-
IT system allows police to predict crimes, better organize police shifts
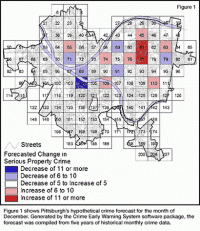
Scientists have developed an IT system based in mathematical algorithms which allows to predict how many and what type of crimes are going to be committed in the next police shift. The developer say that it is about using scientific methods for police patrolling, and that it is the first case of predictive police methods are combined with a mathematical patrolling model.
-
-
Anaheim police employed Stingray surveillance devices

Police in Anaheim, California have been using Stingray surveillance devices, as well as employing the more intrusive cousin, “dirtboxes,” during active investigations, without the knowledge of residents. More than 400 new documents obtained by the American Civil Liberties Union show that the department has requested funds for the technology, and that it has been using the devices since at least 2009.
-
-
New York City settles Muslim surveillance lawsuits

The NYPD has been agreed not to conduct surveillance based on religion, race, and ethnicity after charges that it had illegally monitoring Muslims in New York City. The city has agreed to settle two civil rights lawsuits for illegally monitoring its Muslim community following the September 11 attacks. As part of the settlement, in which the city does not admit to any wrongdoings, the city will appoint a civilian to monitor the NYPD’s counterterrorism unit.
-
-
Wi-Fi devices goldmine for investigators

Timely access to Wi-Fi devices at crime scenes could provide police with vital evidence, including placing suspects at the location. This is due to their ability to record information from mobile devices, including successful or failed attempts to log into a network, de-authentication times and MAC addresses.
-
-
Remote-controlled robot inspects suitcase bombs

Abandoned items of luggage are frequently found at airports and train stations. This is a case for the emergency services, which have to assume that these items might contain bombs. They must assess the potential threat quickly, avert any possible danger, and preserve evidence for criminal proceedings. In the future, police will have the support of a remote-controlled sensor system as they go about their duties. Researchers are developing this sensor suite in cooperation with industry partners and criminal investigation authorities.
-
-
Rail safety delays; Chicago’s trigger-happy police; killing Bangladeshi bloggers

In October the Congress agreed to extend the deadline for installing the systems to 2018, but earlier this month Congress extended the deadline for deploying speed-control systems yet again, this time until the end of 2020; By June 2016, all Chicago police officers will be equipped with non-lethal Tasers. The move is part of a plan by city authorities to curb the sharp rise in the number of people – all of them African Americans — killed by police shooting; in 2015 alone, at least four pro-democracy bloggers and a publisher were murdered while others went into hiding, or fled abroad, prompting widespread calls for protection of free speech in Bangladesh from the threat of radical Islamists.
-
-
U.S., Israel to co-develop technologies for first responders

Some $12 million will be funneled to collaborative Israeli-American projects for the development of advanced technologies for first responders over the next three years. The agreement brings together the Israeli Ministry of Public Security and the U.S. Department of Homeland Security in a drive to better equip and prepare both countries’ national rescue forces including fire, police, and first-aid units. Each side will invest equally in the project.
-
-
Terrorists used encrypted apps to plan, coordinate Paris attacks
The leaders of U.S. and European law enforcement and intelligence agencies have been explicit in their warnings: commercially available communication devices equipped with end-to-end encryption software make it impossible for security services to track terrorists plotting an attack – or monitor the terrorists’ communication while the attack is under way. Sources close to the investigation of the 13 November Paris terrorist attacks have now confirmed that the terrorists used the encrypted WhatsApp and Telegram messengers apps to communicate for a period before the attacks – and with each other during the attacks. What was said in those encrypted messages, and who sent and received these messages, may never be known, because the companies themselves do not have the key – or back door – to decrypt these messages. Thus, security services could not monitor such messages before an attack in order to prevent it, and cannot read these message after an attack to learn more about the terrorists’ network and support system.
-
-
Examining how law enforcement leaders feel about body cameras
The use of force and police behavior continue to be a prominent topic in the media. Several recent high-profile incidents involving police use of deadly force have resulted in increased scrutiny of officer behavior and police-community relations by the media, policy-makers, civil rights groups, and academics, leading to nationwide interest in police-worn body cameras to increase transparency and accountability. While the use of body-worn cameras on police to address these issues has been endorsed by the media, government, social activists, and policy makers alike, there is scant scientific evidence to support or refute the perceived benefits or drawbacks.
-
-
FBI unable to break 109 encrypted messages Texas terror attack suspect sent ahead of attack

FBI director James Comey told lawmakers this week that one of the suspects in the foiled terror attack in Garland, Texas, in May had exchanged 109 messages with sources in a “terrorist location” overseas ahead of the attack. U.S. intelligence and law enforcement agencies, however, have not been able to break into and read those messages because they were exchanged on devices equipped with end-to-end encryption software which, security services in the United States and Europe argue, make it impossible to monitor and track terrorists and criminals.
-
-
New lie-detecting software uses real court case data
By studying videos from high-stakes court cases, University of Michigan researchers are building unique lie-detecting software based on real-world data. Their prototype considers both the speaker’s words and gestures, and unlike a polygraph, it does not need to touch the subject in order to work. In experiments, it was up to 75 percent accurate in identifying who was being deceptive (as defined by trial outcomes), compared with humans’ scores of just more than 50 percent.
-
-
Matching bullets to wounds using organ-specific protein signatures found on projectiles
Forensic medicine has long employed molecular biology to link, for instance, tiny amounts of organic material to a suspect. Yet, such methods are less useful when it comes to finding out which shot or stab wound was the cause of death. They enable a weapon to be linked to the victim, but not the projectile to the wound. Researchers have developed a method which enables them more accurately to reconstruct crimes involving sharp blades or firearms.
-
-
Fibers from natural fats make bulletproof vests stronger and greener
Bulletproof vests and other super-strong materials could soon become even tougher and more environmentally friendly at the same time with the help of extra firm, or “al dente,” fibers. These materials, which are powerful enough to stop speeding bullets, can also be used for many other tasks that require strength.
-
-
Civil liberties coalition condemns cybersecurity bill

Civil libertarians in the United States have a new ally in the fight against the new surveillance bill now being considered in Congress: librarians. The critics of the bill call it both “unhelpful” and “dangerous to Americans’ civil liberties.” House speaker Paul Ryan (R-Wisconsin) has been actively pushing for reconciliation of two bills, the Protecting Cyber Networks Act (PCNA) and the National Cybersecurity Protection Advancement with the Cybersecurity Information Sharing Act of 2015 (CISA), which passed a Senate vote in October.
-
-
Paris attacks expose weaknesses in Europe’s security structure

The 13 November attacks in Paris offered a painful demonstration of Europe’s security loopholes which the terrorists exploited to their advantage. The attacks should serve as a wake-up call to Europeans that the continental security structure, built in another era, is no longer sufficient and needs to be adapted to new circumstances. Whether or not such adaptations can be made, and made in time before the terrorists decide to launch another attack, is an open question.
-
- All
- Regional
- Water
- Biometrics
- Borders/Immig
- Business
- Cybersecurity
- Detection
- Disasters
- Government
- Infrastructure
- International
- Public health
- Public Safety
- Communication interoperabillity
- Emergency services
- Emergency medical services
- Fire
- First response
- IEDs
- Law Enforcement
- Law Enforcement Technology
- Military technology
- Nonlethal weapons
- Nuclear weapons
- Personal protection equipment
- Police
- Notification /alert systems
- Situational awareness
- Weapons systems
- Sci-Tech
- Sector Reports
- Surveillance
- Transportation
Advertising & Marketing: advertise@newswirepubs.com
Editorial: editor@newswirepubs.com
General: info@newswirepubs.com
2010-2011 © News Wire Publications, LLC News Wire Publications, LLC
220 Old Country Road | Suite 200 | Mineola | New York | 11501
Permissions and Policies
Editorial: editor@newswirepubs.com
General: info@newswirepubs.com
2010-2011 © News Wire Publications, LLC News Wire Publications, LLC
220 Old Country Road | Suite 200 | Mineola | New York | 11501
Permissions and Policies
