-
Applications solicited for funding of next-gen first-response technologies
DHS Science and Technology Directorate (S&T) says that applications are now being accepted through 9 March 2016 for the NextGen First Responder Technologies solicitation, an opportunity for joint-funding by DHS S&T and their partners in the Israeli Ministry of Public Security.
-
-
Forensic botany uses plant DNA to trace crimes

Researchers are advancing the field of forensic botany with the publication of two recent studies that use marijuana DNA to link drug supplies and pollen DNA to aid in forensic investigations.
-
-
In FBI versus Apple, government strengthened tech’s hand on privacy
The ongoing fight between Apple and the FBI over breaking into the iPhone maker’s encryption system to access a person’s data is becoming an increasingly challenging legal issue. This case is very specific, and in this narrow case, Apple and law enforcement agencies will likely find a compromise. However, this question is not going away anywhere. With the “Internet of things” touted as the next big revolution, more and more devices will capture our very personal data – including our conversations. This case could be a precedent-setting event that can reshape how our data are stored and managed in the future.
-
-
Suicide bomb detector moves close to commercialization with Sandia engineer’s help
On the chilling list of terrorist tactics, suicide bombing is at the top. Between 1981 and 2015, an estimated 5,000 such attacks occurred in more than 40 countries, killing about 50,000 people. The global rate grew from three a year in the 1980s to one a month in the 1990s to one a week from 2001 to 2003 to one a day from 2003 to 2015. R3 Technologies and a group of other small businesses are developing a way to prevent suicide attacks by detecting concealed bombs before they go off. R3 found a partner in Sandia sensor expert JR Russell who has helped bring the company’s Concealed Bomb Detector, or CBD-1000, close to commercialization over the past two years.
-
-
Fast, lightweight autonomous air vehicle completes first flight data tests
DARPA’s Fast Lightweight Autonomy (FLA) technologies could be useful in addressing a pressing surveillance shortfall. Military teams patrolling dangerous overseas urban environments, and rescue teams responding to disasters such as earthquakes or floods, currently can use remotely piloted unmanned aerial vehicles (UAVs) to provide a bird’s-eye view of the situation, but to know what is going on inside an unstable building or a threatening indoor space often requires physical entry, which can put troops or civilian response teams in danger.
-
-
More Americans support Justice Dept. than Apple in locked iPhone dispute
As the standoff between the Department of Justice and Apple Inc. continues over an iPhone used by one of the suspects in the San Bernardino terrorist attacks, 51 percent say Apple should unlock the iPhone to assist the ongoing FBI investigation. Fewer Americans (38 percent) say Apple should not unlock the phone to ensure the security of its other users’ information; 11 percent do not offer an opinion on the question.
-
-
Passwords, privacy and protection: can Apple meet FBI’s demand without creating a ‘backdoor’?
The point of encryption is to make decryption hard. However, hard does not mean impossible. The FBI could decrypt this data, with sufficient effort and computational power, and they could do this with no help from Apple. However, this route would be expensive, and would take some time. In effect, what they’re requesting of Apple is to make their job easier, cheaper and faster. Ultimately, how this matter gets resolved may depend more on the big-picture question of what privacy rights we as a society want for the data we record on our personal devices. Understanding the technical questions can inform this discussion.
-
-
Snowden ready to return to U.S. for “fair trial”
Edward Snowden has told friends and supporters he was ready to return to the United States if he could be guaranteed a fair trial. Snowden said his representatives had approached the U.S. Justice Department in an effort to negotiate a plea deal, even one involving him spending time in jail. He told the BBC Panorama last year, however, that the Justice Department had made no effort to respond.
-
-
Forensics close in on footwear analysis

First it was your fingerprint that gave the game away and then DNA analysis transformed forensic science. But “watch your step” because experts have developed a new technique which could lead to a step change in forensic footwear imaging. The experts have been able to extract additional information and create a digital picture of the personal footprint we leave behind when we stand or walk on a hard surface.
-
-
NYPD has used Stingrays since 2008 -- with lower-level court orders rather than warrants
The NYPD has confirmed that it owns and operates Stingrays— surveillance devices that spy on cell phones nearby and which can be used to track location. In response to an NYCLU FOIL request, the NYPD disclosed it used Stingrays nearly 1,016 times between 2008 and May of 2015 without a written policy and following a practice of obtaining only lower-level court orders rather than warrants. This is the first time the extent of the use of Stingrays by the NYPD has been made public.
-
-
Helping local law enforcement to share data
DHS Science and Technology Directorate’s (S&T) First Responders Group’s (FRG) Video Datacasting Project transmits encrypted live video and data over existing broadcast television signals to a targeted audience within public safety. Users can download data in the field, improving interoperability at minimal cost and effort in the furtherance of public safety.
-
-
Intelligence agencies could use Internet-of-things to spy on people
James Clapper, the director of U.S. national intelligence, told lawmakers the other day that the Internet of things — baby monitors, TV set, home security devices, voice recognition dolls – may be used by intelligence services to spy on people. Clapper, testifying yesterday before a Senate panel, said that intelligence agencies might be able to use this new generation of household devices to increase their surveillance capabilities.
-
-
Brennan Center sues DHS, DOJ to make “Countering Violent Extremism” records public

The Brennan Center for Justice at NYU School of Law last week sued DHS and the Department of Justice under the Freedom of Information Act (FOIA) for records pertaining to an inter-agency initiative known as “Countering Violent Extremism” (CVE). The CVE initiative is designed to identify and preempt Americans from becoming involved in “violent extremism” and is being implemented in Muslim communities in several parts of the country, including the three formally designated pilot cities of Los Angeles, Boston, and Minneapolis-St. Paul.
-
-
IT system allows police to predict crimes, better organize police shifts
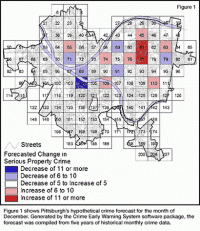
Scientists have developed an IT system based in mathematical algorithms which allows to predict how many and what type of crimes are going to be committed in the next police shift. The developer say that it is about using scientific methods for police patrolling, and that it is the first case of predictive police methods are combined with a mathematical patrolling model.
-
-
Anaheim police employed Stingray surveillance devices

Police in Anaheim, California have been using Stingray surveillance devices, as well as employing the more intrusive cousin, “dirtboxes,” during active investigations, without the knowledge of residents. More than 400 new documents obtained by the American Civil Liberties Union show that the department has requested funds for the technology, and that it has been using the devices since at least 2009.
-
- All
- Regional
- Water
- Biometrics
- Borders/Immig
- Business
- Cybersecurity
- Detection
- Disasters
- Government
- Infrastructure
- International
- Public health
- Public Safety
- Communication interoperabillity
- Emergency services
- Emergency medical services
- Fire
- First response
- IEDs
- Law Enforcement
- Law Enforcement Technology
- Military technology
- Nonlethal weapons
- Nuclear weapons
- Personal protection equipment
- Police
- Notification /alert systems
- Situational awareness
- Weapons systems
- Sci-Tech
- Sector Reports
- Surveillance
- Transportation
Advertising & Marketing: advertise@newswirepubs.com
Editorial: editor@newswirepubs.com
General: info@newswirepubs.com
2010-2011 © News Wire Publications, LLC News Wire Publications, LLC
220 Old Country Road | Suite 200 | Mineola | New York | 11501
Permissions and Policies
Editorial: editor@newswirepubs.com
General: info@newswirepubs.com
2010-2011 © News Wire Publications, LLC News Wire Publications, LLC
220 Old Country Road | Suite 200 | Mineola | New York | 11501
Permissions and Policies
