-
N.C. panel to issue sea-level rise forecast to guide coastal, infrastructure development
Scientists with the North Carolina Coastal Resources Commission(CRC) will have their last public meeting today (Monday) before the group issues its projections on sea level rise around the state’s coastal areas. In a 2010 forecast, the science panel concluded that North Carolina’s sea levels would increase by thirty-nine inches by 2100. Climate-change skeptics and coastal developers opposed the report, and in 2012 persuaded the state legislature to bar any state agency from adopting a policy based on any sea level forecast. The legislature modified the CRC’s mandate by limiting its projections to 30-year periods and instructing it to focus on four separate zones and not the entire state projections. The CRC will submit it report to the legislature on 1 March 2016.
-
-
Ultrasonic robot inspects pipes at nuclear power plant
GE Hitachi Nuclear Energy (GEH) the other day announced that its ultrasonic robot, Surveyor, successfully inspected a section of underground pipe at the South Texas Project Electric Generating Station. The inspection at the site of two Westinghouse-built pressurized water reactors near Bay City, Texas, marks the first deployment of the state-of-the-art robot at a nuclear power plant.
-
-
Florida's First Coast region trying to cope with rising seas
City planners in Florida’s First Coast region are taking steps to avoid massive destruction to property and human life as sea level rise is expected to cause mass flooding and super storms during the next few decades. Some groups are lobbying for coastal property-insurance reforms, while others are researching ways to help historic properties manage flooding.
-
-
Exploring ways to deal with Great Lakes water-level changes

Extreme water-level fluctuations in the Great Lakes, including historic lows on lakes Michigan and Huron in 2013 and substantial upward trends in 2014, are creating serious challenges for many shoreline property owners, tourism-related businesses, municipal planners, and others. To help these community decision makers determine the best strategies for dealing with these water-level changes, a two-tiered, two-year research initiative has been launched with the goal of developing information, tools, and partnerships to help decision makers address challenges and opportunities posed by water-level variability.
-
-
Turning excess space into apartments as an incentive for earthquake-retrofitting of buildings
San Francisco is dealing with a housing shortage at the same time that city officials are trying to get landlords to retrofit buildings which are at risk of crumpling during a severe earthquake. In 2013, Mayor Ed Lee approved a bill that mandates retrofits for soft-story multi-unit residential buildings over the next four to seven years. Roughly 4,800 buildings of two or more stories, containing five or more apartment units, which were approved for construction before January 1978, have to be retrofitted, according to the mandate.A member of San Francisco’s Board of Supervisors, recently proposed that building owners of at-risk apartment buildings be allowed to finance earthquake retrofits by converting garages, basements, and other excess space into apartments –a plan which would also increase the city’s housing stock.
-
-
McAfee Labs report previews 2015 cyber threats, exploits, evasions
McAfee Labs November 2014 Threats Report offers an analysis of threat activity in the third quarter of 2014, and the organization’s annual 2015 Threats Predictions for the coming year. The report details a third quarter filled with threat development milestones and cyber events exploiting long-established Internet trust standards. McAfee Labs forecasts a 2015 threat landscape shaped by more attacks exploiting these standards, new attack surfaces in mobile and Internet of Things (IoT), and increasingly sophisticated cyber espionage capabilities, including techniques capable of evading sandboxing detection technologies.
-
-
Re-thinking Southern California earthquake scenarios
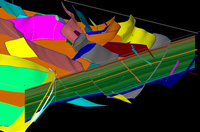
New three-dimensional (3D) numerical modeling that captures far more geometric complexity of an active fault segment in southern California than any other, suggests that the overall earthquake hazard for towns on the west side of the Coachella Valley such as Palm Springs and Palm Desert may be slightly lower than previously believed.
-
-
Coordinated cyberattacks by Iran-based hackers on global critical infrastructure
Irvine, California-based cybersecurity firm Cylance last week released a report detailing coordinated attacks by hackers with ties to Iran on more than fifty targets in sixteen countries around the globe. Victim organizations were found in a variety of critical industries, with most attacks on airlines and airports, energy, oil and gas, telecommunications companies, government agencies and universities.
-
-
Growing cybersecurity threats offer opportunities for cybersecurity businesses
A 2013 report from the U.S. Computer Emergency Readiness Team(US-CERT) noted that the number of cyberattacks reported by federal agencies had skyrocketed 782 percent since 2006, to nearly 49,000, in 2012. Today, the figure is much higher. The increasing threat of cyberattacks from domestic and foreign actors has opened up opportunities for cybersecurity professionals, many of whom held positions with the U.S. military or intelligence agencies. For the private sector, cybersecurity spending is expected to reach $71.1 billion this year, and expected to grow about 9 percent annually through 2016.
-
-
Insurance industry needs support to address effects of climate change on the built environment
A new report finds that the increasing frequency of extreme weather brought on by climate change adversely affects real estate values and increases the probability of property damage occurring in urban areas. In the last ten years alone, direct losses in real estate and infrastructure as a result of natural disasters has tripled, reaching $150 billion per year. The report highlights the steps the insurance industry has taken to adopt risk standards for climate change across the industry, from catastrophe models and scenario analysis to insurance products that incentivize risk-reducing building practices.
-
-
DOJ’s new cyber unit to provide legal guidance on electronic surveillance
The Justice Department is creating a cybersecurity unit within its Computer Crime & Intellectual Property Section (CCIPS) to provide legal guidance on electronic surveillance investigations.The unit will also work with Congress on cybersecurity legislation and focus on cybercrime prevention.
-
-
Micro-capsules and bacteria used in self-healing concrete
Researchers are aiming to develop a novel self-healing concrete that uses an inbuilt immune system to close its own wounds and prevent deterioration. Self-healing concrete could vastly increase the life of concrete structures, and would remove the need for repairs, reducing the lifetime cost of a structure by up to 50 percent. Over seven per cent of the world’s CO2 emissions are caused by cement production, so reducing the amount required by extending the lifetime of structures and removing the need for repairs will have a significant environmental impact.
-
-
CO2 warming effects already felt a decade after being emitted
It takes just ten years for a single emission of carbon dioxide (CO2) to have its maximum warming effects on the Earth. This is according to researchers who have dispelled a common misconception that the main warming effects from a CO2 emission will not be felt for several decades. This means that the benefits from emission reductions — the avoidance of extreme weather events such as droughts, heatwaves, and flooding — will be felt by those who have worked to curb the emissions and not just future generations. Some of the bigger climate impacts from warming, however, such as sea-level rise, melting ice sheets, and long-lasting damage to ecosystems, will have a much bigger time lag.
-
-
Research shows how global warming links to carbon emissions
A team of researchers from the Universities of Liverpool, Southampton, and Bristol have derived the first theoretical equation to demonstrate that global warming is a direct result of the build-up of carbon emissions since the late 1800s, when man-made carbon emissions began. The results are in accord with previous data from climate models. The results show every million-million tons of carbon emitted will generate one degree Celsius of global warming. They also show that the build-up of carbon emitted over the last 200 years will then last for many centuries to millennia even if carbon emissions are subsequently phased out.
-
-
Southeastern Louisiana has a problem: "The sea is rising and the land is sinking"
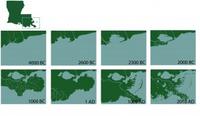
Southeastern Louisiana is drowning at the rate of one football field per hour, totaling up to sixteen square miles annually. In just eighty years, sea level rise, fossil fuel extraction, and having too few wetlands separating the Gulf from the flood protection levee systems have caused some 2,000 square miles of Louisiana’s coastal landscape to sink into the Gulf of Mexico. The issues facing Louisiana’s southeastern coast pose a threat to American energy and economic stability. A $50 billion, 50-year coastal restoration plan, formulated in 2007, is yet to be accepted and funded, but experts note that if sea-level rise is as bad as the worst case scenario, several projects at the heart of the restoration plan would become infective.
-
- All
- Regional
- Water
- Biometrics
- Borders/Immig
- Business
- Cybersecurity
- Detection
- Disasters
- Government
- Infrastructure
- International
- Public health
- Public Safety
- Communication interoperabillity
- Emergency services
- Emergency medical services
- Fire
- First response
- IEDs
- Law Enforcement
- Law Enforcement Technology
- Military technology
- Nonlethal weapons
- Nuclear weapons
- Personal protection equipment
- Police
- Notification /alert systems
- Situational awareness
- Weapons systems
- Sci-Tech
- Sector Reports
- Surveillance
- Transportation
Advertising & Marketing: advertise@newswirepubs.com
Editorial: editor@newswirepubs.com
General: info@newswirepubs.com
2010-2011 © News Wire Publications, LLC News Wire Publications, LLC
220 Old Country Road | Suite 200 | Mineola | New York | 11501
Permissions and Policies
Editorial: editor@newswirepubs.com
General: info@newswirepubs.com
2010-2011 © News Wire Publications, LLC News Wire Publications, LLC
220 Old Country Road | Suite 200 | Mineola | New York | 11501
Permissions and Policies
