-
Beefing up public-key encryption
MIT researchers show how to secure widely used encryption schemes against attackers who have intercepted examples of successful decryption.
-
-
Grammar rules undermine security of long computer passwords
When writing or speaking, good grammar helps people make themselves understood. When used to concoct a long computer password, however, grammar — good or bad — provides important hints that can help someone crack that password, researchers at Carnegie Mellon University have demonstrated by devising grammar-aware password cracker.
-
-
Smartphones turned into secure and versatile keys
It is already possible to open doors using an app — but we are a long way from seeing widespread acceptance of this in the market; now, researchers have developed a piece of software that will make the technology even more secure and versatile
-
-
Secure communication technology overcomes lack of trust between communicating parties
Many scenarios in business and communication require that two parties share information without either being sure whether they can trust the other; examples include secure auctions and identification at ATM machines; researchers say that exploiting the strange properties of the quantum world could be the answer to dealing with such distrust
-
-
Louisiana parishes to encrypt police radio communication
First-responder agencies in Orleans, Jefferson, St. Bernard, and Plaquemines parishes in Louisiana will soon be encrypting all emergency radios, keeping emergency response chatter out of the ears of the public; the police says the encrypted communication is needed in order to keep criminals from gaining information on police by listening to scanners, but a police union and crime-prevention groups are worried that the encrypted system would prevent the media from monitoring police activity, and hobble neighborhood watch organizations from keeping their neighborhoods safe
-
-
Expert show how to crack every common password in under six hours
GPU computing has improved considerably in recent years, and Jeremi Gosney, founder and CEO of Stricture Consulting Group, used a 25-GPU cluster that can run through 350 billion guesses per second to show how easy it would be to crack practically any password out there (easy, that is, if you can use a 25-GPU cluster )
-
-
New NIST report offers guidance in cryptographic key generation
Protecting sensitive electronic information in different situations requires different types of cryptographic algorithms, but ultimately they all depend on keys, the cryptographic equivalent of a password; a new publication from the National Institute of Standards and Technology (NIST) aims to help people secure their data with good keys no matter which algorithm they choose
-
-
Quantum cryptography may soon go main stream
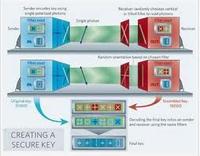
Researchers have perfected a technique that offers a less expensive way to ensure the security of high-speed fiber-optic cables, protecting communication networks from unauthorized snooping; this means that existing telecom networks can now be secured with this ultimate form of encryption
-
-
Students writing their own tickets
Four students at the University of New South Wales say they have cracked the secret algorithm used in Sydney’s public transportation system, which will allow them to print their own tickets
-
-
New solution helps thwart “smash-and-grab” credential theft
Of the data breaches investigated in 2011, servers were among the primary target assets in 64 percent of investigations and those accounted for 94 percent of compromised records; a new solution from RSA scrambles, randomizes, and splits authentication credentials across multiple servers, data centers, and the cloud
-
-
ElcomSoft, Pico Computing show world's fastest password-cracking solution
Pico Computing manufactures a range of high-end hardware acceleration platforms, offering a computational equivalent of more than 2,000 dual-core processors in a single 4U chassis; ElcomSoft updates its range of password recovery tools, employing Pico Field Programmable Gate Array (FPGA)-based hardware to accelerate the recovery of passwords
-
-
Military-grade mobile security for commercial markets
Cummings Engineering announced the release of SecureMobile 1.0, powered its proprietary SAIFE encryption technology
-
-
Yucca Mountain as a data depository

For nearly three decades, Yucca Mountain was the place designated as the country’s nuclear waste repository; after many years of study and exploration, the Obama administration, two years ago, decided not to ask for additional funds for the project; now there is another idea for the site: turning it into a giant, secure data center
-
-
Free mobile security to U.S. government agencies
A company offers its mobile security solutions, free of charge, to U.S. defense agencies; the offer is part of the NSA/CSS Co-operative Research and Development Agreement
-
-
Closing digital security gaps
Two European research centers, one German the other from Luxemburg, have recently agreed on a mutual course for the strategic development of new and integrative approaches to addressing key IT security concerns
-
- All
- Regional
- Water
- Biometrics
- Borders/Immig
- Business
- Cybersecurity
- Detection
- Disasters
- Government
- Infrastructure
- International
- Public health
- Public Safety
- Communication interoperabillity
- Emergency services
- Emergency medical services
- Fire
- First response
- IEDs
- Law Enforcement
- Law Enforcement Technology
- Military technology
- Nonlethal weapons
- Nuclear weapons
- Personal protection equipment
- Police
- Notification /alert systems
- Situational awareness
- Weapons systems
- Sci-Tech
- Sector Reports
- Surveillance
- Transportation
Advertising & Marketing: advertise@newswirepubs.com
Editorial: editor@newswirepubs.com
General: info@newswirepubs.com
2010-2011 © News Wire Publications, LLC News Wire Publications, LLC
220 Old Country Road | Suite 200 | Mineola | New York | 11501
Permissions and Policies
Editorial: editor@newswirepubs.com
General: info@newswirepubs.com
2010-2011 © News Wire Publications, LLC News Wire Publications, LLC
220 Old Country Road | Suite 200 | Mineola | New York | 11501
Permissions and Policies
