-
Pro-ISIS hackers issue threats to Facebook, Twitter founders
Pro-ISIS hackers have released a video threatening the founders of Facebook and Twitter in retaliation for the two social media giants’ campaign to take down ISIS-related accounts. The threat was issued in a 25-minute video, uploaded on Tuesday to social networks by a group calling itself “Sons Caliphate Army” – which experts say is the latest “rebrand” of ISIS’s supporters online.
-
-
Do-it-yourself encryption
Sending e-mails is easy. However, until now a lot of know-how has been required to securely encrypt them. This is bound to change: Deutsche Telekom and the Fraunhofer Institute for Secure Information Technology (SIT) in Darmstadt will be making encryption easy — with a popular encryption named Volksverschlüsselung. The Volksverschlüsselung software provides the required keys and configures the existing e-mail programs for the users to be able to encrypt and decrypt.
-
-
Cybersecurity “Rosetta Stone” marks two years of success
Two years ago this month, the National Institute of Standards and Technology (NIST) released a document designed to help strengthen cybersecurity at organizations that manage critical national infrastructure such as banking and the energy supply. Produced after a year of intensive collaboration with industry, the Cybersecurity Framework is now a tool used by a wide variety of public and private companies and organizations, from retail chains to state governments.
-
-
More Americans support Justice Dept. than Apple in locked iPhone dispute
As the standoff between the Department of Justice and Apple Inc. continues over an iPhone used by one of the suspects in the San Bernardino terrorist attacks, 51 percent say Apple should unlock the iPhone to assist the ongoing FBI investigation. Fewer Americans (38 percent) say Apple should not unlock the phone to ensure the security of its other users’ information; 11 percent do not offer an opinion on the question.
-
-
Passwords, privacy and protection: can Apple meet FBI’s demand without creating a ‘backdoor’?
The point of encryption is to make decryption hard. However, hard does not mean impossible. The FBI could decrypt this data, with sufficient effort and computational power, and they could do this with no help from Apple. However, this route would be expensive, and would take some time. In effect, what they’re requesting of Apple is to make their job easier, cheaper and faster. Ultimately, how this matter gets resolved may depend more on the big-picture question of what privacy rights we as a society want for the data we record on our personal devices. Understanding the technical questions can inform this discussion.
-
-
How mobile ads leak personal data
The personal information of millions of smartphone users is at risk due to in-app advertising that can leak potentially sensitive user information between ad networks and mobile app developers, according to a new study.
-
-
Detecting hidden malicious ads hidden in apps
The danger of acquiring a computer virus or spyware used to come with the risk of visiting the dark, sketchy corners of the Internet. But now trusted and harmless smartphone apps like MyFitnessPal and Candy Crush carry their own risks. As more and more people own smartphones, the number of malicious ads hidden in apps is growing — tripling in just the past year.
-
-
Sharing password data safely to bolster cybersecurity
An unfortunate reality for cybersecurity researchers is that real-world data for their research too often comes via a security breach. Now computer scientists have devised a way to let organizations share statistics about their users’ passwords without putting those same customers at risk of being hacked.
-
-
Apple refuses to comply with court order to help FBI investigate San Bernardino terrorists
Apple’s encryption technology has placed the company at the heart t of the privacy vs national security debate, as the company said it would defy a court order which requires to company to help investigate the San Bernardino attack by helping the FBI crack the code of an iPhone , Syed Rizwan Farook, one of terrorists, used. The U.S. government, stunned by Apple’s refusal to help in investigating a terrorist attack on U.S. soil, persuaded a court to issue on order compelling Apple to cooperate in the investigation.
-
-
Cybercrime’s true toll

Cyber thieves who steal credit and debit card numbers are making millions of dollars in profits, fueling a global criminal enterprise marked by the high-profile data breaches of major companies such as Target and Home Depot. A criminologist offers one of the first scientific studies to estimate cybercrime profits, saying the findings should be a wakeup call for consumers and law enforcement officials alike.
-
-
Russian govt. behind attack on Ukraine power grid: U.S. officials
Obama officials said that Russian hackers were behind a December 2015 cyberattack on Ukraine’s power grid. The attack caused power outages and blackouts in 103 cities and towns across Ukraine. Elizabeth Sherwood-Randall, deputy Energy Secretary, made the comments to a gathering of electric power grid industry executives.
-
-
Encryption prevents FBI from cracking San Bernardino attackers’ phone
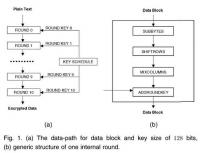
U.S. law enforcement agencies have been unable to access a telephone used by the two Islamist attackers in the San Bernardino shooting, FBI director James Comey said Tuesday. Comey stressed that the post-Snowden end-to-end encryption some technology companies are now offering their customers make it impossible for law enforcement to learn more about terrorists and criminal networks, even after terrorist or criminal acts have been committed and even if a court has approved access to the information.
-
-
Intelligence agencies could use Internet-of-things to spy on people
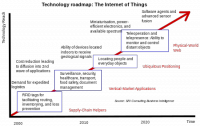
James Clapper, the director of U.S. national intelligence, told lawmakers the other day that the Internet of things — baby monitors, TV set, home security devices, voice recognition dolls – may be used by intelligence services to spy on people. Clapper, testifying yesterday before a Senate panel, said that intelligence agencies might be able to use this new generation of household devices to increase their surveillance capabilities.
-
-
U.S. officials: DHS, DOJ hack not serious
Informed U.S. officials have downplayed the impact of the latest breach of government data in the wake of a hack of the employee information of 29,000 Department of Justice and DHS staff. Unidentified hackers on Sunday claimed that they had stolen personal information of about 20,000 DoJ employees — including FBI officials — and 9,000 DHS employees. Observers note that while the DHS breach is less severe than the one at OPM, it is still embarrassing for a department designated as the point of entry for all corporate data shared with government agencies in the information sharing program between industry and government created last year by the Cybersecurity Information Sharing Act.
-
-
Vulnerability found in in two-factor authentication

Two-factor authentication is a computer security measure used by major online service providers to protect the identify of users in the event of a password loss. Security experts have long endorsed two-factor authentication as an effective safeguard against password attacks. But what if two-factor authentication could be cracked not by computer engineering but by social engineering?
-
More headlines
The long view
Researchers Develop AI Agent That Solves Cybersecurity Challenges Autonomously
New framework called EnIGMA demonstrates improved performance in automated vulnerability detection using interactive tools.
