-
Images, codes offer alternative to multiple device password systems
A system using images and a one-time numerical code could provide a secure and easy to use alternative to multi-factor methods dependent on hardware or software and one-time passwords. The developers of the system believe their new multi-level authentication system GOTPass could be effective in protecting personal online information from hackers. It could also be easier for users to remember, and be less expensive for providers to implement since it would not require the deployment of potentially costly hardware systems.
-
-
Terrorists used encrypted apps to plan, coordinate Paris attacks
The leaders of U.S. and European law enforcement and intelligence agencies have been explicit in their warnings: commercially available communication devices equipped with end-to-end encryption software make it impossible for security services to track terrorists plotting an attack – or monitor the terrorists’ communication while the attack is under way. Sources close to the investigation of the 13 November Paris terrorist attacks have now confirmed that the terrorists used the encrypted WhatsApp and Telegram messengers apps to communicate for a period before the attacks – and with each other during the attacks. What was said in those encrypted messages, and who sent and received these messages, may never be known, because the companies themselves do not have the key – or back door – to decrypt these messages. Thus, security services could not monitor such messages before an attack in order to prevent it, and cannot read these message after an attack to learn more about the terrorists’ network and support system.
-
-
DHS questioned over pressure it put on a library to disable Tor node
Back in September, Kilton Public Library in Lebanon, New Hampshire briefly disabled its Tor relay after local police, following a tip from agents with Homeland Security’s investigations branch that the network may be used by criminals or terrorists. A Congresswoman from California wants to know why DHS officials pressured the New Hampshire library to take down the relay node, and whether DHS has leaned on other organizations to do so.
-
-
FBI unable to break 109 encrypted messages Texas terror attack suspect sent ahead of attack

FBI director James Comey told lawmakers this week that one of the suspects in the foiled terror attack in Garland, Texas, in May had exchanged 109 messages with sources in a “terrorist location” overseas ahead of the attack. U.S. intelligence and law enforcement agencies, however, have not been able to break into and read those messages because they were exchanged on devices equipped with end-to-end encryption software which, security services in the United States and Europe argue, make it impossible to monitor and track terrorists and criminals.
-
-
Untraceable communication -- guaranteed
Anonymity networks, which sit on top of the public Internet, are designed to conceal people’s Web-browsing habits from prying eyes. The most popular of these, Tor, has been around for more than a decade and is used by millions of people every day. Recent research, however, has shown that adversaries can infer a great deal about the sources of supposedly anonymous communications by monitoring data traffic though just a few well-chosen nodes in an anonymity network. Researchers have developed a new, untraceable text-messaging system designed to thwart even the most powerful of adversaries.
-
-
Tech companies: weakening encryption would only help the bad guys
Leading technology companies — Apple, Microsoft, Google, Samsung, Twitter, Facebook, and fifty-six other technology companies — have joined forces to campaign against weakening end-to-end encryption, insisting that any weakening of encryption would be “exploited by the bad guys.” Apple’s chief executive Tim Cook recently asserted that “any backdoor is a backdoor for everyone.”
-
-
E-mail security is better than it was, but far from perfect
E-mail security helps protect some of our most sensitive data: password recovery confirmations, financial data, confidential correspondences, and more. A new report finds that e-mail security is significantly better than it was two years ago, but still has widespread issues.
-
-
Encryption firm tightens access following Paris attacks
Encrypted communications specialist Silent Circle, after learning that ISIS was recommending two of the company’s products — the encrypted Blackphone handset and Silent Phone applications for private messaging — to the organization’s followers, is taking steps to make it more difficult for terrorists and their followers to use these products.
-
-
Telegram IM app recalibrates policies after Paris attacks
Pavel Durov, the creator of the popular instant messaging app Telegram, has said that following the Paris terrorist attacks, his company has blocked dozens of accounts associated with the jihadist Islamic State group. As is the case with other technology companies, Telegram is trying to negotiate the balance between privacy and security: the same privacy-enhancing technology which keeps customers’ communication private, also helps terrorists communicate with each other and plot attacks safe from monitoring and surveillance by intelligence agencies and law enforcement.
-
-
Paris terrorist attacks reignite debate over end-to-end encryption, back doors
The exact way the terrorists who attacked France last Friday communicated with each other, and their handlers, in the run-up to the attack is not yet clear, but the attack has prompted law enforcement and intelligence agencies in Europe and the United States to renew their call to regulate the use of new encryption technologies which allow users to “go dark” and make it difficult, if not altogether impossible, to retrieve the contents of communication.
-
-
Forge-proof authentication method to revolutionize security
Scientists have discovered a way to authenticate or identify any object by generating an unbreakable ID based on atoms. The technology uses next-generation nanomaterials to enable the unique identification of any product with guaranteed security. uses atomic-scale imperfections which are impossible to clone as they comprise the unmanipulable building blocks of matter. The researchers used atomic-scale imperfections which are impossible to clone as they comprise the unmanipulable building blocks of matter.
-
-
Vulnerabilities found in use of certificates for Web security
Consumers use the Internet for banking, e-mailing, shopping, and much more nowadays. With so much personal and private information being transmitted over the Web, Internet users must be able to rely on and trust the sites they are accessing. For security purposes, Web sites use certificates to establish encrypted communications. When a site becomes compromised, its certificate should be revoked. Astudy finds that Web site administrators are providing a large number of revoked certificates, certificate authorities are not using newer processes for distributing revocations, and Web browsers are not checking whether certificates have been revoked.
-
-
Stealing encryption keys on Amazon’s Cloud servers
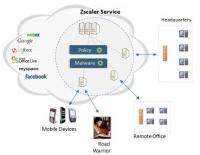
Cloud computing is a service that enables companies and organizations to store information and run computer applications without making their own investments in actual computer hardware or employing IT staff. Researchers have demonstrated that RSA encryption keys, which are used by thousands of companies and organizations to protect the data and processes they entrust to cloud-based services, can be obtained using a sophisticated side-channel attack — despite recent efforts by cloud service providers and cryptography software developers to eliminate such vulnerabilities.
-
-
White House will not seek law allowing law enforcement access to encrypted messages
The Obama administration has decided not to seek legislation which would require tech companies to design their devices in a way which would give law enforcement agencies access to individuals’ encrypted messages, the White House said on Saturday. The tech industry, led by giants Apple, Google, Facebook, IBM, and Microsoft, has mounted a vigorous campaign opposing any administration moves to weaken ever-more-sophisticated encryption systems which are designed to protect consumers’ privacy.
-
-
Supposedly encrypted national identifying numbers easily decrypted
Studies raise questions about the use of national identifying numbers by showing that Resident Registration Numbers (RRN) used in South Korea can be decrypted to reveal a host of personal information. A team of researchers in two experiments was able to decrypt more than 23,000 RRNs using both computation and logical reasoning. The findings suggest that, while such identifiers are encrypted to protect privacy, they remain vulnerable to attack and must be designed to avoid such weaknesses.
-
More headlines
The long view
Researchers Develop AI Agent That Solves Cybersecurity Challenges Autonomously
New framework called EnIGMA demonstrates improved performance in automated vulnerability detection using interactive tools.
