-
NIST’s regional approach to addressing U.S. cybersecurity challenge
NIST has awarded grants totaling nearly $1 million for five projects that are taking a community approach to addressing the U.S. shortage of skilled cybersecurity employees. The NIST-led National Initiative for Cybersecurity Education (NICE), a partnership among government, academia, and the private sector, will oversee the grants as part of its mission to support cybersecurity education, training, and workforce development.
-
-
North Korea has only has 28 Web sites, mistakenly leaked official data reveals
Launching an effective cyberwar against North Korea would be difficult because the secretive country has only twenty-eight registered domains. The information about the surprisingly small number of North Korean registered domains was the result of incorrect configuration of one of North Korea’s top-level name servers. The incorrect configuration made the server reveal a list of all the domain names under the domain .kp.
-
-
Setting up a decoy network to help deflect a hacker's hits
Computer networks may never float like a butterfly, but information scientists suggest that creating nimble networks that can sense jabs from hackers could help deflect the stinging blows of those attacks. The researchers created a computer defense system that senses possible malicious probes of the network and then redirects that attack to a virtual network that offers little information about the real network.
-
-
A chip that checks for sabotage, flags defects
With the outsourcing of microchip design and fabrication a worldwide, $350 billion business, bad actors along the supply chain have many opportunities to install malicious circuitry in chips. These Trojan horses look harmless but can allow attackers to sabotage healthcare devices; public infrastructure; and financial, military, or government electronics. Researchers are developing a unique solution: a chip with both an embedded module that proves that its calculations are correct and an external module that validates the first module’s proofs.
-
-
DHS S&T awards $1.3 million to small businesses for cybersecurity R&D
DHS S&T has awarded $1.3 million to thirteen small businesses for the development of new cyber security technology. Each business was awarded approximately $100,000 in preliminary funding through the DHS S&T Small Business Innovation Research (SBIR) program. The SBIR proposal solicitation, released in December 2015, included four topics developed by Cyber Security Division program managers.
-
-
“Our president should be chosen by American citizens, not by foreign adversaries or interests”
Thirty-one members of the Aspen Institute Homeland Security Group, a bipartisan group of homeland security and counterterrorism experts, last week have issued a statement on the recent Democratic National Committee (DNC) hack. “[T]his is an attack not on one party but on the integrity of American democracy. And it may not be the end of such attacks. It is not unthinkable that those responsible will steal and release more files, and even salt the files they release with plausible forgeries,” members of the group write. “This is unacceptable. Our president should be chosen by American citizens, not by foreign adversaries or interests.”
-
-
U.S. to issue new policy directive for coordinated government response to cyberattacks
The administration is set to release a new directive on how the government should respond to significant cyberattacks. The release of the directives aims to clarify the responsibilities of agencies involved in security breaches. The presidential directive comes against the backdrop of an increasing number of cyberattacks by criminals and foreign governments.
-
-
Automated cybersecurity systems get set for final face-off at DARPA’s Cyber Grand Challenge
The Heartbleed security bug existed in many of the world’s computer systems for nearly two-and-a-half years before it was discovered and a fix circulated in the spring of 2014. The reason for this time lag? In contrast to the sophistication and automation that characterize so much of today’s computer systems, the process of finding and countering bugs, hacks, and other cyber infection vectors is still effectively artisanal. But what if that system of finding and fixing flaws were just as fast and automated as the computer systems they are trying to protect? What if cyber defense were as seamless, sophisticated, and scalable as the Internet itself? These are questions at the heart of DARPA’s Cyber Grand Challenge.
-
-
How to stay anonymous online
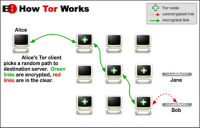
Anonymity networks protect people living under repressive regimes from surveillance of their Internet use. But the recent discovery of vulnerabilities in the most popular of these networks — Tor — has prompted computer scientists to try to come up with more secure anonymity schemes. These scientists have developed a new anonymity scheme that provides strong security guarantees but uses bandwidth much more efficiently than its predecessors, making it possible for network to protect users’ anonymity if all but one of its servers are compromised.
-
-
DHS S&T funds efforts to make Internet of Things safer
DHS S&T the other day awarded $119,000 to Ionic Security, Inc. based in Atlanta, Georgia, to advance detection and monitoring for Internet of Things (IoT) systems security. The Ionic Security team proposes to apply a novel distributed data protection model to solve the authentication, detection, and confidentiality challenges that impact distributed IoT devices.
-
-
DHS S&T awards Charles River Analytics $500,000 for predictive malware defense research

Malicious cyber activity is growing at an unprecedented rate. A leading internet security firm reported there were more than 317 million new malicious code signatures in 2014. Additionally, attacks are increasing in sophistication as authors create malware that circumvents standard signature-based antivirus defense systems. DHS S&T has awarded $500,000 to Cambridge, Massachusetts-based Charles River Analytics to develop malware defense technology that will alert and empower information technology (IT) administrators to fend off an impending cyberattack.
-
-
Intelligence agencies spy on our data by manipulating computer chips
Researchers work to develop mechanisms that will render the Internet of Things more secure. They focus on a specific security gap: the manipulation of computer chips, that is, hardware components. These components can be found not only in PCs and laptops, but also in all other devices with integrated electronics; those include credit cards, cars, and smartphones, as well as large industrial facilities and medical equipment.
-
-
Nation’s elite cybersecurity talent participate in U.S. Cyber Challenge program

A week from today, Illinois’ top cybersecurity talent will descend upon Moraine Valley Community College outside of Chicago to participate in the annual U.S. Cyber Challenge (USCC) Cyber Camp. During the week-long camp, individuals will participate in a variety of classes that cover such subjects as packet crafting and pen testing, and compete in a virtual Capture the Flag competition to demonstrate their cybersecurity abilities in a free-form environment in hopes of winning one of the limited (ISC)2 scholarship vouchers.
-
-
NIST to refine Cybersecurity Framework after comments from stakeholders
NIST is developing a minor update of its Cybersecurity Framework based on feedback from its users. In the just-released Cybersecurity Framework Feedback: What We Heard and Next Steps, NIST is announcing that a draft of the update will be published for comment in early 2017.
-
-
Closing security gaps in the Internet of Things
Cars, fridges, household appliances – in the future, many everyday items will be online. This opens up numerous new targets for attacks. IT experts are developing protection mechanisms. The experts are developing a new method for detecting and fixing vulnerabilities in the applications run on different devices — regardless of the processor integrated in the respective device.
-
More headlines
The long view
Confronting Core Problems in Cybersecurity
It’s common for governors and mayors to declare a state of emergency and activate the National Guard in the aftermath of hurricanes, tornadoes, and other natural disasters. But last month, officials in Minnesota took these steps in the wake of a major cyberattack on the city of St. Paul —a testament to how disruptive these attacks have become.
Voting from Your Sofa Is Secure Enough – but Will It Be Allowed?
A new electronic voting system developed at NTNU can withstand attacks from quantum computers, meaning digital elections can be conducted securely, even in the future.
