CybersecurityWeb security protocol TLS compromised
In one third of all servers, the security protocol TLS and encrypted data transfer can be compromised. All types of online communication that deal with sensitive data are affected. The researchers discovered the flaw by launching a DROWN (Decrypting RSA with Obsolete and Weakened eNcryption) attack – which they will demonstrate and discuss at a forthcoming security conference in Germany.
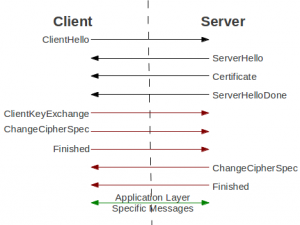
Diagram showing the steps involved in each phase of a simple server authenticated TLS session // Source: cmu.edu
In one third of all servers, the security protocol TLS and encrypted data transfer can be compromised. All types of online communication that deal with sensitive data are affected.
This has been demonstrated in a current study, to which Horst Görtz Institute for IT Security at Ruhr-Universität Bochum has significantly contributed. For their cryptographic attack, the international research team have banked on an old friend: “SSLv2” is the previous version of the current security protocol TLS and is now considered insecure. “SSLv2 is lying dormant on many servers, even though TLS has long been in use,” says Juraj Somorovsky from Horst Görtz Institute in Bochum. The old versions have been mostly replaced, but never completely deleted. A grave error, as it turns out: it creates a gate through which TLS security mechanisms can be bypassed, thus leaving user names, passwords, credit card numbers, and financial data unprotected.
Free-of-cost tactics
RUB reports that the researchers have scanned the entire https network and have found out that approximately 33 percent of all servers worldwide, that is, 11.5 million units, have been affected by their attack. A mere $440 dollars are required to carry out an attack. The researchers invested them to rent graphic cards with high computing power for their attacks in an AMAZON cloud. “Due to an implementation error, we were able to do without the additional computing power when we tried out an alternative variation of the attack,” says Somorovsky. The free-of-cost tactics still works in 26 percent of all servers worldwide.
Webpage gives information about protection
“It is possible to protect yourself from attacks of that kind,” says Somorovsky. First, Web administrators should deactivate SSLv2 protocols on their servers. In addition, the researchers launched the website www.drownattack.com on March 1, 2016, featuring important security advice. Everyone can use it to test if their own webpage is safe. The thus detected security problem is a shameful leftover: twenty years ago, the SSLv2 standard was deliberately launched as a not fully secure version due to cryptography export regulations. “We must learn from the mistakes of the past,” concludes Somorovsky. “Politically and economically independent Internet security standards are indispensable!”
RuhrSec Conference
In the last months, the team, consisting of Juraj Somorovsky, Susanne Engels, and Prof Christof Paar from Horst Görtz Institute at Ruhr-Universität Bochum, collaborated with researchers from the universities in Münster, Tel Aviv, Pennsylvania, and Michigan, and with researchers from the Hashcat project and OpenSSL. Titled DROWN (Decrypting RSA with Obsolete and Weakened eNcryption), the attack will be a key issue discussed at the der RuhrSec conference in Bochum on 29 April 2016.
