-
Secure, user-controlled data
Most people with smartphones use a range of applications that collect personal information and store it on Internet-connected servers — and from their desktop or laptop computers, they connect to Web services that do the same. Some use still other Internet-connected devices, such as thermostats or fitness monitors, that also store personal data online. Generally, users have no idea which data items their apps are collecting, where they’re stored, and whether they’re stored securely. Cryptographic system would allow users to decide which applications access which aspects of their data.
-
-
WhatsApp to add encryption to voice chats

Reports say that WhatsApp is planning to add encrypted video chats to its app in order to make it impossible for, so that nobody could snoop on its users. Adding encrypted voice chats will mean that all of the messages that pass through WhatsApp will be secure. Text messages are already encrypted.
-
-
Snowden dismisses FBI's claim it cannot unlock San Bernardino killers’ iPhone

Edward Snowden has joined the debate over the FBI’s attempt to force Apple to help it unlock the iPhone 5C used by one of the San Bernardino terrorists. The FBI says that only Apple can deactivate certain passcode protections on the iPhone — for example, the 10-attempt limit, which makes the phone permanently inaccessible after ten attempts to guess the password —which would allow law enforcement to guess the passcode by using brute-force.
-
-
Calif. terrorists’ iPhone may have been used to introduce malware into data networks: DA

San Bernardino County District Attorney Michael Ramos has advanced what experts describe as an unusual reason for forcing Apple to allow the FBI to break the password of the iPhone used by the two terrorists as part of the agency’s investigation of the attack. Ramos says the phone might have been “used as a weapon” to introduce malicious software to county computer systems.
-
-
French law would penalize encrypted phone makers who refuse to help police probes
French lawmakers on Thursday voted for a measure which would impose penalties on manufacturers of smartphone who refuse to cooperate with law enforcement in inquiries of terrorism cases. The measure stipulates that a private manufacturer of smartphones, which refuses to hand over encrypted data to an investigating authority, would face up to five years in jail and a 350,000 euro ($380,000) fine.
-
-
Three “twisted” photons in 3 dimensions for quantum encryption
Researchers have achieved a new milestone in quantum physics: they were able to entangle three particles of light in a high-dimensional quantum property related to the “twist” of their wave-front structure. Multi-photon entangled states such as these have applications ranging from quantum computing to quantum encryption. Along these lines, the authors of this study have developed a new type of quantum cryptographic protocol using their state that allows different layers of information to be shared asymmetrically among multiple parties with unconditional security.
-
-
FBI cannot force Apple to unlock iPhone in drug case: Judge
Magistrate Judge James Orenstein in Brooklyn on Monday ruled that the U.S. government cannot force Apple to unlock an iPhone in a New York drug case. The ruling strengthens the company’s arguments in its landmark legal confrontation with the Justice Department over encryption and privacy. The government sought access to the drug dealer’s phone months before a California judge ordered Apple to give access to the San Bernardino terrorist’s handset.
-
-
Do-it-yourself encryption
Sending e-mails is easy. However, until now a lot of know-how has been required to securely encrypt them. This is bound to change: Deutsche Telekom and the Fraunhofer Institute for Secure Information Technology (SIT) in Darmstadt will be making encryption easy — with a popular encryption named Volksverschlüsselung. The Volksverschlüsselung software provides the required keys and configures the existing e-mail programs for the users to be able to encrypt and decrypt.
-
-
More Americans support Justice Dept. than Apple in locked iPhone dispute
As the standoff between the Department of Justice and Apple Inc. continues over an iPhone used by one of the suspects in the San Bernardino terrorist attacks, 51 percent say Apple should unlock the iPhone to assist the ongoing FBI investigation. Fewer Americans (38 percent) say Apple should not unlock the phone to ensure the security of its other users’ information; 11 percent do not offer an opinion on the question.
-
-
Passwords, privacy and protection: can Apple meet FBI’s demand without creating a ‘backdoor’?
The point of encryption is to make decryption hard. However, hard does not mean impossible. The FBI could decrypt this data, with sufficient effort and computational power, and they could do this with no help from Apple. However, this route would be expensive, and would take some time. In effect, what they’re requesting of Apple is to make their job easier, cheaper and faster. Ultimately, how this matter gets resolved may depend more on the big-picture question of what privacy rights we as a society want for the data we record on our personal devices. Understanding the technical questions can inform this discussion.
-
-
Sharing password data safely to bolster cybersecurity
An unfortunate reality for cybersecurity researchers is that real-world data for their research too often comes via a security breach. Now computer scientists have devised a way to let organizations share statistics about their users’ passwords without putting those same customers at risk of being hacked.
-
-
Apple refuses to comply with court order to help FBI investigate San Bernardino terrorists
Apple’s encryption technology has placed the company at the heart t of the privacy vs national security debate, as the company said it would defy a court order which requires to company to help investigate the San Bernardino attack by helping the FBI crack the code of an iPhone , Syed Rizwan Farook, one of terrorists, used. The U.S. government, stunned by Apple’s refusal to help in investigating a terrorist attack on U.S. soil, persuaded a court to issue on order compelling Apple to cooperate in the investigation.
-
-
Encryption prevents FBI from cracking San Bernardino attackers’ phone
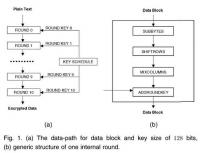
U.S. law enforcement agencies have been unable to access a telephone used by the two Islamist attackers in the San Bernardino shooting, FBI director James Comey said Tuesday. Comey stressed that the post-Snowden end-to-end encryption some technology companies are now offering their customers make it impossible for law enforcement to learn more about terrorists and criminal networks, even after terrorist or criminal acts have been committed and even if a court has approved access to the information.
-
-
Reframing the encryption debate
A new report examines the high-profile debate around government access to encryption, and offers a new perspective gleaned from the discussion, debate, and analyses of an exceptional and diverse group of security and policy experts from academia, civil society, and the U.S. intelligence community. The report takes issue with the usual framing of the encryption debate and offers context and insights that widen the scope of the conversation more accurately to reflect the surveillance landscape both now and in the future.
-
-
World leaders urged to oppose encryption back doors
In an open letter made public on Monday, nearly 200 Internet and digital rights leaders and experts, companies, and organizations are calling on the Obama administration and other world leaders to reject efforts to create “back doors” to encryption. “Encryption tools, technologies, and services are essential to protect against harm and to shield our digital infrastructure and personal communications from unauthorized access,” the letter states.
-
- All
- Regional
- Water
- Biometrics
- Borders/Immig
- Business
- Cybersecurity
- Detection
- Disasters
- Government
- Infrastructure
- International
- Public health
- Public Safety
- Communication interoperabillity
- Emergency services
- Emergency medical services
- Fire
- First response
- IEDs
- Law Enforcement
- Law Enforcement Technology
- Military technology
- Nonlethal weapons
- Nuclear weapons
- Personal protection equipment
- Police
- Notification /alert systems
- Situational awareness
- Weapons systems
- Sci-Tech
- Sector Reports
- Surveillance
- Transportation
Advertising & Marketing: advertise@newswirepubs.com
Editorial: editor@newswirepubs.com
General: info@newswirepubs.com
2010-2011 © News Wire Publications, LLC News Wire Publications, LLC
220 Old Country Road | Suite 200 | Mineola | New York | 11501
Permissions and Policies
Editorial: editor@newswirepubs.com
General: info@newswirepubs.com
2010-2011 © News Wire Publications, LLC News Wire Publications, LLC
220 Old Country Road | Suite 200 | Mineola | New York | 11501
Permissions and Policies
