-
U.S. financial industry pushes Congress to pass cybersecurity bill
Three financial-industry trade groups have issued a letter to senior members of the Senate Select Committee on Intelligenceto re-energize a campaign for moving forward with cybersecurity legislation. The trade groups, representing the U.S. largest financial institutions, said their ability to prevent cyberattacks will be hindered unless Congress acts.
-
-
Inkblots bolster security of online passwords
Computer scientists have developed a new password system that incorporates inkblots to provide an extra measure of protection when, as so often occurs, lists of passwords get stolen from websites. This new type of password, dubbed a GOTCHA (Generating panOptic Turing Tests to Tell Computers and Humans Apart), could foil growing problem of automated brute force attacks, and would be suitable for protecting high-value accounts, such as bank accounts, medical records, and other sensitive information.
-
-
Weakening cybersecurity to facilitate NSA surveillance is dangerous: experts
In the wake of revelations about the NSA surveillance programs, an expert on surveillance and cybersecurity recommended a re-evaluation of those surveillance practices that weaken commercial products and services. These practices include weakening standards and placing “back doors” into products that are accessible to U.S. government agencies. The expert – Jon Peha, former chief technology officer of the FCC and assistant director of the White House’s Office of Science and Technology — said deliberately weakening commercial products and services may make it easier for U.S. intelligence agencies to conduct surveillance, but “this strategy also inevitably makes it easier for criminals, terrorists and foreign powers to infiltrate these systems for their own purposes.”
-
-
DHS struggling to respond to cybersecurity threats: IG
A recent reportby DHS inspector general (IG) has documented the agency’s struggle to respond to cybersecurity threats and its inability to disseminate information about threats because of technical, funding, and staffing challenges.
-
-
U.S. tech companies could go “dark” to regain trust
With each new revelation of the scope of the American National Security Agency’s spying, perceptions of the importance of privacy are hardening around the world. There is thus a motivation for major technology companies to provide a verifiably secure means of allowing users to communicate securely without an ability for the companies to provide access to security agencies, even if requested to. Two companies, Silent Circle and Lavabit, have come together to form the Dark Mail alliance in an attempt to do exactly this.
-
-
Backlash: growing interest in counter-surveillance tools
The revelations about the NSA surveillance programs has prompted what some see as high-tech civil disobedience: a growing number of products and applications aiming to limit the NSA’s ability to access encrypted e-mails, obtain phone records, and listen to phone conversations.
-
-
New approach enhances quantum-based secure communication
Scientists have overcome an Achilles’ heel of quantum-based secure communication systems, using a new approach that works in the real world to safeguard secrets. The research also removes a big obstacle to realizing future applications of quantum communication, including a fully functional quantum network.
-
-
Encryption is less secure than we thought
For sixty-five years, most information-theoretic analyses of cryptographic systems have made a mathematical assumption that turns out to be wrong.
-
-
Using "mathematical jigsaw puzzles" to encrypt software
Researchers have designed a system to encrypt software so that it only allows someone to use a program as intended while preventing any deciphering of the code behind it. This is known in computer science as “software obfuscation,” and it is the first time it has been accomplished. Software remains completely functional but impervious to reverse-engineering.
-
-
Quantum cryptography’s security may not be air-tight
Quantum communication systems offer the promise of virtually unbreakable encryption. Unlike classical encryption, which is used to send secure data over networks today and the security of which depends on the difficulty of solving mathematical problems like the factoring of large numbers, most quantum encryption schemes keep the encryption key separate from the data. This approach ensures that an eavesdropper with access only to the data could not decipher the key. Researchers, however, have recently demonstrated that even quantum encryption may be susceptible to hacking.
-
-
Canadian company provides software to U.S. intelligence agencies
A Canadian company has spent the last few years locking up contracts to provide security software to U.S. federal agencies such as the NSA, CIA, and FBI. The company moved from the United States to Canada because the Canadian government gives tax credits for high-tech companies coming to Canada, and Canadian government agencies help the company break into new markets by sponsoring his company in international conferences. It was in one of these conferences that he once met “some NSA folks.”
-
-
Future computers will identify users by thoughts, not passwords

Instead of typing your password, in the future you may only have to think your password, according to researchers. A new study explores the feasibility of brainwave-based computer authentication as a substitute for passwords.
-
-
A better single-photon emitter for quantum cryptography
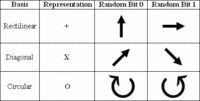
In a development that could make the advanced form of secure communications known as quantum cryptography more practical, researchers have demonstrated a simpler, more efficient single-photon emitter that can be made using traditional semiconductor processing techniques.
-
-
Fully secure communication
Can worldwide communication ever be fully secure? Quantum physicists believe they can provide secret keys using quantum cryptography via satellite. These physicists have, for the first time, successfully transmitted a secure quantum code through the atmosphere from an aircraft to a ground station.
-
-
Using jokes as an encryption method
Encrypting a message with a strong code is the only safe way to keep your communications secret, but it will be obvious to anyone seeing such a message that the sender is hiding something, regardless of whether they are encrypting their e-mails for legitimate or illicit purposes. The solution: hiding a secret message in plain sight – for example, in simple jokes.
-
- All
- Regional
- Water
- Biometrics
- Borders/Immig
- Business
- Cybersecurity
- Detection
- Disasters
- Government
- Infrastructure
- International
- Public health
- Public Safety
- Communication interoperabillity
- Emergency services
- Emergency medical services
- Fire
- First response
- IEDs
- Law Enforcement
- Law Enforcement Technology
- Military technology
- Nonlethal weapons
- Nuclear weapons
- Personal protection equipment
- Police
- Notification /alert systems
- Situational awareness
- Weapons systems
- Sci-Tech
- Sector Reports
- Surveillance
- Transportation
Advertising & Marketing: advertise@newswirepubs.com
Editorial: editor@newswirepubs.com
General: info@newswirepubs.com
2010-2011 © News Wire Publications, LLC News Wire Publications, LLC
220 Old Country Road | Suite 200 | Mineola | New York | 11501
Permissions and Policies
Editorial: editor@newswirepubs.com
General: info@newswirepubs.com
2010-2011 © News Wire Publications, LLC News Wire Publications, LLC
220 Old Country Road | Suite 200 | Mineola | New York | 11501
Permissions and Policies
