-
Feds: We can read all your e-mail, and you’ll never know

Fear of hackers reading private e-mails in cloud-based systems like Microsoft Outlook, Gmail, or Yahoo has recently sent regular people and public officials scrambling to delete entire accounts full of messages dating back years. What we don’t expect is our own government to hack our e-mail — but it’s happening. Federal court cases going on right now are revealing that federal officials can read all your e-mail without your knowledge. For example, in the case of U.S. v. Ravelo, pending in Newark, New Jersey, the government used a search warrant to download the entire contents of a lawyer’s personal cellphone – more than 90,000 items including text messages, e-mails, contact lists, and photos. When the phone’s owner complained to a judge, the government argued it could look at everything (except for privileged lawyer-client communications) before the court even issued a ruling. The judge in Ravelo is expected to issue a preliminary ruling on the feds’ arguments sometime in October. All Americans should be watching carefully to what happens next in these cases – the government may be already watching you without your knowledge.
-
-
Swiss approve broader surveillance powers for the government
A majority of 65.5 percent of Swiss voters have on Sunday approved a new surveillance law, agreeing with the government’s argument that that the country’s security services needed more powers in an increasingly dangerous world. Relative to other European countries, the Swiss police and intelligence agencies have had limited investigative powers. For example, the law which was updated on Sunday had banned phone tapping and e-mail surveillance under any circumstances.
-
-
Fitness trackers found to have serious security flaws

They may look like a normal watch but are capable to do much more than just showing the time: So-called fitness trackers are collecting data on their users’ lifestyle and health status on a large scale helping them with training or losing weight. Researchers have investigated fraud opportunities with fitness trackers and detected serious security flaws.
-
-
FBI director calls for “adult conversation” on encryption – and the privacy-security balance

James Comey, the FBI director, has again said that end-to-end encryption on digital devices makes it impossible for his agency to investigate crimes and acts of terrorism— and called for an “adult conversation” with the manufacturers of these devices. Widespread encryption built into smartphones was “making more and more of the room that we are charged to investigate dark,” Comey said at a cybersecurity symposium.
-
-
Israeli tech company’s spyware turns UAE activist’s iPhone into a self-tracking device
Two University of Toronto researchers have uncovered an iPhone-based attack on Ahmed Mansoor, a prominent United Arab Emirates human rights defender. The attack employed spyware produced by NSO Group — an Israeli technology company founded by former members of Unit 8200, the Israeli military’s electronic surveillance branch – which is sold to government for the purpose of spying on their citizens.
-
-
Many sections of Baltimore are under secret, constant aerial video surveillance by BPD

The Baltimore Police Department has secretly deployed a surveillance system using planes and powerful cameras that can continuously record 30-square-mile sections of the city at once. The technology, which is run by a private company, was originally developed for the Defense Department for use in Iraq. It stores the video footage for an undetermined amount of time, and police can use it to retroactively track any pedestrian or vehicle within the surveillance area.
-
-
Android apps can secretly track users’ whereabouts

Three years ago, the FTC dimmed hopes for the Brightest Flashlight app for Android, slapping its developer with charges of consumer deception, because the app was transmitting users’ locations and device IDs to third parties without telling the users or getting their permission. Permissions, though, are only a small part of the Android-app privacy story. New research shows that Android apps can be manipulated to reach inside your mobile phone to track your whereabouts and traffic patterns, all without your knowledge or consent.
-
-
Protecting privacy in genomic databases
Genome-wide association studies, which try to find correlations between particular genetic variations and disease diagnoses, are a staple of modern medical research. But because they depend on databases that contain people’s medical histories, they carry privacy risks. An attacker armed with genetic information about someone — from, say, a skin sample — could query a database for that person’s medical data. Researchers describe a new system that permits database queries for genome-wide association studies but reduces the chances of privacy compromises to almost zero.
-
-
Live-streaming crime incidents a challenge U.S. privacy law
In July, the fatal police shootings of Alton Sterling and Philando Castile went viral on social media. The aftermath of the Castile shooting was first shared via Facebook Live, which is a type of mobile streaming video technology (MSVT) that allows users to stream live video to followers, similar to Periscope and Meerkat. The two incidents focus attention on the legal rights of people to record and live stream and any potential right to be free from being recorded and streamed in public places.
-
-
DHS S&T awards $3.66 million for privacy-enhancing technology R&D
DHS S&T has announced the award of three contracts totaling $3.66 million to fund the research and development of privacy-enhancing technologies that better defend personally identifying information and protect privacy in cyber space.
-
-
Protecting against “browser fingerprint”
Imagine that every time a person goes out in public, they leave behind a track for all to see, so that their behavior can be easily analyzed, revealing their identity. This is the case with people’s online browser “fingerprints,” which are left behind at each location they visit on their internet browser. Almost like a regular fingerprint, a person’s browser fingerprint — or “browserprint” — is often unique to the individual. Such a fingerprint can be monitored, tracked, and identified by companies and hackers.
-
-
How to stay anonymous online
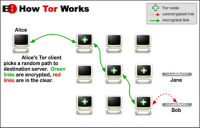
Anonymity networks protect people living under repressive regimes from surveillance of their Internet use. But the recent discovery of vulnerabilities in the most popular of these networks — Tor — has prompted computer scientists to try to come up with more secure anonymity schemes. These scientists have developed a new anonymity scheme that provides strong security guarantees but uses bandwidth much more efficiently than its predecessors, making it possible for network to protect users’ anonymity if all but one of its servers are compromised.
-
-
Your smart watch and fitness tracker may give away your PIN
Wearable devices — Fitbits, Jawbones, Nike+, Apple Watches, and the like — are white-hot. The tech segment is already producing an estimated $14 billion in sales worldwide, and expected to more than double within four years, climbing to north of $30 billion. But a new research report reveals those cool wearables just may leak information as you use them.
-
-
House committee releases encryption report, laying foundation for a national dialogue

Terrorist attacks in Paris and San Bernardino have sparked a public debate on the use of encryption in the United States because the attackers used encrypted communications to evade detection, a phenomenon known as “going dark.” Earlier this week, the Majority Staff of the House Homeland Security Committee released a new report, titled Going Dark, Going Forward: A Primer on the Encryption Debate. The summarizes the committee’s findings, based on more than 100 meetings and briefings committee staff and members have held with key stakeholders over the past year.
-
-
Weak spots in Europe’s “Right to be Forgotten” data privacy law
Under Europe’s “Right to be Forgotten” law, citizens there can petition Internet search providers such as Google to remove search results linked to personal information that is negative or defamatory. In many cases, these links lead to information about accusations of criminal activity or financial difficulties, which may be “delisted” if the information is erroneous or no longer relevant. But “gone” doesn’t always mean “forgotten,” according to a new study.
-
- All
- Regional
- Water
- Biometrics
- Borders/Immig
- Business
- Cybersecurity
- Detection
- Disasters
- Government
- Infrastructure
- International
- Public health
- Public Safety
- Communication interoperabillity
- Emergency services
- Emergency medical services
- Fire
- First response
- IEDs
- Law Enforcement
- Law Enforcement Technology
- Military technology
- Nonlethal weapons
- Nuclear weapons
- Personal protection equipment
- Police
- Notification /alert systems
- Situational awareness
- Weapons systems
- Sci-Tech
- Sector Reports
- Surveillance
- Transportation
Advertising & Marketing: advertise@newswirepubs.com
Editorial: editor@newswirepubs.com
General: info@newswirepubs.com
2010-2011 © News Wire Publications, LLC News Wire Publications, LLC
220 Old Country Road | Suite 200 | Mineola | New York | 11501
Permissions and Policies
Editorial: editor@newswirepubs.com
General: info@newswirepubs.com
2010-2011 © News Wire Publications, LLC News Wire Publications, LLC
220 Old Country Road | Suite 200 | Mineola | New York | 11501
Permissions and Policies
