-
Cyberattack disrupts Iran’s oil production system
The Iranian oil industrywas subject to cyber attack this past weekend,but the Iranian government saysit has contained and controlled the damage from the malware; this is the fourth known cyber attack on Iran’s civilian and military infrastructure
-
-
Better cybersecurity for the healthcare industry
Healthcare organizations face ever more threatening cyber attacks. In response, the Health Information Trust Alliance (HITRUST) has established the HITRUST Cybersecurity Incident Response and Coordination Center to provide support for the healthcare industry
-
-
Global CyberLympics Games agreement announced
Organizations announce 2-year agreement to conduct the CyberLympics Games, a series of global cyber games held on six continents and aiming to raise awareness of information security and unifying global cyber defense
-
-
Closing digital security gaps
Two European research centers, one German the other from Luxemburg, have recently agreed on a mutual course for the strategic development of new and integrative approaches to addressing key IT security concerns
-
-
Feds recruit companies to aid in cyberdefense
The U.S. national security community is intensifying its efforts to enlist the aid of the private security sector in bolstering the U.S. cyberdefenses
-
-
Companies hiring hackers to harden defenses

To burglar-proof your home, it is best hire a burglar as a consultant, as he is more likely to find the security vulnerabilities and demonstrate how they can be exploited; following this approach, companies large and small are now hiring hackers to test the companies’ security system vulnerabilities and find ways to harden these systems to withstand intrusion
-
-
WWII-like message encryption now available for e-mail security
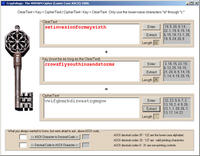
A Singapore-based company offers an e-mail encryption system based on the Verman cipher, or one-time pad, which was invented in 1917 and used by spies in the Second World War; the Vernam cipher is unbreakable because it produces completely random cipher-text that secures data so that even the most powerful super computers can not break the encryption when it is used properly
-
-
Industry insiders: insufficient security controls for smart meters
False data injection attacks exploit the configuration of power grids by introducing arbitrary errors into state variables while bypassing existing techniques for bad measurement detection; experts say current generation of smart meters are not secure enough against false data injection attacks
-
-
HPDC to publish best grid computing cybersecurity papers
In the late 1990s, as science was pushing new limits in terms of levels of computation and data and in the collaboration between scientists across universities, countries, and the globe, grid computing emerged as the model to support such large scientific collaborations by providing their computational resources and the structure behind them
-
-
2012 National Collegiate Cyber Defense Competition kicks off 20 April

The National Collegiate Cyber Defense Competition (NCCDC) is returning to the University of Texas at San Antonio (UTSA) for the seventh consecutive year; the 3-day national championship will kick off 20 April
-
-
U.S. power and water utilities face daily cyberattacks
American water and energy companies deal with a constant barrage of cyberattacks on a daily basis; these incidents usually take the form of cyber espionage or denial-of-service attacks against the utilities’ industrial-control systems
-
-
Passwords contribute to online insecurity
One percent of passwords can be cracked within ten guesses; German and Korean speakers also had passwords which were more difficult to crack, while Indonesian-speaking users’ passwords were the least secure
-
-
Cyberweapon blowback
The real concern about Stuxnet is that its existence demonstrates what is achievable; security analysts are confident that they can stop anything that is a variant of Stuxnet, but the real challenge is stopping something in the style of Stuxnet; this is where the confidence ends
-
-
zvelo reaches 100 OEM milestone
Pivotal milestone attributed to strong adoption of zvelo’s URL database, website categorization and malicious website detection solutions for a vast array of applications
-
-
Including ads in mobile apps poses privacy, security risks

Researchers have found that including ads in mobile applications (apps) poses privacy and security risks; in a recent study of 100,000 apps in the official Google Play market, researchers noticed that more than half contained so-called ad libraries, and that many of the apps included aggressive ad libraries that were enabled to download and run code from remote servers, which raises significant privacy and security concerns
-
- All
- Regional
- Water
- Biometrics
- Borders/Immig
- Business
- Cybersecurity
- Detection
- Disasters
- Government
- Infrastructure
- International
- Public health
- Public Safety
- Communication interoperabillity
- Emergency services
- Emergency medical services
- Fire
- First response
- IEDs
- Law Enforcement
- Law Enforcement Technology
- Military technology
- Nonlethal weapons
- Nuclear weapons
- Personal protection equipment
- Police
- Notification /alert systems
- Situational awareness
- Weapons systems
- Sci-Tech
- Sector Reports
- Surveillance
- Transportation
Advertising & Marketing: advertise@newswirepubs.com
Editorial: editor@newswirepubs.com
General: info@newswirepubs.com
2010-2011 © News Wire Publications, LLC News Wire Publications, LLC
220 Old Country Road | Suite 200 | Mineola | New York | 11501
Permissions and Policies
Editorial: editor@newswirepubs.com
General: info@newswirepubs.com
2010-2011 © News Wire Publications, LLC News Wire Publications, LLC
220 Old Country Road | Suite 200 | Mineola | New York | 11501
Permissions and Policies
