-
How computer worms are spreading among smartphones
Researchers have recently discovered that some of the most common activities among smartphone users — scanning 2D barcodes, finding free Wi-Fi access points, sending SMS messages, listening to MP3 music, and watching MP4 videos — can leave devices vulnerable to harmful “computer worms.” These worms can infiltrate smartphones through apps designed in a specific computer language/code — and they can do more harm than just steal the device owner’s personal information, researchers warn. They can also spread to the owner’s friends and personal contacts.
-
-
Feds struggle to plug power grid security holes
Many of the current vulnerabilities in the power grid are attributable to newly adopted smart-grid technology, which allows operators to transmit energy from a diverse pool of resources. Smart-grid technology relies on devices in remote locations which constantly communicate with substations, those access points can be compromised by hackers.
-
-
DHS repairing internal security operations
Last week DHS announced plans to overhaul its security operations center (SOC), the organization which protects DHS’ internal networks, and deploy a Next Generation Enterprise Security Operations Center (NextGen ESOC) which will incorporate state-of-the-art SOC technologies, concepts, and capabilities to address future security needs.
-
-
Measuring smartphone malware infection rates
Researchers show that infection rates in Android devices at around 0.25 percent are significantly higher than the previous independent estimate. They also developed a technique to identify devices infected with previously unknown malware.
-
-
Student develops new way to detect hackers
A Binghamton U student and her teammates are working on developing a new hacking detection solution. Instead of reviewing all programs run by a network to find the signature of one of millions of known malware programs — some of which mutate to avoid detection — they have developed a technology to assess behavior of individual computers. This is done by monitoring system calls, the internal signals that accompany every computer operation and can reveal every function performed by the computer.
-
-
U.S. Cyber Challenge opens registration for Cyber Quests competition
Last week the Council on CyberSecurity, through the U.S. Cyber Challenge (USCC) initiative, announces the open registration of its qualifying Cyber Quests competition — a challenging online contest open to high school and college students, as well as professionals, who will compete against their peers across the country for an invitation to one of four Cyber Camps being offered this summer. The online competition and camps are designed to improve cybersecurity skills, provide training and mentorship from leading instructors and highlight skills for potential employers.
-
-
Making quantum cryptography suitable for mobile phones
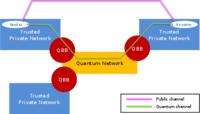
Secure mobile communications underpin our society and through mobile phones, tablets and laptops we have become online consumers. The security of mobile transactions is obscure to most people but is absolutely essential if we are to stay protected from malicious online attacks, fraud and theft. Researchers have shown how it is possible to make the resources necessary for quantum cryptography less bulky and expensive, and thus more suitable for mobile handsets.
-
-
Capabilities-based – rather than actuarial -- risk analysis would make businesses safer
Many businesses and organizations, when applying cost-benefit analysis and a risk-management analysis to measure cyber risk, are relying on the assumption that the likelihood of a future attack depends heavily on how many attacks have occurred in the past. Since there has yet to be a full-scale attack on critical infrastructure in the United States, it is simple to conclude that the risk of a cyberattack on critical infrastructure is low, therefore justifying low investment in additional security initiatives. An actuarial risk analysis may conclude that there is little likelihood of such as attack occurring, but a capabilities-based risk analysis recognizes that since adversaries are capable of such an attack, it is in an organization’s best interest to secure against it.
-
-
Cryptolocker has you between a back-up and a hard place
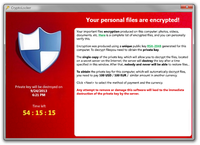
Cryptolocker, a particularly vicious form of malware that first appeared in September 2013, is a game-changer. After getting into your computer, it will encrypt all your data files, from your word documents to your photos, videos, and PDFs. It will then ask for a ransom of around $300 or 0.5 bitcoins to get them back. It has been one of the most commented developments in computer security circles in recent times, and copycats are appearing. The criminals are netting tens or hundreds of millions in ransoms, and at least some of the ill-gotten gains secured from Cryptolocker are likely to be reinvested. The criminals behind it will likely pay for access to bigger botnets to reach a wider base of victims. Future versions of the virus will in all likelihood be more prevalent and will extend across other platforms, like smartphones and tablets.
-
-
Delaware launches cyber initiative
Delaware is joining the number of states that have decided to invest in a statewide cybersecurity workforce to combat the growing threat of cyberattacks directed at both private and public institutions.Delaware hopes its cyber initiative will accelerate current efforts to develop a stronger cyber workforce. The Delaware Cyber Initiative proposes $3 million for a collaborative learning and research network in the form of part research lab, part business park, dedicated to cyber innovation.
-
-
Protecting personal data on smartphone
Social networking and the instantaneous sharing of information have revolutionized the way we communicate. Our mobile phones are able to automatically obtain information such as our current location and activities. This information can be easily collected and analyzed to expose our private life. What is even more malicious is that the personal data contained in our smartphones can be disclosed via installed applications without our being informed.
-
-
Quantum mechanics may lead to ultra-secure Internet
In 1935 Einstein and researchers highlighted a “spooky” theory in quantum mechanics, which is the strange way entangled particles stay connected even when separated by large distances. In the 1990s, scientists realized you can securely transmit a message through encrypting and using a shared key generated by Einstein’s strange entanglement to decode the message from the sender and receiver. Using the quantum key meant the message was completely secure from interception during transmission.
-
-
Making the grid smarter makes it more vulnerable to hackers
The U.S. electric grid is constantly under attack despite attempts by utilities to boost physical security and cyberdefenses. In 2013 a DHS cyber emergency team responded to more than eighty incidents involving energy companies. “If you’re a utility today, depending on your scale, you’re under attack at this moment,” says Robert Weisenmiller, chairman of the California Energy Commission.
-
-
“Hacker schools” grow to meet growing demand for programmers
The increasing demand for computer programmers in the job market has led to the growth of “hacker schools,” an alternative to traditional education that offers students a quicker, cheaper, and effective way to learn computer programing. Hacker schools do not offer certificates or diplomas, instead they target students who currently have degrees in other fields but who want a career change.
-
-
Universities struggle to balance cybersecurity, openness
Since January 2013, more than fifty academic institutions across the country have been targets of cyberattacks, compromising personal information and intellectual property. Unlike other organizations, universities cannot mandate what devices are used to access their networks, and they must accommodate faculty, students, and researchers spread across the globe. Academic network systems are attractive to hackers because they contain valuable intellectual property.
-
- All
- Regional
- Water
- Biometrics
- Borders/Immig
- Business
- Cybersecurity
- Detection
- Disasters
- Government
- Infrastructure
- International
- Public health
- Public Safety
- Communication interoperabillity
- Emergency services
- Emergency medical services
- Fire
- First response
- IEDs
- Law Enforcement
- Law Enforcement Technology
- Military technology
- Nonlethal weapons
- Nuclear weapons
- Personal protection equipment
- Police
- Notification /alert systems
- Situational awareness
- Weapons systems
- Sci-Tech
- Sector Reports
- Surveillance
- Transportation
Advertising & Marketing: advertise@newswirepubs.com
Editorial: editor@newswirepubs.com
General: info@newswirepubs.com
2010-2011 © News Wire Publications, LLC News Wire Publications, LLC
220 Old Country Road | Suite 200 | Mineola | New York | 11501
Permissions and Policies
Editorial: editor@newswirepubs.com
General: info@newswirepubs.com
2010-2011 © News Wire Publications, LLC News Wire Publications, LLC
220 Old Country Road | Suite 200 | Mineola | New York | 11501
Permissions and Policies
