-
W.Va. residents still wary about their drinking water
The January 2014 chemical spill in West Virginia, which contaminated the drinking water of 300,000 residents, has changed how residents use public water. Authorities claimed the water was safe for consumption on 13 January, since MCHM levels had dropped below a federal safety threshold of one part per million. Residents remain skeptical, with some collecting rain water, and other relying on clean water distributed by non-profits.
-
-
Lead ammunition should be replaced by steel in shooting sports: experts
Researchers say that Olympic athletes specializing in shooting use one thousand cartridges per week and scatter some 1.3 tons of lead yearly, with harmful effects for surrounding animals and agricultural land. The researchers urge the International Olympic Committee and other sports organizations to replace lead ammunition with steel, which is non-toxic and contains similar technical characteristics.
-
-
U.S. corporations aware of current, future water risks
A new survey shows that nearly 60 percent of responding companies — the majority Fortune 500 and publically traded, representing virtually every industry sector — indicated that water is poised negatively to affect business growth and profitability within five years, while more than 80 percent said it will affect their decision on where to locate facilities. This is a stark increase from only five years ago, when water issues affected business growth and profitability for less than 20 percent of responding companies.
-
-
House mulls Syria-related sanctions on Iran

U.S. House legislators are considering new terrorism-related sanctions on Iran, targeting the country’s support for Hezbollah, after ceding to the Obama administration’s request to back off on sanctions related to Iran’s nuclear program. The House Foreign Affairs Committee hopes the move will reflect their independence from the White House and also bring more focus to the Syrian crisis.Lawmakers say the bill would reflect the most effective ways to disrupt Iran’s financial support of Hezbollah.
-
-
Global insured losses from catastrophes were $45 billion in 2013
Total economic losses from natural catastrophes and man-made disasters were $140 billion in 2013. Global insured losses were around $45 billion in 2013, with large contributions from flooding and hail events. The economic losses of $140 billion were down from $196 billion in 2012, and below the 10-year average of $190 billion. Around 26,000 lives were lost in natural catastrophes and man-made disasters in 2013.
-
-
The costs of using wind energy, natural gas for electricity virtually equal
The costs of using wind energy and natural gas for electricity are virtually equal when accounting for the full private and social costs of each, making wind a competitive energy source for the United States, according to a new study on the federal tax credit for wind energy. The analysis shows that wind energy comes within .35 cents per kWh when levelized over the 20-year life of a typical wind contract, compared on an equivalent basis to the full costs for natural gas-fired energy.
-
-
Cryptolocker has you between a back-up and a hard place
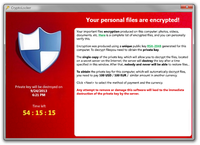
Cryptolocker, a particularly vicious form of malware that first appeared in September 2013, is a game-changer. After getting into your computer, it will encrypt all your data files, from your word documents to your photos, videos, and PDFs. It will then ask for a ransom of around $300 or 0.5 bitcoins to get them back. It has been one of the most commented developments in computer security circles in recent times, and copycats are appearing. The criminals are netting tens or hundreds of millions in ransoms, and at least some of the ill-gotten gains secured from Cryptolocker are likely to be reinvested. The criminals behind it will likely pay for access to bigger botnets to reach a wider base of victims. Future versions of the virus will in all likelihood be more prevalent and will extend across other platforms, like smartphones and tablets.
-
-
Russia leads, U.S. lags in construction of nuclear power reactors around the world
Has a new cold war developed between Russian and the United States in the twenty-first century? Many argue that it has — but with a more unconventional front of commercial nuclear energy contracts with developing countries. Russian companies are building 37 percent of new nuclear reactors around the world; U.S. companies build only 7 percent of new nuclear facilities.
-
-
Delaware launches cyber initiative
Delaware is joining the number of states that have decided to invest in a statewide cybersecurity workforce to combat the growing threat of cyberattacks directed at both private and public institutions.Delaware hopes its cyber initiative will accelerate current efforts to develop a stronger cyber workforce. The Delaware Cyber Initiative proposes $3 million for a collaborative learning and research network in the form of part research lab, part business park, dedicated to cyber innovation.
-
-
FDA proposes rules to prevent terror attack on U.S. food supply
Food terrorism could have drastic economic effects. A DHS risk assessment discovered that should a pathogen like foot-and-mouth disease be introduced to Great Plains ranchers, total damages would exceed $50 billion, affecting U.S. beef exports and dramatically reducing consumer demand for beef products.In order to prevent or reduce the risk from a potential terror attack on the nation’s food supply, the FDA proposed new rules to the Food Safety Modernization Act (FSMA).
-
-
Black markets for hackers increasingly sophisticated, specialized, and maturing
Black and gray markets for computer hacking tools, services and byproducts such as stolen credit card numbers continue to expand, creating an increasing threat to businesses, governments and individuals, according to a new study. One dramatic example is the December 2013 breach of retail giant Target, in which data from approximately forty million credit cards and 70 million user accounts was hijacked. Within days, that data appeared — available for purchase — on black market Web sites.
-
-
Conflicting views hamper N.C. preparation for sea level rise
Residents of North Carolina’s coastal towns are finding themselves increasingly caught in the cross-fire between local and state government regarding how to define future sea level rise resulting from global warming and the necessary measures needed to prepare for it. Due to a four-year moratorium on any action on the state level, area developers and homeowners have received no official input, and the lack of consensus has negative consequences for the health and prosperity of the region.
-
-
Controversial Mississippi power station to cut emissions by more than half

A new $5 billion state-of-the-art power facility is under construction Kemper County, Mississippi. It places a firm bet on the future of carbon-capture technology, and other technological advancements, including: it utilizes the gasification process with carbon in unique ways; it recycles treated wastewater to generate power; and it makes money from the carbon dioxide it has removed by selling it to oil companies for their own extraction. Critics say that investing so much money in untested technologies is too much of a gamble.
-
-
U.S. lags behind other countries in commercial use of drones
As the United States continues to explore regulations and safety guidelines for commercial UAVs, other countries have already adopted their use. Photographers, real estate agents, filmmakers, and news agencies in the United States want to use drones in their operations, but the FAA insists that rules addressing safety challenges associated with drones need to be in place before drones can share the sky with manned aircrafts.
-
-
Howard County, Md. attracts cybersecurity firms
Howard County, Maryland boasts a growing presence of cybersecurity firms and specialists at a time when the industry is gaining attention. The proximity of the county to government agencies has helped cybersecurity firms gain federal contracts, and the proximity of large cybersecurity consumers like the NSA offers cybersecurity firms in Howard County a large pool of cybersecurity specialists to select from when NSA employees decide to shift to the private sector.
-
More headlines
The long view
Factories First: Winning the Drone War Before It Starts
Wars are won by factories before they are won on the battlefield,Martin C. Feldmann writes, noting that the United States lacks the manufacturing depth for the coming drone age. Rectifying this situation “will take far more than procurement tweaks,” Feldmann writes. “It demands a national-level, wartime-scale industrial mobilization.”
Trump Is Fast-Tracking New Coal Mines — Even When They Don’t Make Economic Sense
In Appalachian Tennessee, mines shut down and couldn’t pay their debts. Now a new one is opening under the guise of an “energy emergency.”
Smaller Nuclear Reactors Spark Renewed Interest in a Once-Shunned Energy Source
In the past two years, half the states have taken action to promote nuclear power, from creating nuclear task forces to integrating nuclear into long-term energy plans.
