-
Telegram IM app recalibrates policies after Paris attacks
Pavel Durov, the creator of the popular instant messaging app Telegram, has said that following the Paris terrorist attacks, his company has blocked dozens of accounts associated with the jihadist Islamic State group. As is the case with other technology companies, Telegram is trying to negotiate the balance between privacy and security: the same privacy-enhancing technology which keeps customers’ communication private, also helps terrorists communicate with each other and plot attacks safe from monitoring and surveillance by intelligence agencies and law enforcement.
-
-
Paris terrorist attacks reignite debate over end-to-end encryption, back doors
The exact way the terrorists who attacked France last Friday communicated with each other, and their handlers, in the run-up to the attack is not yet clear, but the attack has prompted law enforcement and intelligence agencies in Europe and the United States to renew their call to regulate the use of new encryption technologies which allow users to “go dark” and make it difficult, if not altogether impossible, to retrieve the contents of communication.
-
-
Forge-proof authentication method to revolutionize security
Scientists have discovered a way to authenticate or identify any object by generating an unbreakable ID based on atoms. The technology uses next-generation nanomaterials to enable the unique identification of any product with guaranteed security. uses atomic-scale imperfections which are impossible to clone as they comprise the unmanipulable building blocks of matter. The researchers used atomic-scale imperfections which are impossible to clone as they comprise the unmanipulable building blocks of matter.
-
-
Iranian global cyber espionage campaign exposed
Check Point Software Technologies Ltd. on Monday published a 38-page report identifying specific details and broad analysis on cyber-espionage activity conducted by the group “Rocket Kitten,” with possible ties to Iranian Revolutionary Guard Corps. The new report also reveals details of the group’s global operations and insight into more than 1,600 of their targets.
-
-
Automated application whitelisting to prevent intrusions, malware
Automated application whitelisting regulates what software can load onto an organization’s network. It is one of a number of techniques that can help prevent malware infections, and it complements other security technologies that are part of an enterprise’s defense-in-depth resources. The National Institute of Standards and Technology (NIST) has published a guide to deploying automated application whitelisting to help thwart malicious software from gaining access to organizations’ computer systems.
-
-
DHS S&T-funded technology protects devices from cyberattacks
In 2011, a small group of university researchers working on securing embedded devices caught the attention of the Department of Homeland Security (DHS) Science and Technology Directorate (S&T). That effort has since evolved into a one-of-a-kind technology — called Symbiote — which Hewlett-Packard (HP) recently licensed from Red Balloon Security, to protect its printers from cyberattacks.
-
-
Iran Revolutionary Guard hackers target State Department’s Iran-policy personnel
Hackers working for Iran’s Revolutionary Guards have in recent weeks intensified their hacking campaign against e-mail and social media accounts of Obama administration officials. U.S. officials say they believe the cyberattacks are linked to the arrest in Tehran of an Iranian-American businessman. The cyberattacks appear to target people working on Iran policy, with many of attacks focusing on personnel in the State Department’s Office of Iranian Affairs and the Bureau of Near Eastern Affairs.
-
-
NSF highlights more than forty years of supporting cybersecurity research and education

New report highlights NSF-funded cybersecurity research and education. Today, NSF invests nearly $160 million each year in interdisciplinary research, education, and workforce development help protect national and personal security. This support helps scientists develop the tools, training, and people that will keep the nation safe and maintain online privacy.
-
-
In our Wi-Fi world, the internet still depends on undersea cables
Not many people realize that undersea cables transport nearly 100 percent of transoceanic data traffic. These lines are laid on the very bottom of the ocean floor. They’re about as thick as a garden hose and carry the world’s Internet, phone calls and even TV transmissions between continents at the speed of light. A single cable can carry tens of terabits of information per second. The cables we all rely on to send everything from e-mail to banking information across the seas remain largely unregulated and undefended. Any single cable line has been and will continue to be susceptible to disruption. And the only way around this is to build a more diverse system, because the thing that protects global information traffic is the fact that there’s some redundancy built into the system. But as things are, even though individual companies each look out for their own network, there is no economic incentive or supervisory body to ensure the global system as a whole is resilient. If there’s a vulnerability to worry about, this is it.
-
-
Protecting vehicles from cyberattacks

The Department of Homeland Security (DHS) Science and Technology Directorate (S&T) has awarded two grants for the development of technologies that can help defend government and privately owned vehicles from cyberattacks. “Modern vehicles are no longer purely mechanical systems,” said Dr. Dan Massey, S&T Cyber Physical Systems Security (CPSSEC) Program Manager. “Today’s vehicles have interdependent cyber components used for telematics, conveniences, and safety-critical systems. A stealthy adversary could gain access to a vehicle’s cyber components and remain completely hidden until initiating a widespread attack.”
-
-
Researching cyber vulnerabilities in computer-controlled cars may violate copyright law
The advent of computer controlled, Internet-capable vehicles is offering fertile new ground to hackers. Groups of “white hat” hackers have already demonstrated the vulnerabilities inherent in the new cars’ computer systems – by taking control over a car from ten miles away. One problem in addressing the issue is that the control software is proprietary, and is owned by the developers, and researching it to uncover flaws may be a violation of copyright laws.
-
-
Vulnerabilities found in use of certificates for Web security
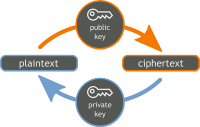
Consumers use the Internet for banking, e-mailing, shopping, and much more nowadays. With so much personal and private information being transmitted over the Web, Internet users must be able to rely on and trust the sites they are accessing. For security purposes, Web sites use certificates to establish encrypted communications. When a site becomes compromised, its certificate should be revoked. Astudy finds that Web site administrators are providing a large number of revoked certificates, certificate authorities are not using newer processes for distributing revocations, and Web browsers are not checking whether certificates have been revoked.
-
-
Stealing encryption keys on Amazon’s Cloud servers
Cloud computing is a service that enables companies and organizations to store information and run computer applications without making their own investments in actual computer hardware or employing IT staff. Researchers have demonstrated that RSA encryption keys, which are used by thousands of companies and organizations to protect the data and processes they entrust to cloud-based services, can be obtained using a sophisticated side-channel attack — despite recent efforts by cloud service providers and cryptography software developers to eliminate such vulnerabilities.
-
-
U.S. fears a Russian attack on undersea internet cables that could plunge world into chaos
It may sound far-fetched at first, but there’s a growing fear of the damage a newly aggressive Russia might inflict in a time of tension or conflict simply by damaging or cutting the undersea cables that carry almost all of the West’s Internet traffic. The perfect global cyberattack could involve severing the fiber-optic cables at some of their hardest-to-access locations in order to halt the instant communications on which the West’s governments, military, economies and citizens have grown dependent. Effectively this would cripple world commerce and communications, destabilize government business and introduce uncertainty into military operations. A significant volume of military data is routed via this Internet backbone. If Russia’s investment in information warfare is any measure we should be concerned — this investment in information warfare is not being matched by the United States and Europe combined.
-
-
Identifying students cognitively equipped to succeed in cybersecurity
The University of Maryland Center for Advanced Study of Language (CASL) will partner with the U.S. Air Force to conduct a two-year study designed to advance the cyber workforce. The Air Force says that by assessing abilities rather than knowledge, it will broaden its cyber pipeline while improving outcomes and maintaining a highly skilled workforce.
-
More headlines
The long view
Encryption Breakthrough Lays Groundwork for Privacy-Preserving AI Models
In an era where data privacy concerns loom large, a new approach in artificial intelligence (AI) could reshape how sensitive information is processed. New AI framework enables secure neural network computation without sacrificing accuracy.
Need for National Information Clearinghouse for Cybercrime Data, Categorization of Cybercrimes: Report
There is an acute need for the U.S. to address its lack of overall governance and coordination of cybercrime statistics. A new report recommends that relevant federal agencies create or designate a national information clearinghouse to draw information from multiple sources of cybercrime data and establish connections to assist in criminal investigations.
