-
Metal-eating microbes are cost-effective for recycling rare earth elements
Today’s high-tech devices usually contain components made of rare earth elements (REEs), a class of metallic elements including neodymium and dysprosium. Despite this demand, and despite the fact that REEs are relatively common in the earth’s crust, REEs are difficult to obtain, and the U.S. currently does not produce a domestic supply. This scarcity of domestic REEs leaves manufacturers of everything from cellphones and computers to wind turbines and telescope lenses vulnerable to supply disruptions. have developed an economical way to recycle REEs using a bacterium called Gluconobacter oxydans.
-
-
Using artificial intelligence to predict criminal aircraft
The ability to forecast criminal activity has been explored to various lengths in science fiction, but does it hold true in reality? It could for U.S. Customs and Border Protection (CBP). ) DHS S&T is developing a Predictive Threat Model (PTM) to help CBP’s Air and Marine Operations Center (AMOC) more quickly and efficiently identify and stop nefarious aircraft.
-
-
Bioengineers today emphasize the crucial ingredient Dr. Frankenstein forgot – responsibility
Mary Shelley was 20 when she published “Frankenstein” in 1818. Two hundred years on, the book remains thrilling, challenging and relevant — especially for scientists like me whose research involves tinkering with the stuff of life. Talk of “engineering biology” makes a lot people squeamish, and technology can turn monstrous, but I read Mary Shelley’s “Frankenstein” not as an injunction against bioengineering as such. Rather, the story reveals what can happen when we – scientists and nonscientists alike – run away from the responsibilities that science and technology demand. Victor Frankenstein was certainly careless and perhaps a coward, unable to own up to the responsibility of what he was doing. We now know that science is best conducted with humility, forethought and in the light of day.
-
-
Protecting soldiers from blast-induced brain injury
Researchers have developed a new military vehicle shock absorbing device that may protect warfighters against traumatic brain injury (TBI) due to exposure to blasts caused by land mines. During Operations Iraqi Freedom and Enduring Freedom, more than 250,000 warfighters were victims of such injuries. Prior to this study, most research on blast-induced TBI has focused on the effects of rapid changes in barometric pressure, also known as overpressure, on unmounted warfighters.
-
-
U.S. firefighters and police turn to an Israeli app to save lives
When Hurricane Irma hit the Florida Keys in September 2017, the new First Response app from Israeli-American company Edgybees helped first-responders identify distress calls in flooded areas. When wildfires hit Northern California a month later, the app steered firefighters away from danger. This lifesaving augmented-reality app — designed only months before as an AR racing game for drone enthusiasts — is now used by more than a dozen fire and police departments in the United States, as well as the United Hatzalah emergency response network in Israel.
-
-
Researchers join AI-enabled robots in “collaborative autonomy”
A team of firefighters clears a building in a blazing inferno, searching rooms for people trapped inside or hotspots that must be extinguished. Except this isn’t your typical crew. Most apparent is the fact that the firefighters are not all human. They are working side-by-side with artificially intelligent (AI) robots who are searching the most dangerous rooms, and making life or death decisions. This scenario is potentially closer than you might think, but while AI-equipped robots might be technologically capable of rendering aid, sensing danger or providing protection for their flesh-and-blood counterparts, the only way they can be valuable to humans is if their operators are not burdened with the task of guiding them.
-
-
Deep Fakes: A looming crisis for national security, democracy and privacy?
Events in the last few years, such as Russia’s broad disinformation campaign to undermine Western democracies, including the American democratic system, have offered a compelling demonstration of truth decay: how false claims — even preposterous ones — can be disseminated with unprecedented effectiveness today thanks to a combination of social media ubiquitous presence and virality, cognitive biases, filter bubbles, and group polarization. Robert Chesney and Danielle Citron write in Lawfare that the resulting harms are significant for individuals, businesses, and democracy – but that the problem may soon take a significant turn for the worse thanks to deep fakes. They urge us to get used to hearing that phrase. “It refers to digital manipulation of sound, images, or video to impersonate someone or make it appear that a person did something—and to do so in a manner that is increasingly realistic, to the point that the unaided observer cannot detect the fake. Think of it as a destructive variation of the Turing test: imitation designed to mislead and deceive rather than to emulate and iterate.”
-
-
Analytical methods to help develop antidotes for cyanide, mustard gas
Several Food and Drug Administration-approved antidotes are available for cyanide poisoning, but they have severe limitations. To develop effective antidotes for chemical agents, such as cyanide and mustard gas, scientists need analytical methods that track not only the level of exposure but also how the drug counteracts the effects of the chemical.
-
-
Real-time Captcha technique bolsters biometric authentication
A new login authentication approach could improve the security of current biometric techniques that rely on video or images of users’ faces. Known as Real-Time Captcha, the technique uses a unique challenge that’s easy for humans — but difficult for attackers who may be using machine learning and image generation software to spoof legitimate users.
-
-
Energy-efficient encryption for the internet of things
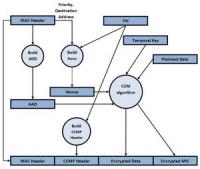
Most sensitive web transactions are protected by public-key cryptography, a type of encryption that lets computers share information securely without first agreeing on a secret encryption key. Public-key encryption protocols are complicated, and in computer networks, they’re executed by software. But that won’t work in the internet of things, an envisioned network that would connect many different sensors — embedded in vehicles, appliances, civil structures, manufacturing equipment, and even livestock tags — to online servers. Embedded sensors that need to maximize battery life can’t afford the energy and memory space that software execution of encryption protocols would require. Special-purpose chip reduces power consumption of public-key encryption by 99.75 percent, increases speed 500-fold.
-
-
Spotting IEDs from a safe distance
Landmines, improvised explosive devices (IEDs), and other homemade bombs struck 6,461 people worldwide in 2015, killing at least 1,672. Survivors are often left with devastating injuries. In a study published in BMJ Open, 70 percent of people hit by IEDS in Afghanistan required multiple amputations. These homemade bombs are often hidden—nestled in bushes, buried underground, or sometimes stuffed inside other objects. To keep soldiers away from these deadly weapons, researchers are developing technology that can spot explosive hazards precisely and from a safe distance.
-
-
A quantum leap for quantum communication
Quantum communication, which ensures absolute data security, is one of the most advanced branches of the “second quantum revolution.” In quantum communication, the participating parties can detect any attempt at eavesdropping by resorting to the fundamental principle of quantum mechanics — a measurement affects the measured quantity. Thus, the mere existence of an eavesdropper can be detected by identifying the traces that his measurements of the communication channel leave behind. The major drawback of quantum communication today is the slow speed of data transfer, which is limited by the speed at which the parties can perform quantum measurements. Researchers have devised a method that overcomes this speed limit, and enables an increase in the rate of data transfer by more than 5 orders of magnitude.
-
-
Epigenetic technology to help in fight against WMD proliferation
Intelligence officers in the field, in trying to determine the presence or use of WMDs, would benefit from being able to check the epigenetic markers of an individual who may have come into contact with WMDs, read a history of any time he has been exposed to threat agents, and start piecing together a chain of evidence right there in the field, in real time. The epigenome is biology’s record keeper. Though DNA does not change over a single lifetime, a person’s environment may leave marks on the DNA that modify how that individual’s genes are expressed. DARPA’s new Epigenetic CHaracterization and Observation (ECHO) program aims to build a field-deployable platform technology that quickly reads someone’s epigenome.
-
-
Putting statistics into forensic firearms identification
When a gun is fired, and the bullet blasts down the barrel, it encounters ridges and grooves that cause it to spin, increasing the accuracy of the shot. Those ridges dig into the soft metal of the bullet, leaving striations. At the same time that the bullet explodes forward, the cartridge case explodes backward with equal force against the mechanism that absorbs the recoil, called the breech face. This stamps an impression of the breech face into the soft metal at the base of the cartridge case, which is then ejected from the gun. Researchers have developed a statistical approach for ballistic comparisons that may enable numerical testimony – similar to a DNA expert expressing the strength of the evidence numerically when testifying about genetic evidence.
-
-
Keeping the lights on if the world turns to 100% clean, renewable energy
Researchers propose three separate ways to avoid blackouts if the world transitions all its energy to electricity or direct heat and provides the energy with 100 percent wind, water, and sunlight. The solutions reduce energy requirements, health damage, and climate damage. “Based on these results, I can more confidently state that there is no technical or economic barrier to transitioning the entire world to 100 percent clean, renewable energy with a stable electric grid at low cost,” says one researcher.
-
More headlines
The long view
Autonomous Vehicle Technology Vulnerable to Road Object Spoofing and Vanishing Attacks
Researchers have demonstrated the potentially hazardous vulnerabilities associated with the technology called LiDAR, or Light Detection and Ranging, many autonomous vehicles use to navigate streets, roads and highways. The researchers have shown how to use lasers to fool LiDAR into “seeing” objects that are not present and missing those that are – deficiencies that can cause unwarranted and unsafe braking or collisions.
Tantalizing Method to Study Cyberdeterrence
Tantalus is unlike most war games because it is experimental instead of experiential — the immersive game differs by overlapping scientific rigor and quantitative assessment methods with the experimental sciences, and experimental war gaming provides insightful data for real-world cyberattacks.
Prototype Self-Service Screening System Unveiled
TSA and DHS S&T unveiled a prototype checkpoint technology, the self-service screening system, at Harry Reid International Airport (LAS) in Las Vegas, NV. The aim is to provide a near self-sufficient passenger screening process while enabling passengers to directly receive on-person alarm information and allow for the passenger self-resolution of those alarms.
Falling Space Debris: How High Is the Risk I'll Get Hit?
An International Space Station battery fell back to Earth and, luckily, splashed down harmlessly in the Atlantic. Should we have worried? Space debris reenters our atmosphere every week.
Testing Cutting-Edge Counter-Drone Technology
Drones have many positive applications, bad actors can use them for nefarious purposes. Two recent field demonstrations brought government, academia, and industry together to evaluate innovative counter-unmanned aircraft systems.
Strengthening the Grid’s ‘Backbone’ with Hydropower
Argonne-led studies investigate how hydropower could help add more clean energy to the grid, how it generates value as grids add more renewable energy, and how liner technology can improve hydropower efficiency.
The Tech Apocalypse Panic is Driven by AI Boosters, Military Tacticians, and Movies
From popular films like a War Games or The Terminator to a U.S. State Department-commissioned report on the security risk of weaponized AI, there has been a tremendous amount of hand wringing and nervousness about how so-called artificial intelligence might end up destroying the world. There is one easy way to avoid a lot of this and prevent a self-inflicted doomsday: don’t give computers the capability to launch devastating weapons.
The Tech Apocalypse Panic is Driven by AI Boosters, Military Tacticians, and Movies
From popular films like a War Games or The Terminator to a U.S. State Department-commissioned report on the security risk of weaponized AI, there has been a tremendous amount of hand wringing and nervousness about how so-called artificial intelligence might end up destroying the world. There is one easy way to avoid a lot of this and prevent a self-inflicted doomsday: don’t give computers the capability to launch devastating weapons.
