-
Asteroids are harder to destroy than previously thought
A popular theme in the movies is that of an incoming asteroid that could extinguish life on the planet, and our heroes are launched into space to blow it up. But incoming asteroids may be harder to break than scientists previously thought, finds a new study that used a new understanding of rock fracture and a new computer modeling method to simulate asteroid collisions.
-
-
Protect confidential information from cyberattacks
The NSF is funding research aiming to develop new guidelines for sharing secret information through wireless communication that would improve security for users and minimizes cost.
-
-
New periodic table of droplets could help in solving crimes
Liquid droplets assume complex shapes and behave in different ways, each with a distinct resonance – like a drum head or a violin string – depending on the intricate interrelationship of the liquid, the solid it lands on and the gas surrounding it. Researchers have created a periodic table of droplet motions, inspired in part by parallels between the symmetries of atomic orbitals. Better understanding of droplets behavior may help solve crimes.
-
-
Robots help in the demanding Fukushima cleanup efforts
In 2011, a tsunami triggered by a magnitude 9.0 earthquake all but decimated the Pacific Coast of Tohoku, Japan, including the Fukushima Daiichi power plant. A catastrophic meltdown ensued. Many tons of nuclear fuel, boiled down to a radioactive lava, corroded the steel surrounding the facility’s three reactors. Today, the cleanup effort is still projected to take several decades. S&T and NIST developed standard test methods for robots, which the Japanese government is now beginning to apply directly to their Fukushima cleanup efforts.
-
-
Better monitoring of nuclear power plants, nuclear proliferation
The United Kingdom is investing nearly £10 million (about $12.7 million) in a joint project with the United States to harness existing particle physics research techniques to remotely monitor nuclear reactors. Expected to be operational in 2024, the Advanced Instrumentation Testbed (AIT) project’s 6,500-ton detector will measure the harmless subatomic particles called antineutrinos that are emitted by an existing nuclear power plant 25 kilometers, or about 15.5 miles, away.
-
-
Long-distance earthquake detection
In traditional seismology, researchers studying how the earth moves in the moments before, during, and after an earthquake rely on sensors that cost tens of thousands of dollars to make and install underground. Now researchers have figured out a way to overcome these hurdles by turning parts of a 13,000-mile-long testbed of “dark fiber,” unused fiber-optic cable, owned by the DOE Energy Sciences Network (ESnet), into a highly sensitive seismic activity sensor that could potentially augment the performance of earthquake early warning systems currently being developed in the western United States.
-
-
L.A. showcases quake alert system
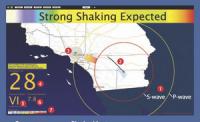
California is earthquake country, and residents of Los Angeles can now get some critical warning, when conditions are right, after a quake has started and seismic waves are heading their way. The long-delayed system, called ShakeAlertLA, is the first of its kind in the United States.
-
-
700,000 submunitions demilitarized by Sandia-designed robotics system

More than 700,000 Multiple Launch Rocket System submunitions have been demilitarized since the Army started using an automated nine-robot system conceptualized, built and programmed by Sandia Lab engineers. The automated system was built for the Army’s demilitarization program that aims to dismantle obsolete ammunition and missiles.
-
-
Marine organisms as detectors of enemy undersea activity
Goliath grouper, black sea bass, and snapping shrimp, along with bioluminescent plankton and other microorganisms, are set to be the unlikely additions to protecting U.S. assets. Researchers are developing new types of sensor systems that detect and record the behaviors of these marine organisms and interpret them to identify, characterize, and report on the presence of manned and unmanned underwater vehicles operating in strategic waters. The incorporation of biological signals will extend the range, lifetime, and performance of undersea surveillance technologies in strategic waters.
-
-
Putting data privacy in the hands of users
In today’s world of cloud computing, users of mobile apps and web services store personal data on remote data center servers. Services often aggregate multiple users’ data across servers to gain insights on, say, consumer shopping patterns to help recommend new items to specific users, or may share data with advertisers. Traditionally, however, users haven’t had the power to restrict how their data are processed and shared. New platform acts as a gatekeeper to ensure web services adhere to a user’s custom data restrictions.
-
-
Developing a system to identify, patch software security holes
DARPA is funding research of security vulnerabilities in web software. A new system called GAMEPLAY (for Graph Analysis for Mechanized Exploit-generation and vulnerability Patching Leveraging human Assistance for improved Yield) will spot security weaknesses in the millions – sometimes billions – of lines of code that run websites including banking and online shopping which are attractive to hackers.
-
-
Paradigm shift needed for making bridges tsunami-resistant

Over the past fifteen years, big earthquakes whose epicenters were in the ocean off the coasts of Japan and Indonesia have caused tsunamis that killed more than 250,000 people and caused more than $200 billion in damage. The damage includes washing away or otherwise dislodging hundreds of bridges, emphasizing the need to better understand the wave impacts’ underlying physics. Researchers argue in a new study that a paradigm shift is needed for assessing bridges’ tsunami risk.
-
-
Russia, China threaten U.S. space dominance: Pentagon
The Defense Intelligence Agency (DIA), the Pentagon’s lead intelligence agency, has warned that Russia and China are building technologies which will soon threaten U.S. dominance in space. Both countries “are developing a variety of means to exploit perceived U.S. reliance on space-based systems and challenge the U.S. position in space,” the report said. Russian doctrine “involves employing ground, air, and space-based systems to target an adversary’s satellites, with attacks ranging from temporary jamming or sensor blinding to destruction of enemy spacecraft and supporting infrastructure,” the report said.
-
-
Artificial Intelligence to make life harder for hackers
As the volume of digital information in corporate networks continues to grow, so grows the number of cyberattacks, and their cost. One cybersecurity vendor, Juniper Networks, estimates that the cost of data breaches worldwide will reach $2.1 trillion in 2019, roughly four times the cost of breaches in 2015. Now, computer scientists have developed a tool that could make it harder for hackers to find their way into networks where they don’t belong.
-
-
Under-road heating system to keep Europe’s highways ice-free
Snow and ice can dramatically change the conditions of a road, where slippery surfaces make it harder to keep control of a vehicle, particularly when braking or turning. Under-road heating that melts ice and snow within 15 minutes and real-time information about icy road conditions could help prevent wintertime accidents.
-
More headlines
The long view
New Technology is Keeping the Skies Safe
DHS S&T Baggage, Cargo, and People Screening (BCP) Program develops state-of-the-art screening solutions to help secure airspace, communities, and borders
Factories First: Winning the Drone War Before It Starts
Wars are won by factories before they are won on the battlefield,Martin C. Feldmann writes, noting that the United States lacks the manufacturing depth for the coming drone age. Rectifying this situation “will take far more than procurement tweaks,” Feldmann writes. “It demands a national-level, wartime-scale industrial mobilization.”
How Artificial General Intelligence Could Affect the Rise and Fall of Nations
Visions for potential AGI futures: A new report from RAND aims to stimulate thinking among policymakers about possible impacts of the development of artificial general intelligence (AGI) on geopolitics and the world order.
Keeping the Lights on with Nuclear Waste: Radiochemistry Transforms Nuclear Waste into Strategic Materials
How UNLV radiochemistry is pioneering the future of energy in the Southwest by salvaging strategic materials from nuclear dumps –and making it safe.
Model Predicts Long-Term Effects of Nuclear Waste on Underground Disposal Systems
The simulations matched results from an underground lab experiment in Switzerland, suggesting modeling could be used to validate the safety of nuclear disposal sites.
