-
Administration tries to harness Silicon Valley’s talent for fight against ISIS
Senior administration intelligence officials are meeting today (Friday) with Silicon Valley’s major technology firms — companies including Facebook, Twitter, Apple, Microsoft, YouTube , LinkedIn, Dropbox, and others — in an effort to recruit them and their technological know-how in the fight against radicalization and terrorism.
-
-
Extreme weather increasingly threatening U.S. power grid
Power outages related to weather take out between $18 billion to $33 billion from the nation’s economy. Analysis of industry data found that these storms are a growing threat to, and the leading cause of outages in, the U.S. electric grid. The past decade saw power outages related to bad weather increase, which means that power companies must find a way address this problem.
-
-
U.S. to impose new sanctions on Iran over ballistic missile program

The United States is preparing a new round of economic sanctions against Iran after Iran had violated agreements related to its ballistic missile program by testing, on 10 October, an advanced version of one of its missiles. The ballistic missile agreement is unrelated to the nuclear agreement the P5+1 powers signed with Iran last summer. The nuclear program-related sanctions would begin to be lifted in 2016 if Iran fully complies with the requirements of the nuclear deal.
-
-
Calls for tighter regulations of the design of toy guns

The death of people – often children – who carry BB or pellet guns resembling real weapons has prompted lawmakers and activists to call for tighter regulations on the design of non-lethal guns. California has already passed such a law, and it would go into effect on Friday.
-
-
As storms continue to batter U.K., estimates of cost rise

As Storm Frank – which is following on the heels of Storms Eva and Desmond — continues to batter England, Scotland, and Wales, estimates of the cost of the damage wrought continue to rise. The total economic loss caused by the three Storms may well breach £3 billion – and these projections do not include any government spending on flood defenses, estimated to be between £2.3 billion and £2.8 billion.
-
-
U.K.: Economic costs from flooding could reach £1.5bn, reduce GDP growth

Economic losses caused by the flooding which has devastated parts of Britain in the past few days could exceed 1.5 billion pounds, and shave 0.2-0.3 percent off GDP growth overall in the first quarter of 2016. Insurers will likely shoulder the bulk of the burden after first Storm Desmond and then Storm Eva saw waters swamp large swathes of the country.
-
-
Climate change losses for Southeast Asia well above previous estimate: ADB
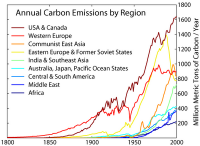
Economic losses from the impacts of climate change in Southeast Asia could be 60 percent higher than previously estimated, reducing the region’s gross domestic product (GDP) by up to 11 percent by 2100, according to a new Asian Development Bank (ADB) study. The analysis is an update to a 2009 ADB report that estimated a 7 percent annual reduction in economic output due to climate change.
-
-
Growing risks in flood-prone areas due to economic growth more than climate change
Worldwide economic losses from river flooding could increase 20-fold by the end of the twenty-first century if no further actions on flood risk reduction are taken. There are two contributors to risks associated with river flooding. Floods’ frequency and severity (both influenced by climate change); and the exposure to floods of people and economic assets (determined by economic activity and human residency in flood-prone areas). Researchers calculate that in many flood-prone regions of the world, more than 70 percent of the increase in flood-related risks over the coming decades can be attributed to economic growth and residency patterns in flood prone areas.
-
-
Iranian hackers attacked New York dam

In 2013, Iranian government hackers infiltrated the control system of Bowman Avenue Dam in Rye, New York, located twenty-five miles from New York City. Using a cellular modem, the hackers could have released larger volumes of upstream water without warning. As dams go, the Rye dam is small at about 20ft tall. There was some confusion initially, as DHS and DOE thought a similarly named dam in Oregon — the Arthur R. Bowman Dam – was the one hacked. The Oregon dam, at 245 feet, is much bigger, and hacking its control systems could have had much more serious consequences.
-
-
U.S. reliance on nonfuel mineral imports increasing
Key nonfuel mineral commodities that support the U.S. economy and national security are increasingly being sourced from outside the U.S., according to a new U.S. Geological Survey report. Over the past sixty years, there has been an increase in the number and diversity of nonfuel commodities that the United States imports as well as the extent to which the United States is import reliant.
-
-
Terrorists used encrypted apps to plan, coordinate Paris attacks
The leaders of U.S. and European law enforcement and intelligence agencies have been explicit in their warnings: commercially available communication devices equipped with end-to-end encryption software make it impossible for security services to track terrorists plotting an attack – or monitor the terrorists’ communication while the attack is under way. Sources close to the investigation of the 13 November Paris terrorist attacks have now confirmed that the terrorists used the encrypted WhatsApp and Telegram messengers apps to communicate for a period before the attacks – and with each other during the attacks. What was said in those encrypted messages, and who sent and received these messages, may never be known, because the companies themselves do not have the key – or back door – to decrypt these messages. Thus, security services could not monitor such messages before an attack in order to prevent it, and cannot read these message after an attack to learn more about the terrorists’ network and support system.
-
-
Recovering rare earth elements from coal mining waste

West Virginia could become one of the country’s significant sources for rare earth elements (REE), the “vitamins of modern industry,” without the expense or environmental cost of opening new mines. A new project brings together academia, state regulators, and industry to collaborate on finding a successful recovery technology for total REEs from acid mine drainage, or AMD. In Pennsylvania and West Virginia alone, it is estimated that AMD generates more than 45,000 tons of total REEs per year or about three times the current U.S. demand for total REEs.
-
-
The economic impact of refugees in Sweden
The world currently has more refugees and internally displaced persons than it has had since the Second World War. Many countries are reluctant to take refugees in. Security is a recent concern, but a major underlying reason is the perceived financial burden which would result from larger intake of refugees. But what, in reality, is the economic impact of these new arrivals? Since 2005, Sweden has taken in more refugees per capita than any other European country. A detailed study of the Swedish case shows that the acceptance of those refugees has resulted in a net fiscal redistribution from the non-refugee population to refugees corresponding to 1.0 percent of Swedish GDP – with four-fifths of the redistribution due to lower public per capita revenues from refugees. A clear takeaway from this research is that policies should focus on integrating refugees into the labor market as quickly as possible.
-
-
U.S. facing looming grain failures

Across the United States, record quantities of corn and soybeans have been harvested in recent years. However, according to new research, this trend may soon change. “By midcentury,” the interdisciplinary team reports, “temperatures in Illinois will likely be closer to those of today’s mid-South, and precipitation will range somewhere between that of today’s East Texas and that of the Carolinas.” In the face of a rapidly changing climate, the researchers call for a U.S. Midwest field research network to address crucial agricultural challenges.
-
-
Improving active shooter response
When an active shooter strikes, every second counts. The sooner law enforcement can respond and the more information they have, the more lives can be saved. Battelle’s SiteGuard Active Shooter Response (ASR) provides a high tech, integrated approach to help protect building occupants in an active shooter event. The ASRcombines gunshot sensors with building security and communication systems to provide critical information to law enforcement and building occupants. As soon as the sensors detect a gunshot, SiteGuard ASR activates a series of predetermined actions and automated responses vital to occupant and first responder safety and optimized response.
-
More headlines
The long view
Factories First: Winning the Drone War Before It Starts
Wars are won by factories before they are won on the battlefield,Martin C. Feldmann writes, noting that the United States lacks the manufacturing depth for the coming drone age. Rectifying this situation “will take far more than procurement tweaks,” Feldmann writes. “It demands a national-level, wartime-scale industrial mobilization.”
Trump Is Fast-Tracking New Coal Mines — Even When They Don’t Make Economic Sense
In Appalachian Tennessee, mines shut down and couldn’t pay their debts. Now a new one is opening under the guise of an “energy emergency.”
Smaller Nuclear Reactors Spark Renewed Interest in a Once-Shunned Energy Source
In the past two years, half the states have taken action to promote nuclear power, from creating nuclear task forces to integrating nuclear into long-term energy plans.
