-
Infrastructure security market to reach $32.55 billion in 2012
The global infrastructure security market, in terms of government spending, will reach a value of $32.55 billion in 2012; a new report says that spending on bolstering the cyber aspects of infrastructure security has little utility by itself unless the physical integrity of the infrastructure is also appropriately safeguarded
-
-
First successful "spoofing" of UAVs demonstrated

A research team successfully demonstrated for the first time that the GPS signals of an unmanned aerial vehicle (UAV), or drone, can be commandeered by an outside source — a discovery that could factor heavily into the implementation of a new federal mandate to allow thousands of civilian drones into the U.S. airspace by 2015
-
-
DHS FY2013 $5.75 billion IT budget request focuses on mobility, data center consolidation

DHS FY2013 IT spending requests are roughly even with FY2012 levels, with emphasis on commodity IT, mobility, and data center consolidation; the overall 2013 DHS budget request is just under $40 billion; the department’s IT budget request is just over $5.75 billion; down from $5.79 billion in FY2012
-
-
DHS awards Unisys IT services contract with a total potential value of $3 billion
Unisys among thirty companies to compete for task orders for infrastructure support and operations and maintenance services under $3 billion contract; Unisys shares were trading sharply higher Wednesday morning after the company released the news about the contract
-
-
nCircle’s new solution offers coverage for six SCADA suppliers
Critical infrastructure is designated by DHS and the North American Reliability Corporation (NERC) as the assets, systems, and networks so vital to the United States that their incapacitation or destruction would have a debilitating effect on security, national economic security, and public health or safety; nCircle offers a security solution which covers vulnerabilities from six SCADA equipment suppliers
-
-
New program to educate next generation of U.S. cybersecurity specialists

University of Maryland and Northrop Grumman create a cybersecurity honors program for undergraduates; the program, Advanced Cybersecurity Experience for Students (ACES), will immerse undergraduate students in all aspects of the field to meet growing manpower needs in the nation and the State of Maryland
-
-
Experts: Flame represents a new level of state-sponsored cyber attacks
The latest cyber espionage malware, Flame, represents a new level of sophistication in state-sponsored cyberattacks; experts note that Flame circumvented anti-virus programs, and remained undetected between two and five years; one expert says: “[Flame] uses multiple exploit combinations so it is pretty significant that it hid itself, but maybe the best ones have not been discovered yet”; another expert says: “The failure to detect Flame means simplistic signature-based detection is obsolete”
-
-
QinetiQ North America to provide cybersecurity services to DOT
QinetiQ North America (QNA) was awarded a new task order by the Volpe National Transportation Systems Center to provide cybersecurity services to protect the U.S. transportation and control systems and critical infrastructure
-
-
NSA launches cyber operations academic program
The NSA has launched National Centers of Academic Excellence (CAE) in Cyber Operations Program; the program is intended to be a deeply technical, inter-disciplinary, higher education program grounded in the computer science (CS), computer engineering (CE), or electrical engineering (EE) disciplines, with extensive opportunities for hands-on applications via labs and exercises
-
-
Malware intelligence system allow organizations to share threat information
As malware threats expand into new domains and increasingly focus on industrial espionage, researchers are launching a new tool to help battle the threats: a malware intelligence system which will help corporate and government security officials share information about the attacks they are fighting
-
-
How govt. can achieve IT savings, innovation
Innovative shifts in technology can springboard government into a new era of efficiency, effectiveness, and transparency; lawmakers urged to focus not only on technology infrastructure to achieve savings and efficiencies, but also consider how the government procures and delivers
-
-
McAfee, Intel collaborate on protecting energy infrastructure

McAfee and Intel will collaborate on improving the protection of the world’s energy utilities, including generation, transmission, and distribution, from increased cyber attacks; the two companies have provided a blueprint for a comprehensive solution of multiple products which create layers of security and operate together without great complexity or without impacting availability
-
-
Self-adapting computer network that actively defends itself against hackers
Researchers are looking into the feasibility of building a computer network that could protect itself against online attackers by automatically changing its setup and configuration; the researchers will examine whether this type of adaptive cybersecurity, called moving-target defense, can be effective – and cost-effective
-
-
Travelers’ laptops infected through fake software updates in foreign hotel rooms
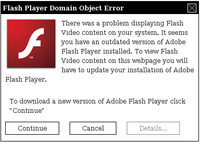
Recent analysis from the FBI and other government agencies demonstrates that malicious actors are targeting travelers abroad through pop-up windows while establishing an Internet connection in their hotel rooms
-
-
Number, diversity of targeted cyberattacks increased in 2011
The number of vulnerabilities decreased by 20 percent in 2011, but the number of malicious attacks leaped by 81 percent in the same period; targeted attacks have spread to organizations of all sizes and types
-
- All
- Regional
- Water
- Biometrics
- Borders/Immig
- Business
- Cybersecurity
- Detection
- Disasters
- Government
- Infrastructure
- International
- Public health
- Public Safety
- Communication interoperabillity
- Emergency services
- Emergency medical services
- Fire
- First response
- IEDs
- Law Enforcement
- Law Enforcement Technology
- Military technology
- Nonlethal weapons
- Nuclear weapons
- Personal protection equipment
- Police
- Notification /alert systems
- Situational awareness
- Weapons systems
- Sci-Tech
- Sector Reports
- Surveillance
- Transportation
Advertising & Marketing: advertise@newswirepubs.com
Editorial: editor@newswirepubs.com
General: info@newswirepubs.com
2010-2011 © News Wire Publications, LLC News Wire Publications, LLC
220 Old Country Road | Suite 200 | Mineola | New York | 11501
Permissions and Policies
Editorial: editor@newswirepubs.com
General: info@newswirepubs.com
2010-2011 © News Wire Publications, LLC News Wire Publications, LLC
220 Old Country Road | Suite 200 | Mineola | New York | 11501
Permissions and Policies
