detecting them before they do deep and lasting damage.
-
-
Power safety in data centers
Power and thermal management have become a critical priority in data centers, which can use as much electricity as a small town. Energy and power vulnerabilities pose serious security threats to data centers, but so far little has been done to address these issues. A DHS grant will allow researchers to investigate energy and power safety in data centers.
-
-
DHS S&T awards $10.4 million in mobile security research contracts
The mobile technology industry has continuously expanded with new devices and apps, allowing people to simplify how and where business is conducted. While increasing the use of mobile technology can enhance productivity, improved security is needed to ensure that sensitive information is not at risk to current and emerging cyber threats. DHS S&T the other day announced $10.4 million in cybersecurity Mobile Technology Security (MTS) research and development (R&D) awards to enhance the security of mobile devices for the federal government.
-
-
DHS S&T awards U Oregon a 1.38M contract for DDoS research

DDoS attacks are used to render key resources unavailable. A typical DDoS attack might disrupt an organization’s Web site and temporarily block a consumer’s ability to access the site. A more strategic attack could make a key resource inaccessible during a critical period. DHS S&T awarded a $1.38 million contract to the University of Oregon to create technology to defend against large and sophisticated Distributed Denial of Service (DDoS) attacks. The University of Oregon’s DrawBridge project will become part of the DHS S&T Cyber Security Division’s larger DDoSD program.
-
-
Draft guide to help energy companies reduce cyber risk

DHS reported that 5 percent of the cybersecurity incidents its Industrial Control Systems Cyber Emergency Response Team responded to in fiscal year 2014 were tied to weak authentication. Four percent were tied to abuse of access authority. The National Cybersecurity Center of Excellence (NCCoE) is requesting comments on a draft guide to help energy companies better control who has access to their networked resources, including buildings, equipment, information technology, and industrial control systems.
-
-
Calif. state auditor: Many state entities vulnerable to cyberattack, disruption

In the past few years, retailers, financial institutions, and government agencies have increasingly fallen victim to cyberattacks. California state auditor says that given the size of California’s economy and the value of its information, the state presents a prime target for similar information security breaches. Despite the need to safeguard the state’s information systems, the state auditor says that its review found that many state entities have weaknesses in their controls over information security. These weaknesses leave some of the state’s sensitive data vulnerable to unauthorized use, disclosure, or disruption.
-
-
DHS S&T awards Mobile Technology Security (MTS) research grants
The Department of Homeland Security (DHS) Science and Technology Directorate (S&T) on Monday announced a $759,727 cybersecurity Mobile Technology Security (MTS) research and development (R&D) award which will help secure mobile devices for the federal government. The goal of the next-generation mobile security management tools project is to look at innovative technology solutions which protect the operating layer of the mobile device, but also incorporate user identities and actions to protect against vulnerabilities.
-
-
U.S. should promote international cybersecurity standardization: Interagency report
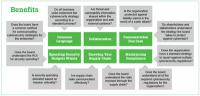
A new draft report by an interagency working group lays out objectives and recommendations for enhancing the U.S. government’s coordination and participation in the development and use of international standards for cybersecurity. The report recommends the government make greater effort to coordinate the participation of its employees in international cybersecurity standards development to promote the cybersecurity and resiliency of U.S. information and communications systems and supporting infrastructures. These efforts should include increased training, collaborating with private industry and working to minimize risks to privacy.
-
-
Hackers exploit flaws in mobile phones’ security
Owners of smartphones have developed a sense of security, using them as if they were sitting in front of their computers at home. Once used for voice transmission only, mobile phones, or smartphones, have grown to become devices used for shopping, bill paying, bank transactions, and a host of other applications. Unfortunately, they are not nearly as secure as most users think they are. Hackers have found a number of flaws, and are capable of exploiting them.
-
-
Securing data from attacks by ever more powerful supercomputers

For the powerful quantum computers that will be developed in the future, cracking online bank account details and credit cards number will be a cinch. But a team of cryptographers is already working at future-proofing the privacy of today’s Internet communications from tomorrow’s powerful computers. The researchers have developed upgrades to the Internet’s core encryption protocol that will prevent quantum computer users from intercepting Internet communications.
-
- All
- Regional
- Water
- Biometrics
- Borders/Immig
- Business
- Cybersecurity
- Detection
- Disasters
- Government
- Infrastructure
- International
- Public health
- Public Safety
- Communication interoperabillity
- Emergency services
- Emergency medical services
- Fire
- First response
- IEDs
- Law Enforcement
- Law Enforcement Technology
- Military technology
- Nonlethal weapons
- Nuclear weapons
- Personal protection equipment
- Police
- Notification /alert systems
- Situational awareness
- Weapons systems
- Sci-Tech
- Sector Reports
- Surveillance
- Transportation
Advertising & Marketing: advertise@newswirepubs.com
Editorial: editor@newswirepubs.com
General: info@newswirepubs.com
2010-2011 © News Wire Publications, LLC News Wire Publications, LLC
220 Old Country Road | Suite 200 | Mineola | New York | 11501
Permissions and Policies
Editorial: editor@newswirepubs.com
General: info@newswirepubs.com
2010-2011 © News Wire Publications, LLC News Wire Publications, LLC
220 Old Country Road | Suite 200 | Mineola | New York | 11501
Permissions and Policies
