-
Logging in securely without passwords
Passwords are a common security measure to protect personal information, but they do not always prevent hackers from finding a way into devices. Researchers are working to perfect an easy-to-use, secure login protection that eliminates the need to use a password — known as zero-interaction authentication.
-
-
Snowden revelations spur a surge in encrypted e-mail services
The Edward Snowden revelations about National Security Agency(N.S.A) surveillance programs have fueled a surge of new e-mail encryption services. “A lot of people were upset with those revelations, and that coalesced into this effort,” said the co-developer of a new encrypted e-mail service which launched last Friday. The company notes that its servers are based in Switzerland, making it more difficult for U.S. law enforcement to reach them.
-
-
Researchers crack supposedly impregnable encryption algorithm in two hours
Without cryptography, no one would dare to type their credit card number on the Internet. Security systems developed to protect the communication privacy between the seller and the buyer are the prime targets for hackers of all kinds, hence making it necessary for encryption algorithms to be regularly strengthened. A protocol based on “discrete logarithms,” deemed as one of the candidates for the Internet’s future security systems, was decrypted by École polytechnique fédérale de Lausann (EPFL) researchers. Allegedly tamper-proof, it could only stand up to the school machines’ decryption attempts for two hours.
-
-
New algorithm revolutionizes cryptography
Researchers have solved one aspect of the discrete logarithm problem. This is considered to be one of the “holy grails” of algorithmic number theory, on which the security of many cryptographic systems used today is based. They have devised a new algorithm which calls into question the security of one variant of this problem, which has been closely studied since 1976.
-
-
NIST removes cryptography algorithm from random number generator recommendations
Following a public comment period and review, the National Institute of Standards and Technology (NIST) has removed a cryptographic algorithm from its draft guidance on random number generators. Before implementing the change, NIST is requesting final public comments on the revised document, Recommendation for Random Number Generation Using Deterministic Random Bit Generators. The revised document retains three of the four previously available options for generating pseudorandom bits needed to create secure cryptographic keys for encrypting data. It omits an algorithm known as Dual_EC_DRBG, or Dual Elliptic Curve Deterministic Random Bit Generator.
-
-
Major step toward stronger encryption technology announced
Researchers the other day announced the first successful trial of Quantum Key Distribution (QKD) technology over a live “lit” fiber network. The trial paves the way for more advanced research into QKD, the next frontier of data encryption technology, which will deliver even greater levels of network security.
-
-
Inspired by nature, researches develop “unbreakable” security codes
A revolutionary new method of encrypting confidential information has been patented by scientists who have been inspired by their discoveries from human biology, which model how the heart and lungs coordinate their rhythms by passing information between each other. A mathematical model based on the complex interaction between these organs has now been transferred to the world of modern communications.
-
-
Making quantum cryptography suitable for mobile phones
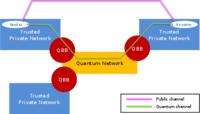
Secure mobile communications underpin our society and through mobile phones, tablets and laptops we have become online consumers. The security of mobile transactions is obscure to most people but is absolutely essential if we are to stay protected from malicious online attacks, fraud and theft. Researchers have shown how it is possible to make the resources necessary for quantum cryptography less bulky and expensive, and thus more suitable for mobile handsets.
-
-
Quantum cryptography to help us keep our secrets secret
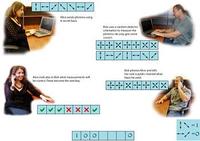
In the history of secret communication, the most brilliant efforts of code-makers have been matched time and again by the ingenuity of code-breakers. Sometimes we can even see it coming. We already know that one of today’s most widely used encryption systems, RSA, will become insecure once a quantum computer is built. An article in Nature reviewing developments in quantum cryptography describes how we can keep our secrets secret even when faced with the double challenge of mistrust and manipulation.
-
-
Quantum mechanics may lead to ultra-secure Internet
In 1935 Einstein and researchers highlighted a “spooky” theory in quantum mechanics, which is the strange way entangled particles stay connected even when separated by large distances. In the 1990s, scientists realized you can securely transmit a message through encrypting and using a shared key generated by Einstein’s strange entanglement to decode the message from the sender and receiver. Using the quantum key meant the message was completely secure from interception during transmission.
-
-
BGU startup Titanium Core wins Cybertition cyber security competition
Ben-Gurion University of the Negev startup Titanium Core won the first Jerusalem Venture Partners (JVP)-sponsored Cybertition cyber security competition. Titanium Core uses a multilayered security approach to repel attacks on mission-critical systems, provide real-time attack information, and prevent threats from moving onto other computer systems. The company will receive $1 Million investment from JVP and space in the JVP Cyber Labs incubator, located in the cyber center in Beer-Sheva, adjacent to Ben-Gurion University.
-
-
NIST seeking comments on its cryptographic standards process
As part of a review of its cryptographic standards development process, NIST said it was seeking public comment on a new draft document that describes how the agency develops those standards. In November 2013, NIST announced it would review its cryptographic standards development process after concerns were raised about the security of a cryptographic algorithm in NIST Special Publication 800-90 (2006) an its updated version, 800-90A (2007).
-
-
Facebook-WhatsApp deal raises security concerns
Facebook’s acquisition of WhatsApp made headlines for its sheer size — $4 billion in cash and $15 in Facebook stock, for a total of about $19 billion – but security experts are worried about the security aspects of the deal. Even security specialists advising WhatApp’s customers not to panic about the deal, use language which is not exactly reassuring. Serge Malenkovich of Kaspersky Labs says: “There are no new [emphasis in original] reasons to worry about messaging privacy. Honestly speaking, WhatsApp was never meant to be a true confidential messaging tool; there were even multiple breaches in the past, including some attacks, which make eavesdropping possible.”
-
-
Israeli defense company launches cybersecurity solutions section
In recent months the Israel Aerospace Industries (IAI) has increased its cyberdefense-related activities. Esti Peshin, director of the company’s cyber section and a veteran of the IDF’s hush-hush sigint Unit 8200, says IAI is now developing solutions for clients in Israel and abroad. “We’re a start-up, but with the backing of a company that earns $3.5 billion a year,” she said. Ultimately, she implied, these defensive measures can be turned into offensive capabilities. “Intelligence is a subset of attack,” Peshin said. “This is, first of all, a national mission.”
-
-
New software obfuscation system a cryptography game changer
A team of researchers has designed a system to encrypt software so that it only allows someone to use a program as intended while preventing any deciphering of the code behind it. This is known in computer science as “software obfuscation,” and it is the first time it has been accomplished. Previously developed techniques for obfuscation presented only a “speed bump,” forcing an attacker to spend some effort, perhaps a few days, trying to reverse-engineer the software. The new system puts up an “iron wall,” making it impossible for an adversary to reverse-engineer the software without solving mathematical problems that take hundreds of years to work out on today’s computers — a game-change in the field of cryptography.
-
- All
- Regional
- Water
- Biometrics
- Borders/Immig
- Business
- Cybersecurity
- Detection
- Disasters
- Government
- Infrastructure
- International
- Public health
- Public Safety
- Communication interoperabillity
- Emergency services
- Emergency medical services
- Fire
- First response
- IEDs
- Law Enforcement
- Law Enforcement Technology
- Military technology
- Nonlethal weapons
- Nuclear weapons
- Personal protection equipment
- Police
- Notification /alert systems
- Situational awareness
- Weapons systems
- Sci-Tech
- Sector Reports
- Surveillance
- Transportation
Advertising & Marketing: advertise@newswirepubs.com
Editorial: editor@newswirepubs.com
General: info@newswirepubs.com
2010-2011 © News Wire Publications, LLC News Wire Publications, LLC
220 Old Country Road | Suite 200 | Mineola | New York | 11501
Permissions and Policies
Editorial: editor@newswirepubs.com
General: info@newswirepubs.com
2010-2011 © News Wire Publications, LLC News Wire Publications, LLC
220 Old Country Road | Suite 200 | Mineola | New York | 11501
Permissions and Policies
